Two newly disclosed vulnerabilities in the vBulletin forum software have placed thousands of websites at serious risk of compromise. The flaws, tracked as CVE-2025-48827 and CVE-2025-48828, impact a wide range of vBulletin versions and have been rated critical—with CVSS scores of 10.0 and 9.0 respectively. One of the vulnerabilities enables remote code execution (RCE), making it a severe risk for enterprise-grade communities still using outdated versions of the platform.
The affected versions span from vBulletin 5.0.0 through 5.7.5 and 6.0.0 through 6.0.3, specifically on systems running PHP 8.1 or later. These flaws were likely patched quietly in late 2024 with the release of Patch Level 1 for the 6.x branch and 5.7.5 Patch Level 3, but many administrators have not upgraded—leaving their installations vulnerable.
How the Exploit Works: Abuse of PHP Reflection API and Template Engine
The vulnerabilities were disclosed on May 23, 2025, by researcher Egidio Romano (EgiX). In a technical blog post, Romano demonstrated how vBulletin’s use of PHP’s Reflection API—combined with changes introduced in PHP 8.1—could be exploited to invoke protected methods without altering their visibility.
The issue centers on the way vBulletin handles template conditional logic and dynamic method calls. Attackers can abuse the endpoint 'ajax/api/ad/replaceAdTemplate' by injecting custom template code. This allows them to:
- Call protected functions via crafted URLs
- Bypass “unsafe function” filters using variable function calls
- Inject malicious templates that lead to full RCE
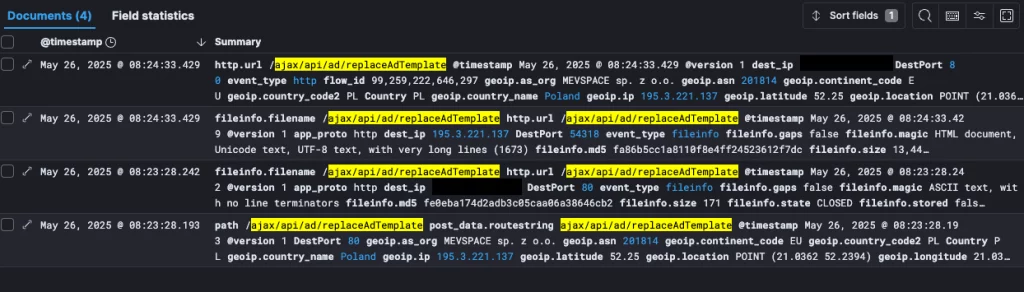
Logs showing exploitation attempts
Source: blog.kevintel.com
Once exploited, the attacker gains shell-level access on the underlying server, operating with the privileges of the web server user (commonly www-data on Linux).
“The vulnerability lies in the ability to invoke protected methods via crafted URLs and misuse of template conditionals,” Romano explained in his detailed write-up.
Exploitation Detected in the Wild
Security researcher Ryan Dewhurst confirmed active exploitation of CVE-2025-48827 just three days later, on May 26, 2025. Using honeypot logs, Dewhurst observed multiple requests targeting the vulnerable endpoint, likely based on Romano’s disclosed exploit.
The exploitation attempts included efforts to:
- Deploy PHP-based web shells
- Execute system-level commands remotely
- Use backdoors to maintain persistent access
One set of logs even traced the activity to an attacker based in Poland. Dewhurst stated that while the full RCE chain was not confirmed in these logs, its execution is highly probable given the nature of the payloads and the public availability of working proof-of-concept (PoC) code.
Additionally, Nuclei templates for vulnerability detection were available just one day after disclosure, further accelerating the speed of exploitation.
The Broader vBulletin Risk Landscape
vBulletin remains one of the most commonly used PHP/MySQL forum platforms worldwide, favored for its modularity, mobile APIs, and AJAX-based features. However, this flexibility comes at a cost—a large and complex attack surface.
Historically, vBulletin has been a repeated target for severe vulnerabilities. Previous RCE flaws in the platform have been weaponized in attacks against high-traffic forums, leading to massive data breaches and user credential leaks.
Administrators are urged to:
- Upgrade immediately to vBulletin version 6.1.1, which is not affected by these vulnerabilities
- Verify patches for earlier 6.x or 5.7.5 installations
- Monitor logs for suspicious access to the
'replaceAdTemplate'endpoint - Conduct external scans using updated Nuclei templates or other detection mechanisms
Failure to act may leave critical infrastructure open to takeover, data exfiltration, or even lateral movement inside broader corporate networks.