IntelBroker is advertising the sale of data allegedly exfiltrated from Hewlett-Packard Enterprise (HPE). The HPE data breach, announced on January 17, 2025, involves a substantial amount of sensitive information, raising serious concerns about corporate security and the protection of personal data in corporate environments.
IntelBroker, along with members of their threat group CyberN—–s, posted on a popular hacking forum claiming responsibility for the breach.
“We’ve been connecting to some of their services for about 2 days now,” wrote IntelBroker, showcasing the speed and efficiency of the attack.
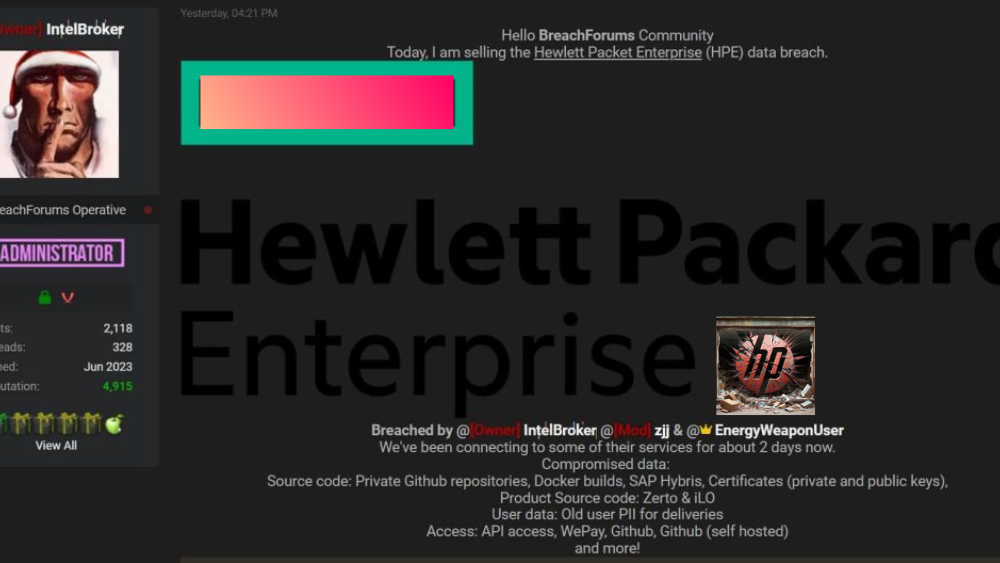
The types of data exposed in the HPE breach are alarming. The stolen data reportedly includes a range of sensitive information:
- Private GitHub repositories: This exposes valuable source code and intellectual property. The importance of securing private repositories is crucial for organizations like HPE.
- Docker builds: Compromised Docker images could lead to further vulnerabilities and attacks.
- SAP Hybris data: This indicates a potential breach of customer relationship management (CRM) systems.
- Certificates (private and public keys): This poses a significant risk, allowing attackers to impersonate HPE or access sensitive systems.
- Product source code: Zerto & iLO: The exposure of source code for products like Zerto and iLO is a severe blow to HPE’s intellectual property and security.
- Old user personally identifiable information (PII): This includes names, email addresses, and passwords, potentially leading to identity theft and other harms.
- Access to HPE’s API, WePay, and GitHub: This grants attackers extensive access to HPE’s internal systems and potentially customer data.
IntelBroker further uploaded screenshots as proof, containing names, email addresses, and passwords, illustrating the severity of the personal information exposed in this Hewlett-Packard breach. The threat actor’s actions highlight the increasing cyber threats to corporations and the need for robust cybersecurity measures.
This HPE data breach by IntelBroker is not an isolated incident. Late last year, IntelBroker claimed responsibility for a similar breach at Cisco, stealing vast amounts of data.
While Cisco confirmed data exfiltration, they stated that the threat actors accessed a publicly accessible DevHub environment, emphasizing the risks of publicly accessible development environments.
IntelBroker acknowledged accessing a DevHub instance that Cisco had accidentally left open, exfiltrating 4.5 terabytes of data. A partial upload of 2.9 gigabytes was released, containing data related to various Cisco products, including Cisco IOS XE & XR, Cisco ISE, Cisco SASE, Cisco Umbrella, and Cisco Webex.
“Hopefully this proves the legitimacy of the breach to others wanting to buy the full version,” added IntelBroker.
This incident underscores the common vulnerabilities in corporate cybersecurity and the need for proactive security measures.
Cyber Daily has reached out to HPE for a statement and further information regarding their response to the breach. The response of Hewlett-Packard to the breach, and the impact of the HP breach on customers, remain to be seen.
However, this incident serves as a stark reminder of the ever-evolving cybersecurity threats to large corporations and the critical need for robust security protocols to protect sensitive information from threat actors. Understanding how to respond to data breaches is paramount for all organizations.
This HPE data breach underscores the vital importance of protecting sensitive information, securing private repositories, and mitigating the risks associated with publicly accessible development environments.
The implications of corporate data breaches can be far-reaching, impacting both the organization and its customers. Learning from this incident and implementing effective strategies for protecting personal data in corporate environments is crucial for preventing future breaches.









