SentinelOne, a major U.S.-based cybersecurity firm known for its endpoint and extended detection and response (EDR/XDR) solutions, has revealed new findings about an attempted cyberattack linked to Chinese state-backed hackers. The attackers targeted SentinelOne through an IT services and logistics provider—an approach designed to gain access via the company’s supply chain.
The campaign appears to be part of a broader wave of espionage activity that has affected more than 70 organizations across industries including government, telecom, media, finance, IT, and manufacturing between June 2024 and March 2025.
“This post highlights the persistent threat posed by China-nexus cyberespionage actors to a wide range of industries and public sector organizations, including cybersecurity vendors themselves,” SentinelOne stated.
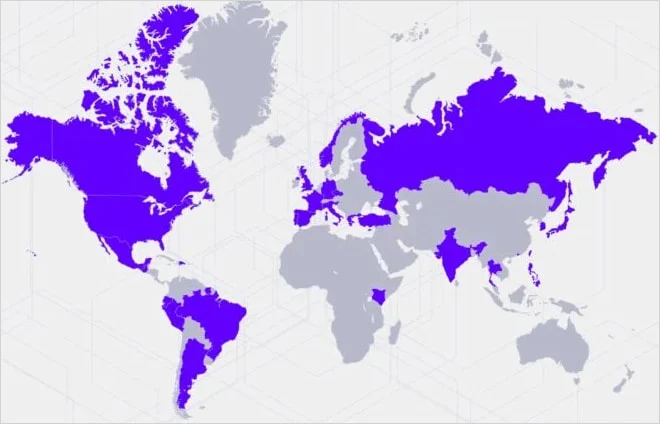
Targets of the campaign
Source: SentinelLabs
SentinelOne’s Role as a High-Value Target
SentinelOne’s platform protects critical U.S. infrastructure and large enterprise networks, making it a top priority for state-aligned threat groups. Successful infiltration could offer attackers insight into threat detection methods, enabling them to design better evasion techniques.
SentinelLabs initially flagged the breach attempt in April. The latest update from the firm outlines two coordinated threat clusters tied to known advanced persistent threat (APT) groups: APT15 (also known as UNC5174) and APT41.
The Two Threat Clusters: PurpleHaze and ShadowPad
PurpleHaze
This activity, linked to APT15, took place from September to October 2024. The attackers conducted reconnaissance on SentinelOne by scanning internet-facing systems over port 443. They registered deceptive domains like sentinelxdr[.]us and secmailbox[.]us that mimicked SentinelOne infrastructure.
In attacks against other entities, such as a South Asian government, the group used the GOREshell backdoor, dropped through zero-day exploits targeting unpatched endpoints.
ShadowPad
The more recent activity, attributed to APT41, ran from June 2024 through March 2025. This campaign involved an attempt to compromise SentinelOne indirectly via a third-party logistics and IT services provider.
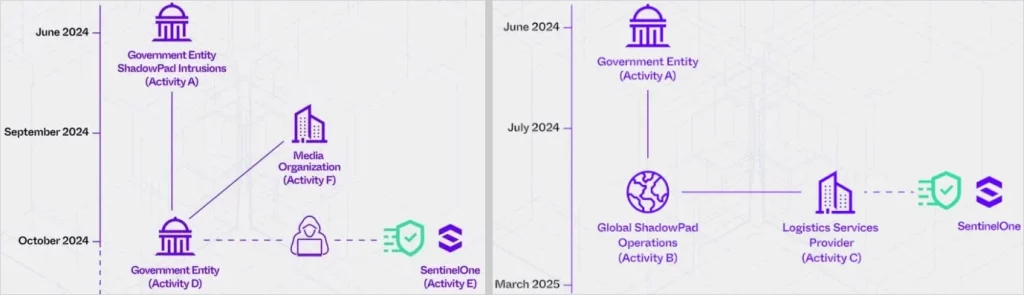
PurpleHaze (left) and ShadowPad (right) attacks on SentinelOne
Source: SentinelLabs
APT41 deployed ShadowPad malware, concealed using a technique called ScatterBrain. The malware was delivered through PowerShell with a built-in delay to bypass sandbox detection. It also initiated a system reboot 30 minutes later to erase its memory footprint.
After initial infection, the attackers installed Nimbo-C2, a remote access framework with capabilities such as:
- Command execution through PowerShell
- Screenshot capturing
- File manipulation
- User Account Control (UAC) bypass
Sensitive data was exfiltrated using a custom PowerShell script that searched recursively for documents, archived them using password-protected 7-Zip files, and exfiltrated them.
Initial Access and Exploitation Techniques
SentinelOne believes attackers leveraged vulnerabilities in a range of exposed network devices for initial access, including:
- Check Point gateways
- Ivanti Cloud Service Appliances
- Fortinet Fortigate
- Microsoft IIS
- SonicWall
- CrushFTP servers
“We suspect that the most common initial access vector involved the exploitation of Check Point gateway devices,” the report noted.
SentinelOne Confirms No Breach of Its Systems
Despite the sophistication and breadth of the campaign, SentinelOne confirmed that its own software and systems remained uncompromised.
“The company thoroughly examined its assets and reported that no compromise had been detected on SentinelOne software or hardware.”
The attackers’ full intent remains unclear, but the evidence points to an attempted supply chain compromise—a growing tactic in state-sponsored cyber-espionage operations targeting security providers themselves.
The incident underscores the evolving risk to cybersecurity vendors from increasingly strategic and layered attacks orchestrated by state-linked threat actors.









