Scattered Spider has become a household name in cybersecurity circles, especially after its recent high-profile intrusions on UK retailers Marks & Spencer and Co-op. Mainstream media coverage has turned the group into a cyber-villain monolith, but the reality is more complex—and far more alarming. This blog breaks down what most people think they know about Scattered Spider, what’s often missed, and why this threat actor represents a turning point in modern identity-based cyberattacks.
There Is No “Scattered Spider”—At Least Not as You Know It
One of the most misunderstood facts is that Scattered Spider isn’t a single, unified group.
The name was coined by CrowdStrike, but other vendors have labeled the same (or overlapping) behaviors with different tags: UNC3944 (Mandiant), Octo Tempest (Microsoft), 0ktapus (Group-IB), Muddled Libra (Unit 42), and Scatter Swine (Okta). These aliases refer not to a centralized threat actor but to a distributed collective of cybercriminals who share similar techniques and goals.
This classification muddies attribution further because it often overlaps with ransomware-as-a-service (RaaS) crews like DragonForce, who provide encryption tools and infrastructure to affiliates. In the M&S and Co-op attacks, for example, it appears DragonForce provided the payload, while the initial access was handled by actors in the “Scattered Spider” mold.
“What we call Scattered Spider is better understood as a playbook than a team—a loose collective of native English-speaking attackers operating with remarkable agility.”
So what defines “Scattered Spider”?
- Primarily English-speaking operators from the UK, US, Canada, Australia, with some links to Europe, Russia, and India.
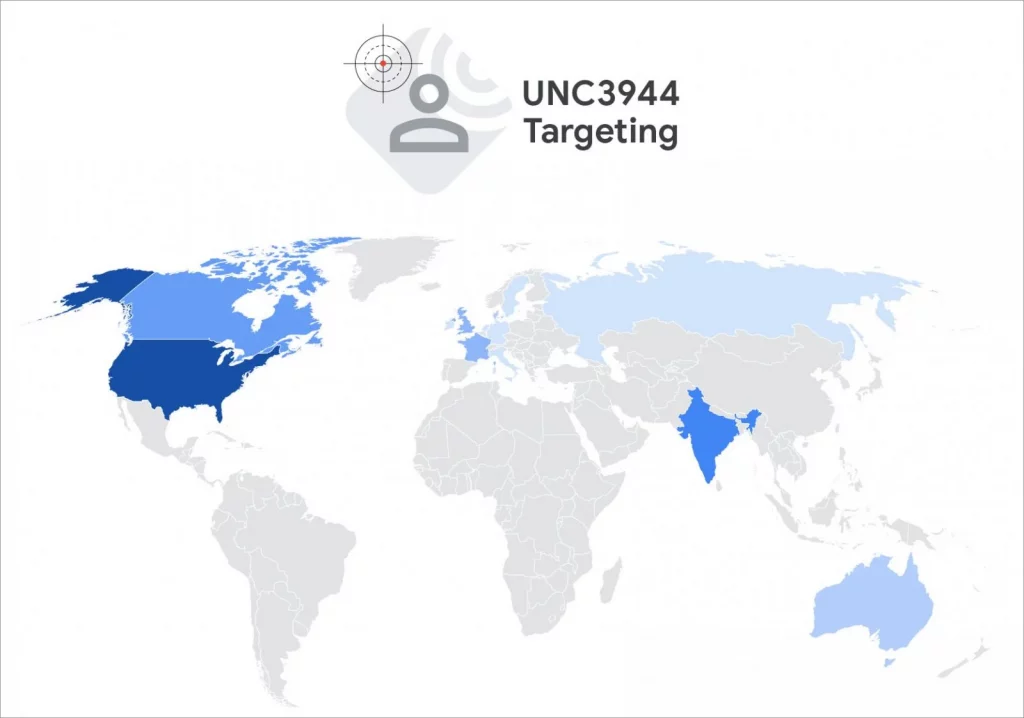
Scattered Spider presence
Source: Mandiant
- Identity-based TTPs like phishing, credential stuffing, SIM swapping, vishing, and smishing—focused entirely on account takeovers.
- Cloud-native targeting, especially against platforms like Okta and Microsoft Entra, using account compromise to navigate cloud environments.
These are attackers raised in a post-perimeter world—less interested in exploiting networks, more focused on manipulating identity systems. Most likely, they began their cybercriminal careers in fraud and carding, not port scanning or shell exploits.
Identity Is Their Weapon of Choice
Scattered Spider exemplifies the identity-first attacker. Their operations aren’t built around zero-days or network exploits, but on phishing, smishing, SIM swapping, vishing, and social engineering to gain unauthorized access to cloud identity platforms like Okta and Microsoft Entra. Once inside, they leverage account takeovers—especially of privileged users—to move laterally and launch ransomware, steal data, or extort victims.
These attackers don’t need deep technical exploits; they’re con artists fluent in English, seasoned in social engineering, and experts in abusing authentication systems. Most began in internet fraud or credit card scams and have now evolved into cloud-native adversaries.
Help Desk Scams: Not New, Just Effective
One recurring theme in Scattered Spider’s campaigns is the help desk scam—a social engineering tactic where the attacker impersonates an employee and convinces support staff to reset credentials or remove MFA. While the tactic made headlines in recent UK attacks, it’s far from new.
These scams often bypass multiple layers of security by exploiting a single weak link: a helpful human.
“Help desks, especially outsourced ones, are vulnerable by design—measured by speed, not caution.”
Here’s how it works:
- The attacker poses as an employee and claims to have a new device.
- They ask to remove old MFA settings and register a new number or email.
- With the MFA reset link now redirected, they use self-service portals to reset the password and take over the account.
From there, attackers target administrative accounts, bypassing traditional privilege escalation. Because many help desks use the same process for all accounts, attackers can go straight for high-value targets.
This method has proven highly effective. But it’s not new.
Scattered Spider has used help desk and voice-based social engineering since 2022. Notable examples include:
- Twilio, LastPass, Riot Games, and Coinbase — where voice phishing (vishing) enabled initial access.
- Caesars Entertainment (Aug 2023) — $15M ransom paid after help desk-assisted access.
- MGM Resorts (Sep 2023) — resulted in $100M+ losses, 6TB of stolen data, and a class-action lawsuit.
- Transport for London (Sep 2024) — affected 5,000 users and required in-person password resets for 30,000 employees.
Despite extensive media focus, the help desk vector is only one part of a broader, evolving identity attack strategy.
Unfortunately, fixes like callback verification or webcam ID checks are increasingly unreliable in a world of SIM swapping and deepfakes. SIM swapping can subvert call-back verification. Deepfake video can fool identity checks. And helpfulness, a help desk’s core trait, is also its greatest vulnerability.
Outsourced or offshored help desks—removed from company culture and context—are especially prone to these impersonation attacks.
Scattered Spider Doesn’t Rely on Just One Trick
While help desk impersonation is one of their favored techniques, Scattered Spider maintains a broader toolkit:
- SIM Swapping to redirect MFA or password reset flows.
- Smishing and Phishing, often targeting Okta credentials.
- AiTM (Attacker-in-the-Middle) Toolkits to intercept MFA tokens during login sessions.
- Inbound Federation Attacks to impersonate users across tenants in cloud environments.
- VMware Hypervisor Targeting, notably in the M&S and MGM attacks, where attackers encrypted systems directly at the hypervisor layer—evading endpoint detection and response (EDR) tools running inside virtual machines.
These attackers go straight for privileged accounts. In the MGM Resorts breach, they accessed an Okta Super Admin account and used inbound federation attacks to impersonate any user in the environment, elevate privileges in Azure, and ultimately deploy ransomware via VMware.
VMware servers have become a consistent final-stage target. By compromising VCentre Admin groups, attackers can encrypt entire hypervisors—bypassing endpoint detection systems that reside inside the virtual machines.
These tactics reflect a clear pattern: endpoint and network defenses are not their primary concern. They exploit identity to move laterally and escalate before endpoint controls ever have a chance to react.
Compare this to ShinyHunters and the 2024 Snowflake attacks—where credential databases from infostealer logs were used to bypass weak MFA implementations and breach over 165 customers. Or Lapsus$, who deployed eerily similar identity-focused techniques as early as 2021.
Their objective is consistent: bypass MFA, gain account access, escalate privileges, and deploy payloads with minimal resistance.
Why Arrests Haven’t Stopped the Spider from Spreading
Despite arrests throughout 2024, attacks linked to Scattered Spider’s playbook have only escalated. That’s because we’re not dealing with a closed, hierarchical group but rather a diffused, international network of like-minded cybercriminals—primarily native English speakers operating from the UK, US, Canada, Australia, and parts of Europe and Asia.
The distributed nature of this threat makes it more persistent and more dangerous. Even as some actors are arrested or drop out, others quickly adapt and fill the void—bringing new tools, tactics, and targets.
What You Can Do to Protect Your Environment from Scatter Spider
You can’t defend against Scattered Spider with firewalls or antivirus alone. Protection requires an identity-centric security model with modern, resilient controls:
- Multi-party authorization for privileged account resets.
- In-person verification for high-value identity changes.
- MFA reset freezes during suspicious behavior.
- Security awareness training focused on social engineering tactics like vishing and impersonation.
Help desks, in particular, need to be hardened—not just technically, but culturally. Attackers exploit helpfulness. If SLAs reward speed over scrutiny, the system remains exposed.
Conclusion
Scattered Spider isn’t just a threat group—it’s a sign of the times. These actors represent the shift to a post-MFA world, where traditional security controls are easily bypassed through manipulation and misuse of identity infrastructure.
Whether it’s ransomware deployment, data theft, or extortion, these attackers don’t brute-force their way in. They ask politely—and too often, someone opens the door.









