Integris Health, Oklahoma’s largest not-for-profit health network, has recently experienced a cyberattack resulting in the theft of patient data. The Integris Health data breach led to Integris Health patients receiving blackmail emails claiming that their data was compromised and would be sold to other threat actors if an extortion demand was not met.
In response to the Integris Health hacking incident, the healthcare provider swiftly took action to secure their systems and initiated an investigation to understand the extent of the unauthorized activity.
Integris Health Data Breach – Integris Notifies of Breach
The investigation into Integris hospital data breach revealed that certain files may have been accessed by an unauthorized party on November 28, 2023.
The Integris Health published a data privacy notice on their website that reads:
“INTEGRIS Health discovered potential unauthorized activity on certain systems,
Upon becoming aware of the suspicious activity, INTEGRIS Health promptly took steps to secure the environment and commenced an investigation into the nature and scope of the activity.
The investigation determined that certain files may have been accessed by an unauthorized party on November 28, 2023.”
Integris Health Patients Receive Extortion Emails – Patient Data Breached
According to reports received on December 24th, the hackers behind the Integris Health data breach have sent extortion emails to patients, claiming to have stolen the personal data of over 2 million patients.
The compromised data is said to include sensitive information such as Social Security Numbers, dates of birth, addresses, phone numbers, insurance details, and employer information.
This information has been independently verified by patients who have received these emails, confirming that their personal data was indeed compromised in the Integris Health cyberattack.
“We have contacted Integris Health, but they refuse to resolve this issue,
We give you the opportunity to remove your personal data from our databases before we sell the entire database to data brokers on Jan 5 2024.”
Integris Health Data Breach Goes Public on Tor Extortion Site
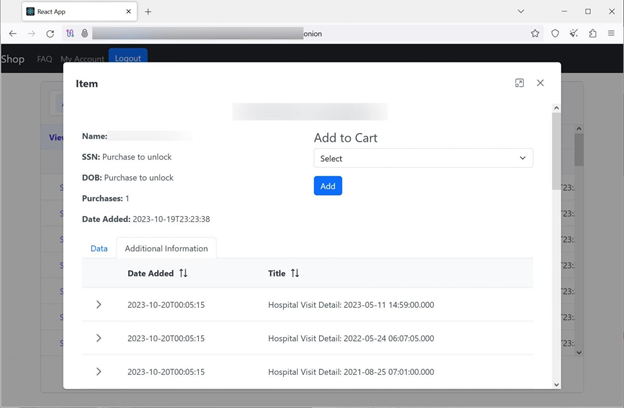
The perpetrators of the Integris healthcare data breach have included a link to a Tor extortion site in the blackmail emails. This website currently displays stolen data for approximately 4,674,000 individuals, comprising their names, Social Security Numbers, dates of birth, and details of their hospital visits.
The website allows visitors to pay $50 to have their data record deleted or $3 to simply view it. It is important to note that the total number of data records includes duplicates, and the exact count of unique records remains unclear.
Integris Health is actively aware of the emails sent to patients and has promptly updated its security notice to caution recipients against responding, contacting the sender, or clicking on any links provided in the email.
Integris is not the first hospital hit with data breach; similar emails were sent to patients of the Fred Hutchinson Cancer Center (Fred Hutch) following a breach by the Hunters International ransomware gang. The similarity between the two cases suggests the possibility of the same ransomware threat actors who were also behind the Integris Health cyber attack.
Considering the potential risk of identity theft resulting from the exposed data, some patients may be tempted to pay the ransom to have their data deleted. However, previous experiences with extortion demands have demonstrated that paying the ransom does not always guarantee the actual deletion of data. Moreover, paying the ransom exposes one’s concern, making them susceptible to further extortion attempts by the threat actors.