GitVenom: Hundreds of GitHub Repositories Abused to Steal Cryptocurrency
A new malware campaign, dubbed GitVenom, is making headlines. It’s using hundreds of GitHub repositories. The attackers use them to trick users and download info-stealers. They also download remote access trojans (RATs) and clipboard hijackers. The goal is to steal cryptocurrency and credentials.
GitVenom’s Reach and Tactics
According to Kaspersky, GitVenom has been active for at least two years. It targets users globally. However, Russia, Brazil, and Turkey are seeing increased attacks.
“Over the course of the GitVenom campaign, the threat actors behind it have created hundreds of repositories on GitHub that contain fake projects with malicious code – for example, an automation instrument for interacting with Instagram accounts, a Telegram bot allowing to manage Bitcoin wallets, and a hacking tool for the video game Valorant,” describes Kaspersky’s Georgy Kucherin.
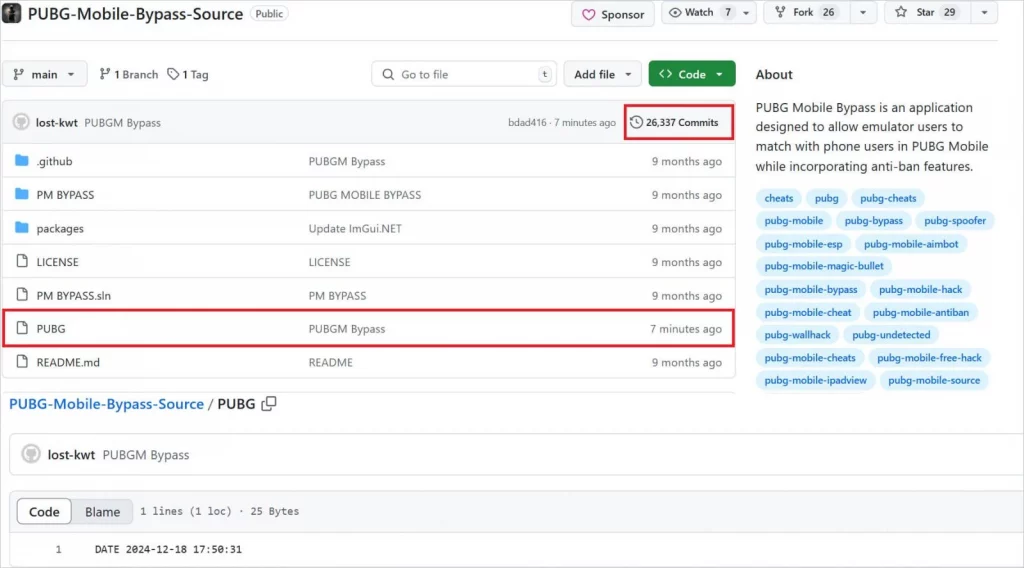
Fake GitHub repositories
Source: Kaspersky
The fake repositories are cleverly designed. They have detailed descriptions and well-written readme files. The attackers also inflate the number of commits. This creates a false sense of activity. It boosts credibility.
