The Cookeville Regional Medical Center (CRMC) in Tennessee is grappling with the aftermath of a ransomware attack launched on July 13, now claimed by the Rhysida gang.
The medical center, which serves more than 250,000 patients annually across 14 counties in Tennessee and Kentucky, disclosed the incident as a “network security event” that caused system outages. While hospital officials have assured patients that care remains largely unaffected, reports indicate delays in test results, cancelled appointments, and scheduling issues across outpatient offices.
CRMC confirmed that its Information Systems (IS) Security Team has been working around the clock to restore impacted systems, assisted by external cybersecurity experts. Federal law enforcement has also been notified.
Tim McDermott, CRMC Chief Information Officer, stated:
“The IS security team has been here 24 hours a day. We greatly appreciate everyone’s patience during this process. We take this matter seriously, and we are working with outside IT experts to investigate the issue.”
The hospital promised to notify patients if their data was found to be accessed or acquired without authorization.
Crmchealth.org. Rhysida leak site. Image by Cybernews.
Rhysida Lists CRMC Data for Sale on Dark Web
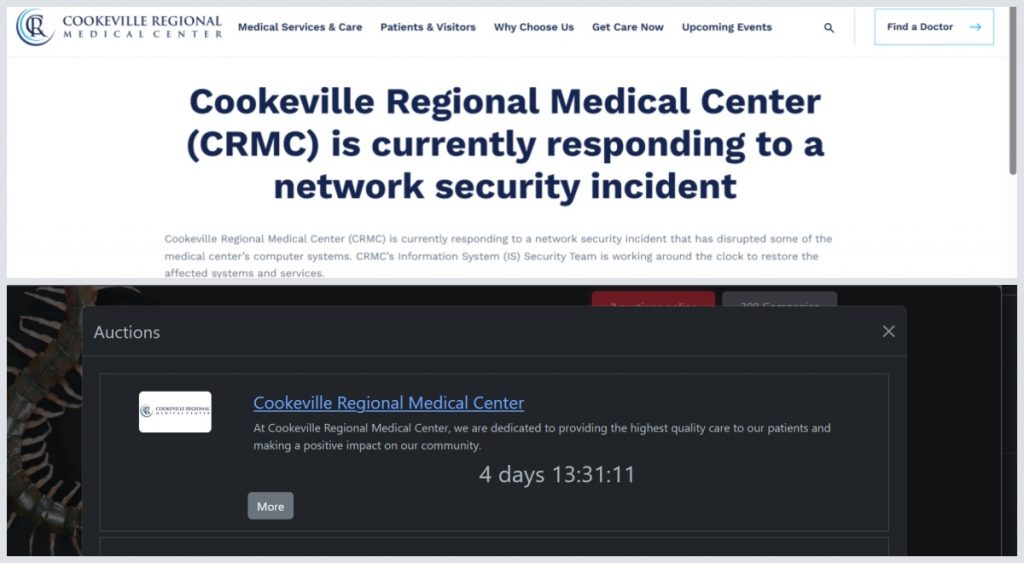
The Rhysida ransomware gang listed CRMC on its dark web leak site on August 2—over two weeks after the initial breach—suggesting that ransom negotiations failed.
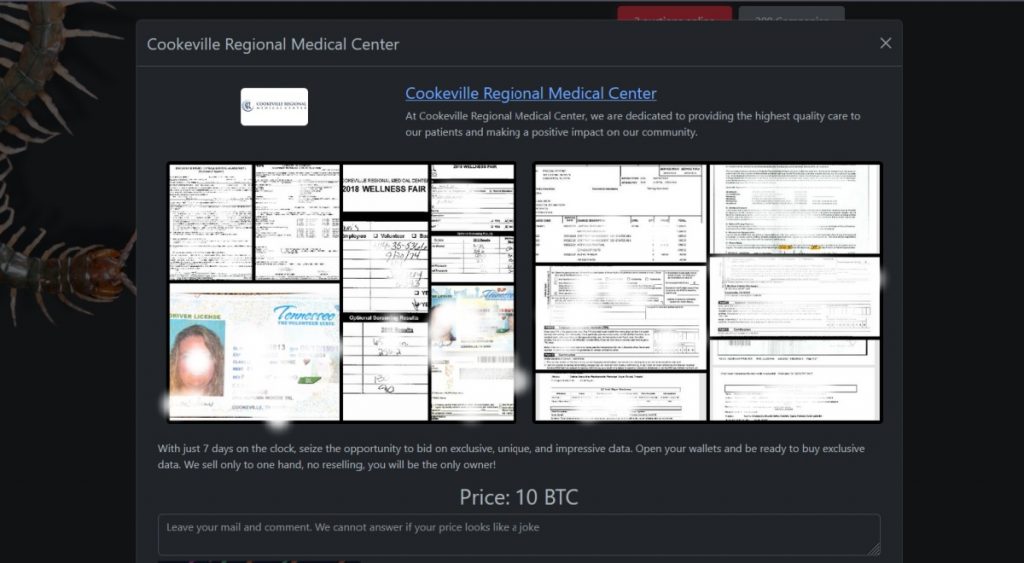
The group has given CRMC just over four days to pay an undisclosed ransom before auctioning the stolen data for 10 Bitcoin (approximately $1.15 million).
As proof, Rhysida published more than a dozen sample files, which reportedly include driver’s licenses, patient medical records, employee tax forms, and financial documents dating back to 2018.
Limited Impact on Patient Care, But Communication Concerns Surface
In a Facebook update posted on July 15, CRMC CEO Buffy Key assured the community that patient care remained a priority:
“Patient care has not been affected, even though technology, scheduling, etc. have been slow. Our team has stayed grounded in making sure we see patients and care for them.”
However, some patients expressed frustration over delays and lack of updates, with reports of long waits for test results in emergency departments. Others reported no issues with care during their visits.
The hospital has not provided an estimated timeline for full system restoration since its initial statement.
Rhysida victim leak site. Image by Cybernews.
Rhysida Expands Its Ransomware Campaign
Rhysida, a Russian-linked ransomware group active since May 2023, has claimed over 200 victims worldwide across sectors including healthcare, education, manufacturing, and local governments.
The group typically gains access through phishing attacks, uses Cobalt Strike tools for network exploitation, and deploys its namesake ransomware to encrypt systems. It is known for leveraging patient safety risks to pressure healthcare providers into paying ransoms.
High-profile past victims include The Washington Times, the UK’s British Library, the City of Columbus, and multiple U.S. hospitals such as Prospect Medical Group and Lurie Children’s Hospital.
In recent attacks, Rhysida has demanded multimillion-dollar payments, including 100 Bitcoin (approximately $11 million) from Seattle-Tacoma International Airport in 2024.
Although security researchers at Korea Internet & Security Agency (KISA) released a free Rhysida decryption tool last year, the group continues to expand its operations and affiliate partnerships with other ransomware actors such as Vice Society.









