A new SuperBlack ransomware strain, is actively exploiting vulnerabilities in Fortinet firewall appliances. The attacks are attributed to a threat actor known as Mora_001, who is leveraging two authentication bypass flaws: CVE-2024-55591 and CVE-2025-24472.
These vulnerabilities were disclosed by Fortinet in January and February 2025, respectively.
Fortinet confirmed that CVE-2024-55591 was exploited as a zero-day vulnerability, with Arctic Wolf reporting attacks dating back to November 2024. Initially, there was confusion surrounding CVE-2025-24472, as Fortinet initially stated it had been patched in January 2024 and was not being exploited.
However, Forescout researchers discovered SuperBlack attacks using CVE-2025-24472 as early as February 2nd, 2025. Forescout shared their findings with Fortinet, leading to an update of Fortinet’s advisory to acknowledge active exploitation of CVE-2025-24472.
The SuperBlack ransomware attack chain, as detailed by Forescout, is highly structured:
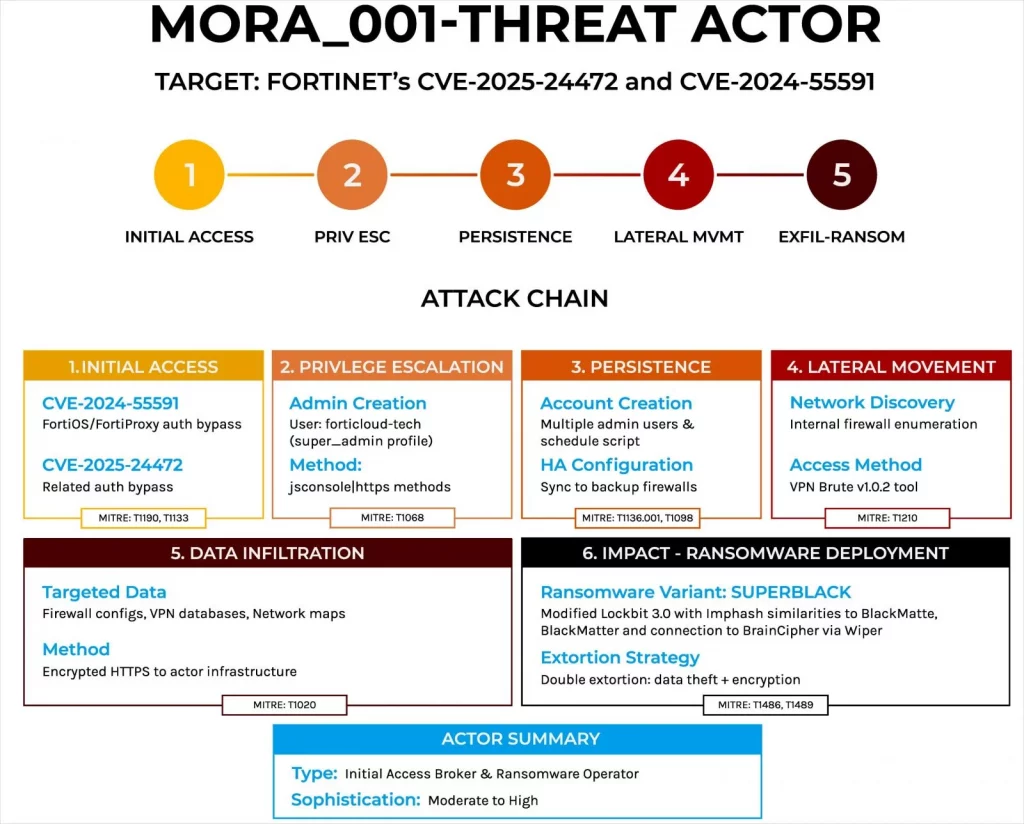
Mora_001’s attack chain overview
Source: Forescout
- Mora_001 gains super_admin privileges by exploiting the Fortinet vulnerabilities via WebSocket attacks (jsconsole interface) or direct HTTPS requests to exposed firewall interfaces.
- New administrator accounts (forticloud-tech, fortigate-firewall, adnimistrator) are created, with automation tasks ensuring their recreation if removed.
- The attacker maps the network and attempts lateral movement using stolen VPN credentials and newly added VPN accounts, WMIC, SSH, and TACACS+/RADIUS authentication.
- A custom tool is used to steal data before file encryption for double extortion. File and database servers, and domain controllers are prioritized.
- Ransom notes are deployed.
- A custom wiper, ‘WipeBlack,’ is used to remove ransomware executables, hindering forensic analysis.
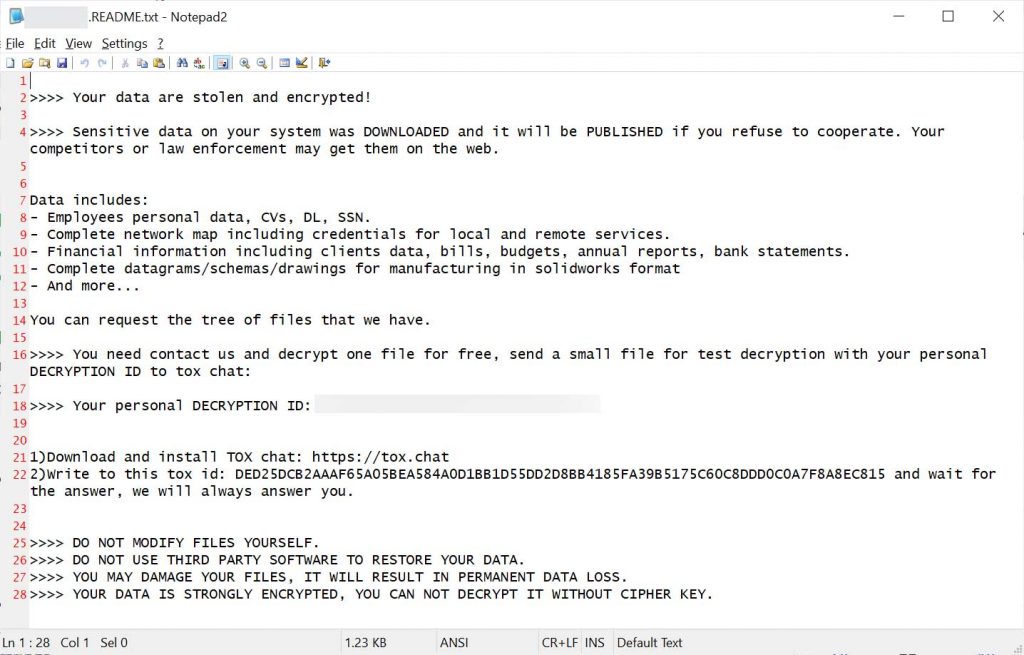
SuperBlack ransom note
Source: Forescout
Forescout’s research reveals strong links between SuperBlack and LockBit ransomware:
- SuperBlack’s encryptor (VirusTotal) is based on LockBit 3.0’s leaked builder, sharing identical payload structure and encryption methods, but with original branding removed.
- The ransom note includes a TOX chat ID linked to LockBit operations.
- There is significant IP address overlap with previous LockBit operations.
- WipeBlack has also been used by BrainCipher, EstateRansomware, and SenSayQ ransomware, all linked to LockBit.

Relationship diagram based on the available evidence
Source: Forescout
This suggests Mora_001 may be a former LockBit affiliate or a member of its core team. The close relationship between SuperBlack and LockBit highlights the interconnectedness of ransomware groups and the potential for shared resources and expertise.
For further information on ransomware threat actors, see our article on Top 10 Ransomware Groups of 2024.
Helpful Reads:









