LockBit Ransomware Operation Compromised, Internal Database Leaked
The LockBit ransomware group has suffered a major breach after its dark web affiliate panels were defaced and replaced with a link to a MySQL database dump, exposing internal operations, victim negotiations, and affiliate credentials.
All LockBit panels now display the message:
“Don’t do crime CRIME IS BAD xoxo from Prague”
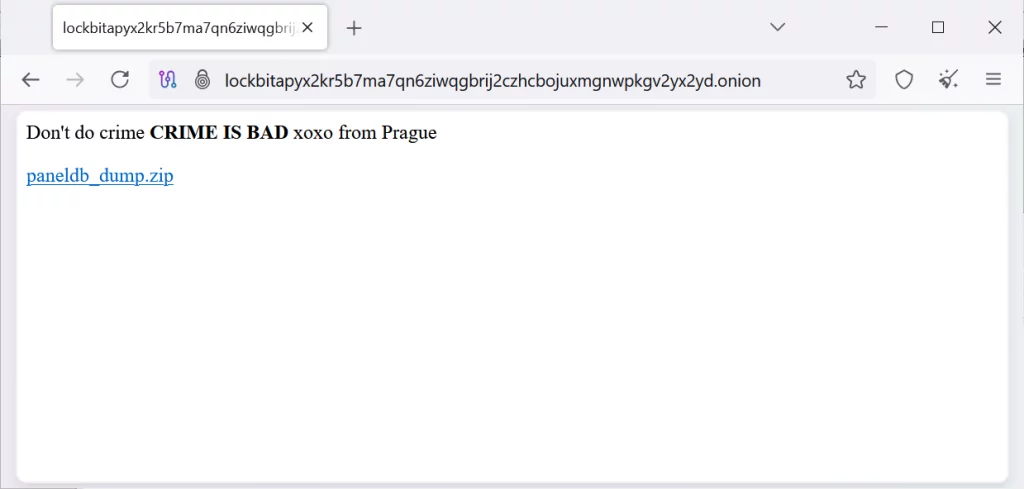
LockBit dark web site defaced with link to database
This message includes a link to download a file named paneldb_dump.zip. The contents of the dump were first spotted by threat actor “Rey” and analyzed by BleepingComputer.
Database Dump Reveals Victim Negotiations and Affiliate Credentials
The SQL database dump contains 20 tables, revealing extensive information about LockBit’s operations. Key tables include:
btc_addresses:
Contains 59,975 unique bitcoin wallet addresses used by the group.buildsandbuilds_configurations:
These tables detail individual malware builds created by affiliates, including targeted companies and specific settings like ESXi exclusions and file encryption lists.chats:
Stores 4,442 negotiation messages between LockBit and its victims, dating from December 19, 2024, to April 29, 2025.users:
Lists 75 affiliates and administrators. Passwords were stored in plaintext. Notable examples include'Weekendlover69','MovingBricks69420', and'Lockbitproud231'.
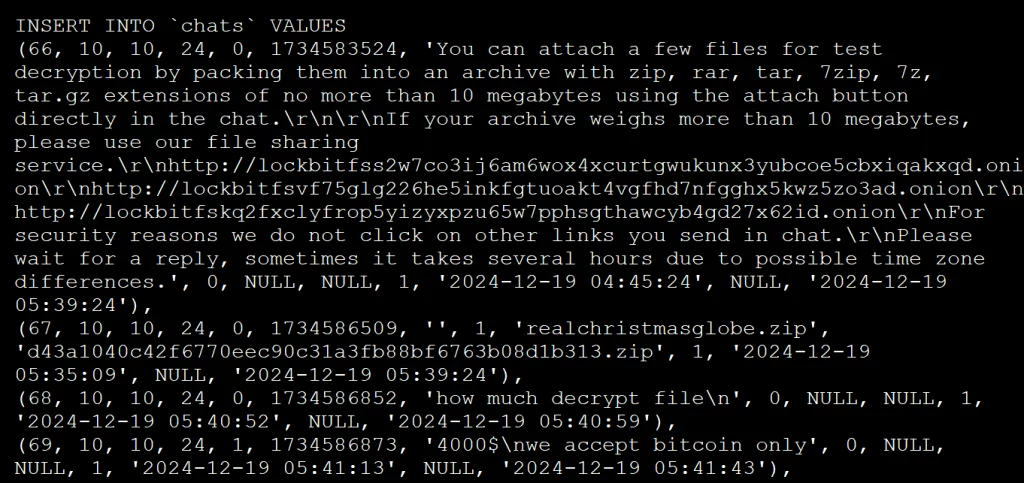
Affiliate panel ‘chats’ table
Despite the exposure, LockBit’s operator “LockBitSupp” confirmed in a Tox chat with Rey that no private keys were leaked and no operational data was lost.
Timeline and Breach Indicators Suggest a Coordinated Attack
The dump appears to have been generated on April 29, 2025, based on timestamps in the negotiation records. While the attacker’s identity remains unknown, the defacement message matches one used in a recent breach against Everest ransomware, indicating a possible link.
In 2024, LockBit’s infrastructure was previously disrupted during Operation Cronos, a coordinated law enforcement effort that dismantled:
- 34 data leak servers
- Cryptocurrency wallets
- 1,000 decryption keys
- The original affiliate management panel
LockBit managed to resume operations afterward, but this latest breach could severely impact its credibility among affiliates and the broader cybercrime ecosystem.
A Growing List of Breached Ransomware Groups
LockBit now joins other ransomware operations that have suffered internal data leaks, including Conti, Black Basta, Everest.
The exposure of affiliate communications and internal configurations may further discourage cybercriminal collaboration with the group.









