Stolen Employee Logins from Tata Consultancy Services Used in Marks & Spencer Ransomware Attack
The Scattered Spider ransomware group allegedly gained unauthorized access to Marks & Spencer (M&S) by using login credentials from two employees at Tata Consultancy Services (TCS), a third-party IT services provider. The revelation adds a new dimension to the ongoing investigation into the April 2025 attack, which has significantly disrupted operations at the 141-year-old UK retailer.
According to sources speaking to Reuters, the credentials from TCS employees were used to access M&S systems. TCS, which also counts Co-op and several other major British retailers as clients, has not yet publicly commented on the breach.
“At least two Tata Consultancy Services employees’ M&S logins were used as part of the breach,” one source familiar with the investigation told Reuters.
This attack is consistent with Scattered Spider’s established tactics, which rely heavily on compromising third-party credentials, social engineering, and MFA bypass techniques to infiltrate enterprise networks.
Third-Party Risk and Supply Chain Exposure Under Scrutiny
Tata Consultancy Services, headquartered in Mumbai, is one of the largest global IT consulting firms, employing over 600,000 people in 55 countries. It has longstanding partnerships with M&S and Co-op and has been instrumental in delivering cloud-first, digital transformation projects for both.
In August 2023, M&S and TCS won “Retail Partnership of the Year” for building a new loyalty platform using modern cloud architectures and engineering practices.
“TCS and M&S were recognised for their collaboration to build an in-house loyalty platform using a cloud-first strategy,” stated TCS in a press release.
Ironically, in February 2024, TCS also announced a strategic partnership with Co-op to modernize the company’s IT infrastructure and migrate to the cloud — a project that would commence just months before both M&S and Co-op were hit by cyberattacks attributed to Scattered Spider.
These interlinked vendor relationships raise serious concerns about third-party access controls, credential hygiene, and supply chain security governance across the UK retail sector.
Source: corporate.marksandspencer.com
Social Engineering, MFA Bypass, and Help Desk Impersonation
The UK’s National Cyber Security Centre (NCSC) has acknowledged that recent attacks against M&S, Harrods, and Co-op may share commonalities in initial access methods, particularly social engineering techniques aimed at IT help desks.
Scattered Spider, also known by industry aliases such as UNC3944 and 0ktapus, is notorious for:
- Impersonating IT help desk agents to trick employees into providing MFA tokens
- Conducting SIM-swapping and SMS phishing
- Inducing MFA fatigue through repeated login prompts
“Modern MFA systems rely on factors like passwords and SMS codes — things that can be phished or socially engineered,” said Andrew Bud, CEO of biometric security firm iProov.
Bud advocates for biometric authentication as a necessary evolution.
“If an employee uses face verification to confirm identity, a threat actor impersonating the help desk just receives a useless selfie.”
The NCSC blog also stated that it is “not yet in a position to say if the attacks are linked,” but reiterated that attackers are increasingly infiltrating through legitimate credentials, cloud services, and trusted partner networks.
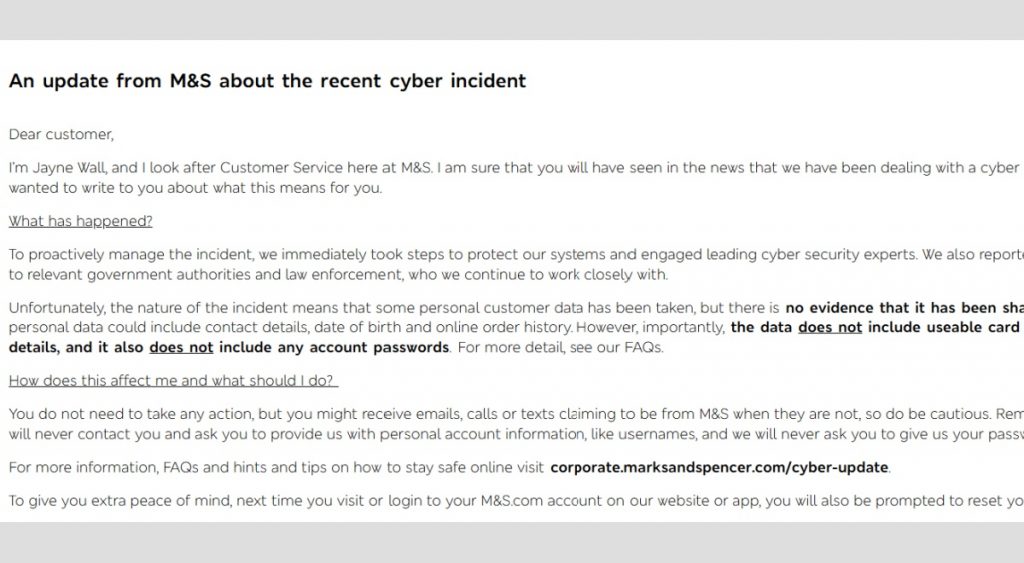
Impact on M&S: System Downtime, Data Theft, and Financial Losses
Nearly a month after the breach, Marks & Spencer continues to recover, with substantial operational impact:
- Online ordering systems remained down for weeks
- A customer-wide password reset was triggered after data was confirmed stolen
- The retailer lost approximately £60 million in profit due to disruption
- An estimated £1 billion in market value was wiped from its stock
“Full-service restoration for a digitally mature retailer can take days, even weeks,” said Aditya K. Sood, VP of Security Engineering and AI Strategy at Aryaka.
Sood emphasized that retailers like M&S should implement network segmentation, redundant backup systems, and rigorous third-party access controls to reduce the blast radius of such attacks.
“Critical systems such as payment platforms, inventory, and remote work infrastructure are deeply interdependent. Without proper segmentation and incident response orchestration, recovery is slow and painful.”
Scattered Spider’s Campaign Against UK Retail: M&S, Co-op, Harrods
The ransomware group also targeted Co-op, where it attempted to deploy ransomware but was detected in real time. Additionally, Harrods reportedly experienced a separate cyberattack shortly after M&S.
Despite the technical failure at Co-op, Scattered Spider successfully exfiltrated data from M&S and caused major service disruption. The UK retail sector is now reckoning with the consequences of a sophisticated, multi-pronged campaign against high-value targets.
Scattered Spider’s tactics were previously used in 2023 attacks against MGM Resorts and Caesars Entertainment, where the group bypassed MFA protections by impersonating help desk workers.
Recommendations: Strengthening Identity Verification and Vendor Access Security
The M&S breach, likely enabled through legitimate partner credentials, underscores the urgent need for:
- Zero Trust Architecture with continuous identity verification
- Restricting vendor access using just-in-time provisioning
- Implementing phishing-resistant MFA, including biometrics and FIDO2 standards
- Enhanced monitoring of third-party accounts and MFA reset workflows
- Regular red-teaming and supply chain security assessments
“These kinds of threats are now having visibly damaging consequences and will only escalate,” Bud warned. “It’s time to adopt new, robust methods of identity verification that cannot be easily social engineered.”









