Hackers have infected Over 1 Million with Malware Using Fake Facebook Midjourney AI Pages.
Cybercriminals are creating fake profiles impersonating popular AI services like Midjourney and using them to infect over a million people with malware!
These hackers are taking it to the next level by setting up what look like legitimate communities on Facebook dedicated to these AI tools.
They gain thousands of followers by sharing real-looking image generations and news updates.
Hackers Impersonating Fake Facebook Midjourney AI Pages, SORA, DALL-E and More
The hackers engage in a deceptive tactic where they take control of genuine profiles and convert them into seemingly official community pages for popular AI tools like Midjourney, OpenAI’s SORA, DALL-E, and others.
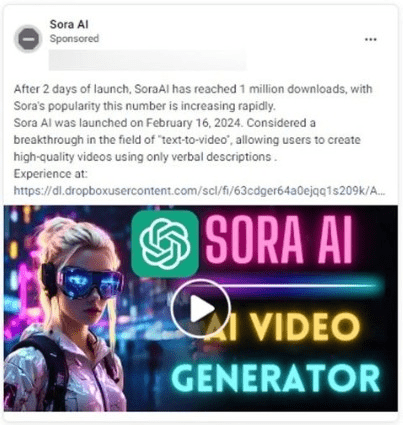
Ad for OpenAI’s Sora video generation tool
Source: Bitdefender
These malicious advertising campaigns are orchestrated through compromised Facebook profiles that impersonate well-known AI services, luring users with the promise of exclusive previews of new features.
Once users fall for these advertisements, they are directed to join fraudulent Facebook communities. Within these communities, the threat actors post updates, AI-generated images, and other relevant information to create an illusion of legitimacy for the pages.
This enables the hackers to further deceive users and exploit their trust in these seemingly authentic AI services.
The community posts within these fraudulent Facebook pages often promote exclusive access to highly anticipated AI services.
However, these posts are designed to deceive users into downloading malicious executable files that infect Windows computers with dangerous information-stealing malware. Some notable examples of such malware include Rilide, Vidar, IceRAT, and Nova.
Fake Facebook Midjourney AI Pages Campaign
The impact of these campaigns is significant, particularly due to the widespread interest in AI. Given the rapid developments in the field, it becomes challenging for individuals to keep up and differentiate between genuine announcements and obvious fraudulent attempts. Researchers at Bitdefender have come across a particularly alarming case where a malicious Fake Facebook Midjourney AI page posing as Midjourney managed to amass a staggering 1.2 million followers. This fraudulent page remained active for almost a year before it was eventually removed. Rather than creating the page from scratch, the threat actors behind the attack hijacked an existing profile in June 2023 and transformed it into a fake Midjourney page. It took until March 8, 2024, for Facebook to take action and shut down the deceptive page.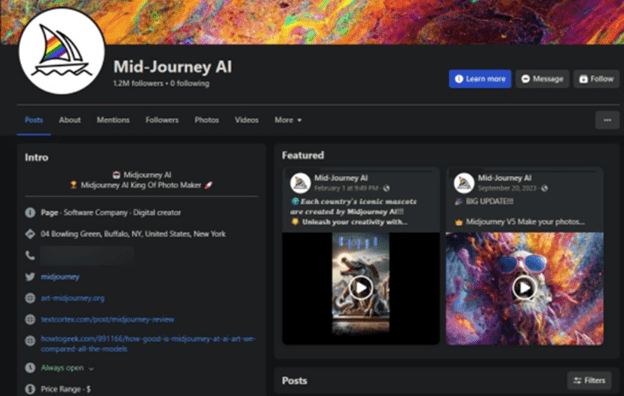
Fake Facebook profile
Source: Bitdefender
Numerous deceptive posts within these campaigns employed tactics to trick users into downloading infostealers. One common approach was to promote a non-existent desktop version of the AI tool. For instance, some posts falsely claimed the release of V6, even though the latest official version was V5.
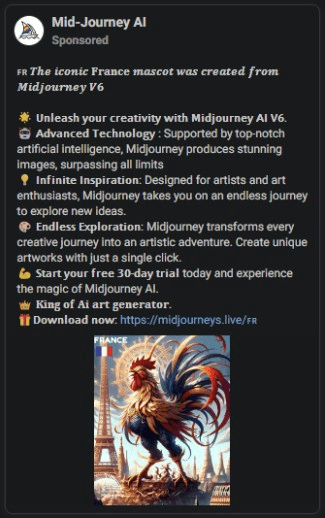
A non-existent MJ version
Source: Bitdefender
In other instances, the malicious ads capitalized on the popularity of NFT art by enticing users with opportunities to create and monetize their own artwork.
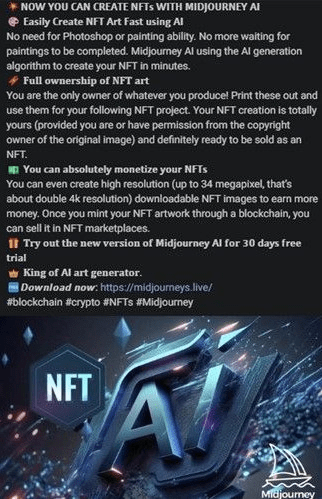
Fake NFT promotion
Source: Bitdefender
Researchers examining the targeting parameters of these Facebook ads, accessible through the Meta Ad Library, discovered that the ads predominantly targeted a specific demographic.
Men between the ages of 25 and 55 in various European countries, such as Germany, Poland, Italy, France, Belgium, Spain, the Netherlands, Romania, and Sweden, were the primary focus of the campaigns.
Hackers Replicated Official Landing Page of Midjourney
In a notable shift from using Dropbox and Google Drive links, the operators behind this campaign adopted a different approach.
They created multiple websites that replicated the official landing page of Midjourney, deceiving users into believing that they were downloading the latest version of the art-generating tool. The download links, however, led unsuspecting users to GoFile, where they unknowingly downloaded Rilide v4.
Disguised as a Google Translate extension for web browsers, Rilide v4 operated discreetly in the background while siphoning sensitive data such as Facebook cookies and other information.
Although the specific page used in this scheme has been taken down, the threat actors have launched a new page that remains active. This page has amassed over 600,000 members and continues to distribute malware under the guise of a fake Midjourney site.
It seems that Cybercriminals have found a devious way to take advantage of the hype around AI technology by manipulating popular social media platforms.
It is best to stay alert of any AI-related ads or links, especially on Facebook.