Authorities across seven countries have dismantled 300 servers and seized 650 domains in a global operation targeting ransomware infrastructure and malware-as-a-service networks.
Law Enforcement Hits Ransomware Infrastructure in Coordinated International Takedown
From May 19 to 22, law enforcement agencies conducted a large-scale operation under the banner of Operation Endgame, neutralizing critical parts of the ransomware ecosystem. Led by Europol and Eurojust and supported by private sector partners, the coordinated effort spanned multiple nations and struck a major blow to cybercriminal operations.
According to the task force:
“From 19 to 22 May, authorities took down some 300 servers worldwide, neutralised 650 domains, and issued international arrest warrants against 20 targets.”
An additional €3.5 million in cryptocurrency was seized during the action week, raising the total seizures from Operation Endgame to over €21.2 million.
The operation focused on disrupting malware loader ecosystems used to facilitate ransomware attacks. The takedown specifically targeted components of:
- Qakbot
- Bumblebee
- Lactrodectus
- Trickbot
- DanaBot
- Warmcookie
These loader strains serve as initial access tools in the ransomware-as-a-service (RaaS) supply chain.
“By disrupting the services criminals rely on to deploy ransomware, we are breaking the kill chain at its source,” said Europol Executive Director Catherine De Bolle.
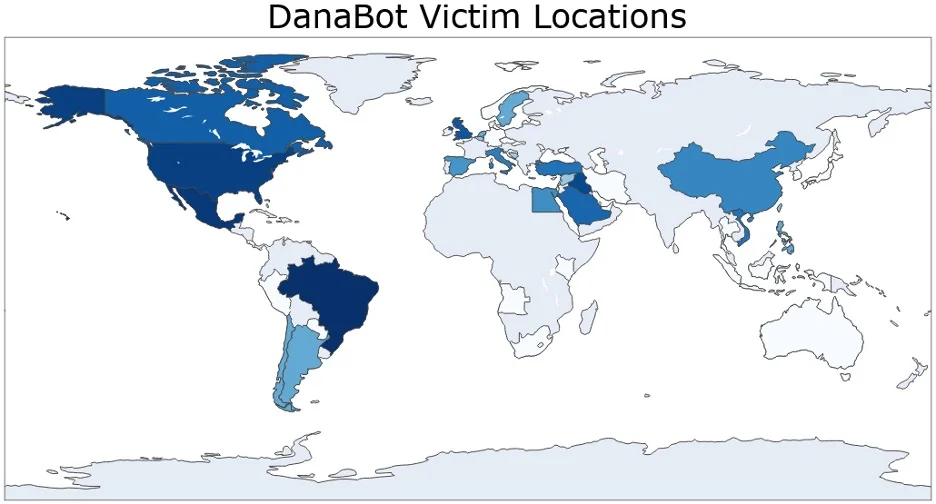
Image: Lumen
U.S. DOJ Charges 16 Linked to DanaBot Malware-as-a-Service Network
In parallel with the takedown, the U.S. Department of Justice unsealed charges against 16 individuals allegedly involved in running the DanaBot malware operation. Eight of the defendants were named, including nationals of Russia and other countries, while the rest were identified by aliases.
DanaBot, active since 2018, is a malware-as-a-service botnet that has infected over 300,000 computers and caused more than $50 million in damages. It is capable of:
- Deploying secondary malware including ransomware
- Hijacking banking sessions and stealing credentials
- Enabling full remote access, keystroke logging, and video surveillance
- Recording screen interactions for espionage
The DOJ noted that a separate version of DanaBot was used for espionage purposes against military, law enforcement, and diplomatic personnel in North America and Europe.
“This variant was allegedly used to target diplomats, law enforcement personnel, and members of the military,” the DOJ stated.
Previous Operation Endgame Successes Set the Stage
This week’s actions follow earlier Operation Endgame milestones:
- In 2023, over 100 servers and 2,000 domains used by loader operations like IcedID, Pikabot, and Smokeloader were seized.
- In June 2024, police arrested a LockBit and Conti crypter developer who helped malware evade antivirus systems.
- In April, intelligence from a seized Smokeloader customer database led to the arrest of five cybercriminals.
- Earlier this month, 2,300 domains tied to the Lumma infostealer MaaS operation were taken offline in a Microsoft-led disruption.
Additionally, this week saw Rustam Rafailevich Gallyamov, a Russian national and alleged leader of Qakbot, indicted by U.S. authorities. Qakbot is linked to over 700,000 infected systems used in ransomware campaigns.









