The developers behind StealC, a known information-stealing malware, have released a significantly upgraded version featuring enhanced payload delivery, stealth mechanisms, and expanded data theft capabilities.
According to new analysis from Zscaler, version 2 of StealC has been available to threat actors since March 2025, with subsequent point updates — the latest being version 2.2.4 — adding even more functionality.
StealC Malware Evolution and Dark Web Activity
Originally launched in early 2023, StealC has been marketed on the dark web at a subscription cost of $200 per month. By 2024, the malware had been linked to widespread malvertising campaigns and attacks that locked victims into restricted kiosk modes.
Later that year, researchers confirmed ongoing development activity. StealC’s authors had introduced a method to bypass Chrome’s App-Bound Encryption, allowing the theft of expired session cookies to hijack Google accounts.
Key Enhancements in StealC Malware Version 2.x
Zscaler researchers outlined the main upgrades introduced in the version 2 series:
- Expanded payload support: StealC now delivers executable files, MSI installers, and PowerShell scripts, with flexible payload activation settings.
- Improved obfuscation and encryption:
- RC4 encryption is now used for both code strings and C2 (command-and-control) communication.
- C2 responses now include randomized parameters to reduce detection.
- Architecture improvements:
- Payloads are now compiled for 64-bit systems.
- API calls are resolved dynamically at runtime.
- A self-deletion routine has been added to cover traces post-execution.
- Embedded build system:
- Operators can now use an embedded builder to generate customized StealC builds and define targeted data theft rules.
- Operator communication:
- Real-time alerts can be delivered via Telegram bots.
- Enhanced surveillance:
- Full desktop screenshots are now supported, including on multi-monitor setups.
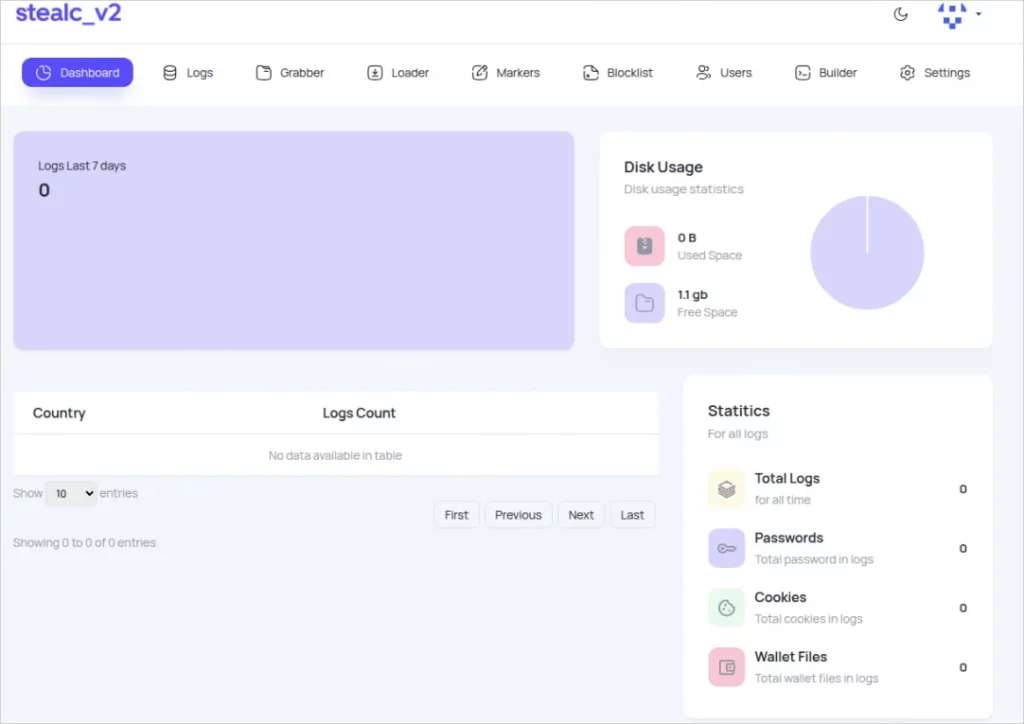
StealC v2 new admin panel
Source: Zscaler
Some features from earlier versions, such as anti-VM checks and DLL-based payload execution, have been removed. It’s unclear whether this is by design to reduce footprint or a temporary result of recent codebase changes.
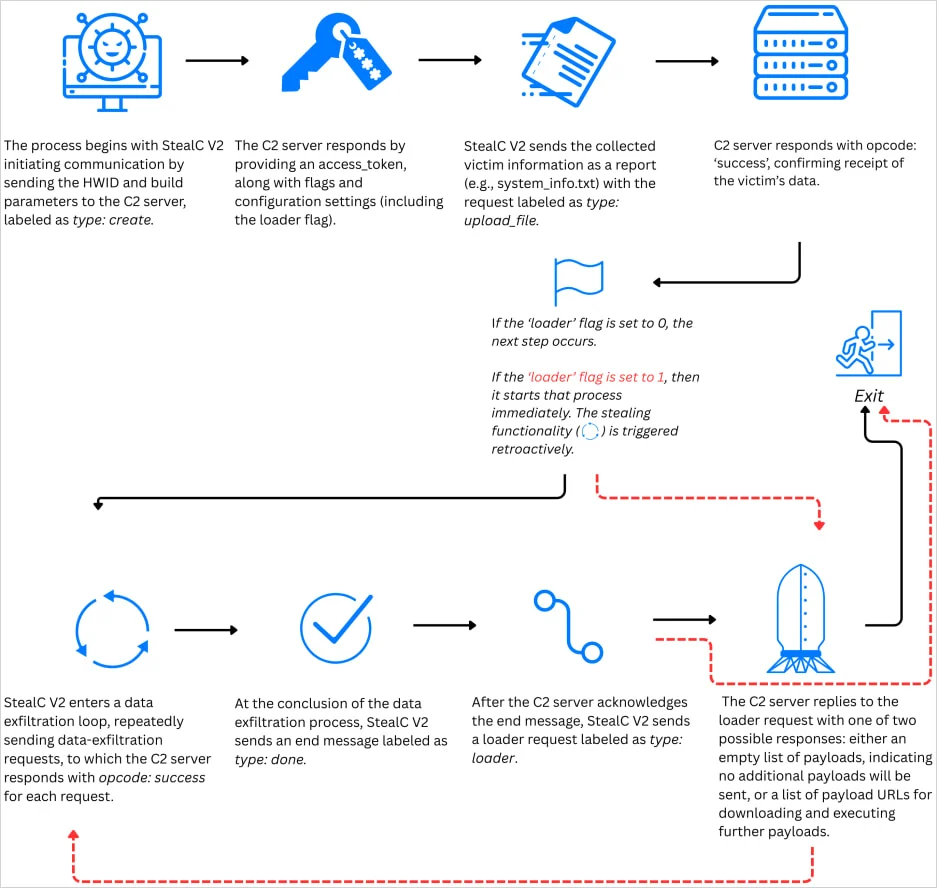
StealC’s C2 communication flow
Source: Zscaler
Active Use in Current Threat Campaigns
Zscaler observed StealC Malware being deployed using Amadey, a separate malware loader, though deployment methods could vary across different threat groups.
The company emphasized that multiple cybercriminal operators are using StealC in unique attack chains, reflecting its flexible deployment capabilities and ongoing demand.