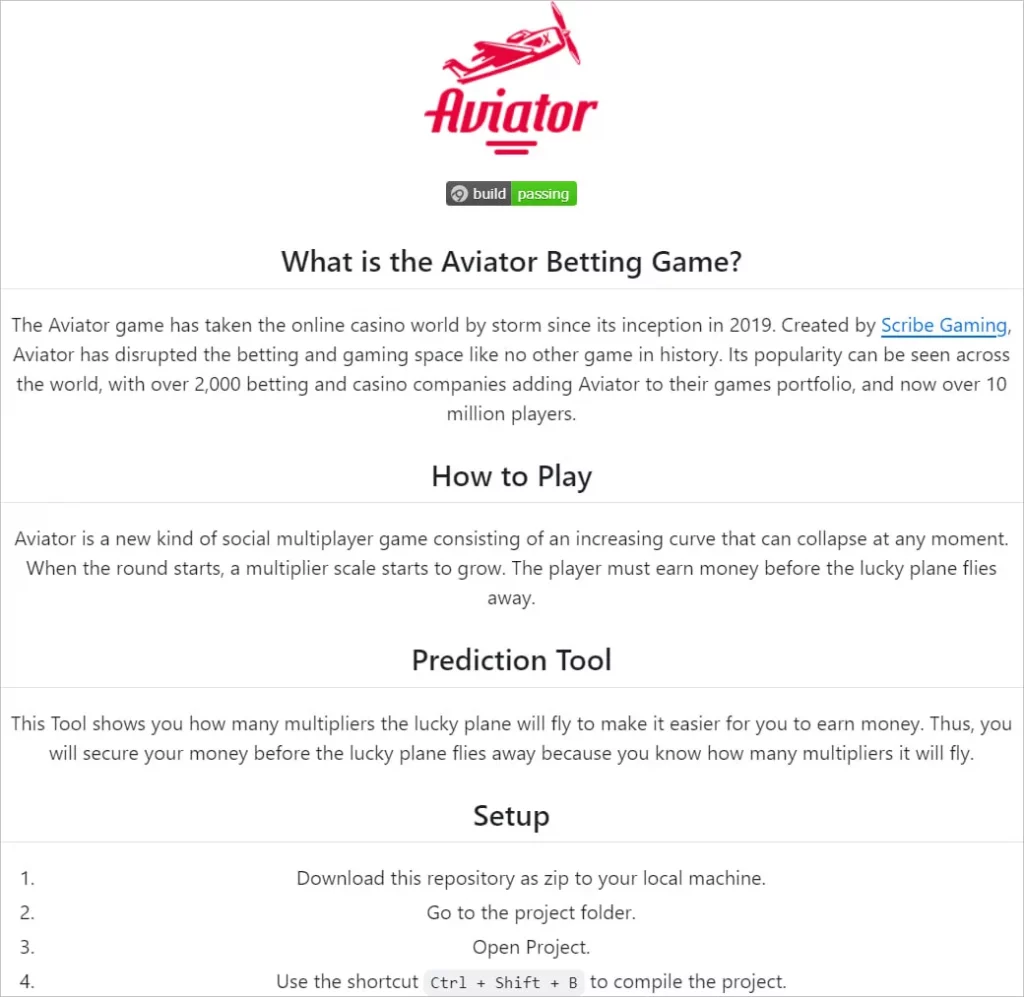
Readme file of a fraudulent project
Source: Kaspersky
Malicious Code and Payloads
The malicious code uses various programming languages. Python, JavaScript, C, C++, and C# are some of the languages used. This helps evade detection. When a victim runs the code, it downloads a second stage payload. This payload comes from an attacker-controlled GitHub repository.
Malware Used in GitVenom Attacks
Kaspersky’s research identified several tools used in GitVenom attacks:
- Node.js stealer: This info-stealer targets saved credentials, cryptocurrency wallet information, and browsing history. It compresses data and sends it via Telegram.
- AsyncRAT: An open-source RAT. It enables remote control, keylogging, screen capturing, file manipulation, and command execution.
- Quasar backdoor: Another open-source RAT. It has similar capabilities to AsyncRAT.
- Clipboard hijacker: This malware monitors the clipboard. It looks for cryptocurrency wallet addresses. It replaces them with an attacker-controlled address. This redirects funds to the hacker.
One attack in November 2024 resulted in 5 BTC being stolen. That’s worth about half a million USD.
Protecting Yourself from GitVenom
While malware hiding in GitHub isn’t new, GitVenom’s scale is concerning. It shows how effective platform abuse can be.
- Pre-use Inspection: Always carefully check any project before using its files.
- Repository Examination: Thoroughly inspect the repository’s contents.
- Antivirus Scan: Scan all files with updated antivirus software.
- Isolated Execution: Run downloaded files within an isolated environment (like a virtual machine).
- Suspicious Indicators: Be cautious of:
- Obfuscated code.
- Unusual or excessive automated commits.
- Excessively detailed readme files.
Read more about protecting yourself from ransomware attacks: Latest news Breaches, Hacks, & Protection Tips – Daily Security Review.









