Microsoft has announced the takedown of several GitHub repositories linked to a widespread malvertising campaign that has affected nearly one million devices globally. This campaign utilized malicious ads embedded in videos on illegal streaming sites to redirect users to harmful content.
Details of the Malvertising Campaign
According to Microsoft’s threat analysts, the attacks were first detected in December 2024. The team observed multiple devices downloading malware from the compromised GitHub repositories, which were subsequently used to deploy various malicious payloads.
“The streaming websites embedded malvertising redirectors within movie frames to generate pay-per-view or pay-per-click revenue from malvertising platforms,” Microsoft explained.
Attack Mechanism
The malvertising videos redirected users to GitHub repositories, where malware was designed to perform system discovery and collect detailed information about the infected systems, including:
- Memory size
- Graphics details
- Screen resolution
- Operating system
- User paths
Once this data was collected, it was exfiltrated while additional payloads were deployed.
Multi-Stage Payload Delivery
The attack operated in multiple stages:
- Initial Access: Users were redirected to malicious GitHub repositories.
- Data Collection: The malware gathered system information.
- Stage Three Payload: A PowerShell script downloaded the NetSupport remote access trojan (RAT) from a command-and-control server, establishing persistence in the registry.
- Additional Payloads: The malware could also deploy the Lumma information stealer and the Doenerium infostealer to extract user data and browser credentials.
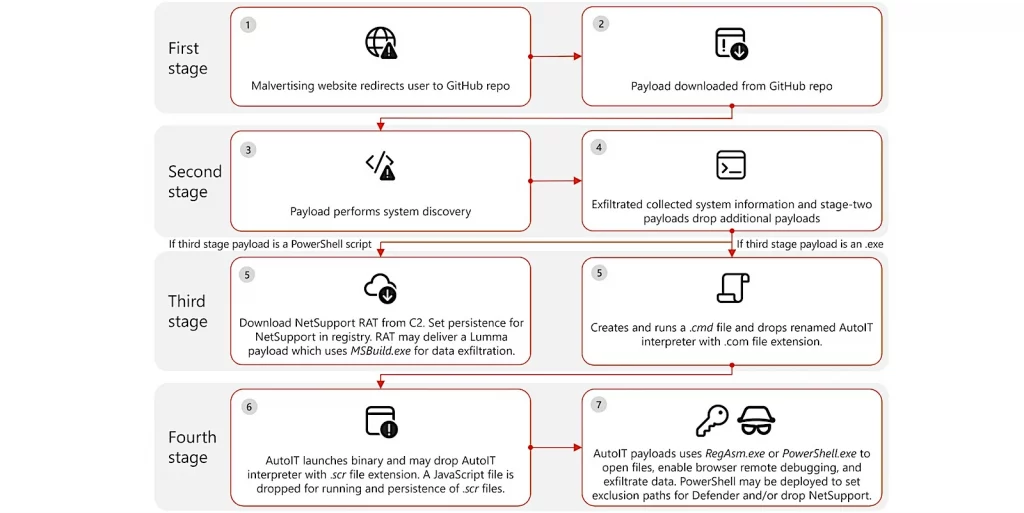
Microsoft noted that if the third-stage payload was an executable, it would create and execute a CMD file while dropping an AutoIt interpreter. This interpreter could launch binaries and facilitate further payloads.
Scope of the Impact
The campaign, tracked under the name Storm-0408, has affected a wide range of organizations and industries, impacting both consumer and enterprise devices. Microsoft emphasized the indiscriminate nature of the attack.
“This activity is tracked under the umbrella name Storm-0408 that we use to track numerous threat actors associated with remote access or information-stealing malware,” Microsoft stated.
Microsoft’s report highlights the complexity and reach of this malvertising campaign. The use of popular platforms like GitHub for malware distribution indicates a significant shift in tactics among cybercriminals.
For more detailed information on the various stages of the attacks and the payloads used, refer to Microsoft’s complete report.
Helpful Reads:









