The BadBox malware, a notorious Android botnet, has been disrupted by cybersecurity experts, impacting over 500,000 infected devices globally. This operation involved the removal of 24 malicious applications from Google Play and sinkholing communications of the botnet.
Overview of BadBox Malware Operations
BadBox has become a significant threat, primarily targeting low-cost Android devices, including TV streaming boxes, tablets, smart TVs, and smartphones. These devices often come pre-loaded with the malware or become infected through malicious applications and firmware updates. Once infected, these devices are turned into residential proxies, generating fake ad impressions and redirecting users to low-quality domains. This leads to fraudulent traffic distribution and enables credential stuffing attacks using the victims’ IP addresses.
“This scheme impacted more than 1 million consumer devices.”
A statement from HUMAN’s Satori Threat Intelligence team.
The botnet, now referred to as “BadBox 2.0,” has been found in devices manufactured in mainland China and shipped worldwide, with a significant number of infections reported in Brazil, the United States, Mexico, and Argentina.
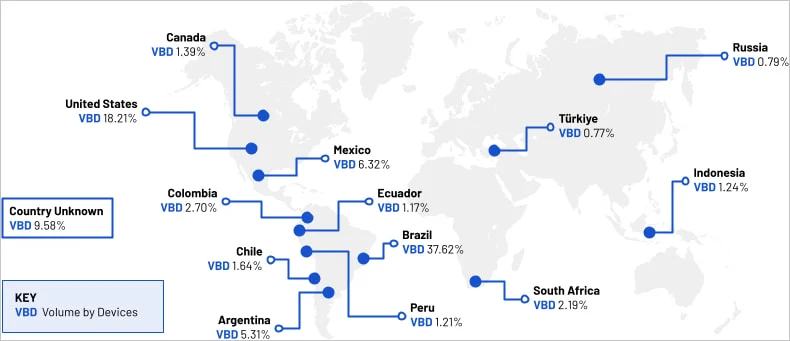
Spread of BadBox 2.0 malware
Source: HUMAN
Details of the Disruption
The latest disruption was a collaborative effort involving Google, Trend Micro, The Shadowserver Foundation, and other partners. The team identified that the botnet had expanded from its previous size and sinkholed a number of BadBox 2.0 domains. This action prevents over 500,000 infected devices from communicating with the command-and-control (C2) servers controlled by the attackers.
When a domain is sinkholed, researchers take control, enabling them to monitor connections made by infected devices. This effectively puts the malware into a dormant state, disrupting ongoing infections.
Malicious Applications Identified
The operation also uncovered 24 malicious apps on Google Play, including titles like “Earn Extra Income” and “Pregnancy Ovulation Calculator,” which had over 50,000 downloads each. Google has since removed these applications and implemented Play Protect enforcement rules to alert users and block the installation of apps associated with BadBox 2.0.
“We appreciate collaborating with HUMAN to take action against the BADBOX operation and protect consumers from fraud.”
Shailesh Saini, Google’s Director of Android Security & Privacy Engineering & Assurance, stated,
Despite these significant disruptions, the threat is far from eliminated. Google highlighted that they cannot disinfect non-Play Protect-certified Android devices sold globally. As long as consumers continue to purchase Android Open Source Project (AOSP)-based devices lacking official Google Play Services support, they remain at risk of using hardware pre-loaded with malware.
Impacted Device Models
A list of devices known to be impacted by the BadBox malware includes:
| Device Model | Device Model | Device Model | Device Model | Device Model |
|---|---|---|---|---|
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 | X96mini |
| S168 | ums512_1h10_Natv | X96_S400 | X96mini_RP | TX3mini |
| HY-001 | MX10PRO | X96mini_Plus1 | LongTV_GN7501E | Xtv77 |
| NETBOX_B68 | X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P | X96QPRO-TM |
| sp7731e_1h10_native | M8SPROW | TV008 | X96Mini_5G | Q96MAX |
| Orbsmart_TR43 | Z6 | TVBOX | Smart | KM9PRO |
| A15 | Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX | X96Q |
| isinbox | Mbox | R11 | GameBox | KM6 |
| X96Max_Plus2 | TV007 | Q9 Stick | SP7731E | H6 |
| X88 | X98K | TXCZ |
These devices, often marketed as low-cost alternatives, lack the necessary security certifications to ensure user safety.
The disruption of the BadBox malware botnet represents a significant step in the ongoing battle against cyber fraud. However, cybersecurity experts warn that the underlying issues remain, particularly concerning the proliferation of unsecure Android devices.
Excerpt: The BadBox malware disruption has impacted over 500,000 devices, revealing the urgency of addressing cybersecurity threats in low-cost Android devices.
Meta Description: Discover how BadBox malware was disrupted on over 500K infected Android devices, exposing critical vulnerabilities and the ongoing risks in cybersecurity.
Helpful Reads:









