An international police operation has dismantled the ransomware group known as Diskstation, which spent years targeting Synology NAS devices and disrupting businesses across Europe. The gang, traced to Romania, had encrypted the data of several organizations in Italy’s Lombardy region, demanding large cryptocurrency ransoms to unlock access.
The operation, codenamed “Elicius,” was coordinated by Europol in collaboration with Romanian and French law enforcement. It focused on a ransomware campaign that began in 2021 and operated under various aliases including “DiskStation Security,” “Quick Security,” “7even Security,” and “Umbrella Security.”
The attackers zeroed in on internet-exposed Network Attached Storage (NAS) devices—critical infrastructure used by businesses for centralized data storage and backups. Once compromised, files were encrypted and companies were held hostage until they paid ransoms ranging from $10,000 to several hundred thousand dollars.
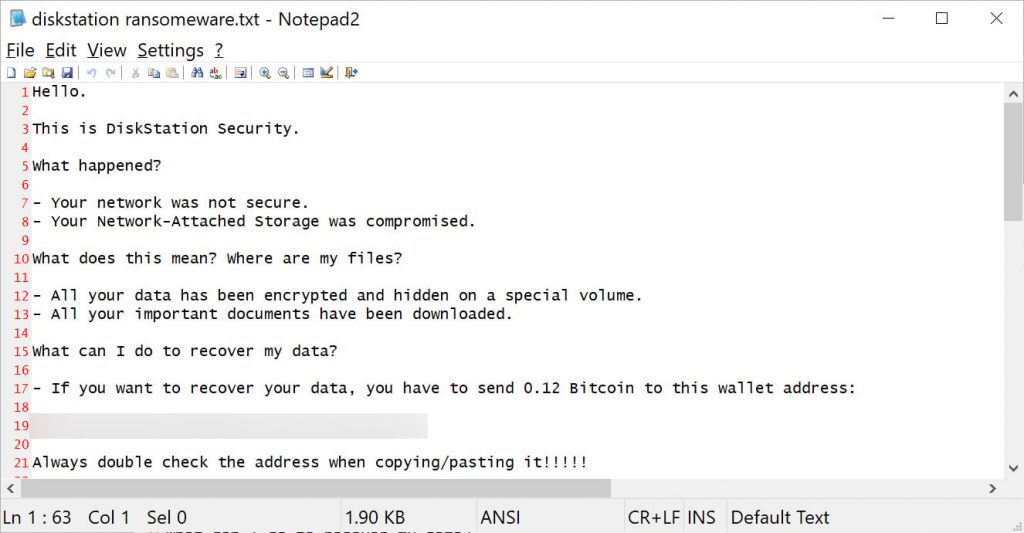
DiskStation ransom note
Source: BleepingComputer
“These companies had experienced encryption of data on their IT systems, resulting in the complete ‘paralysis’ of their production processes,” authorities stated.
“To regain access to their data and resume operations, the victims were required to pay a substantial ransom in cryptocurrency to the cybercriminals.”
Victims included graphic design studios, film production houses, event organizers, and international NGOs operating in civil rights and humanitarian sectors. Many reported the incidents to Italy’s Postal and Cybersecurity Police, triggering an investigation led by the Milan Prosecutor’s Office.
Authorities combined forensic analysis with blockchain tracking to trace the ransom payments. Within months, suspects were identified, leading to coordinated raids across multiple residences in Bucharest in June 2024.
A 44-year-old Romanian man believed to be the main operator behind the attacks was arrested during the raids. He remains in pre-trial detention and faces charges of unauthorized access to IT systems and extortion.
The Diskstation operation highlights the risks of leaving NAS devices unprotected online. Authorities recommend organizations:
- Regularly update NAS firmware
- Disable unused services like Telnet, rsync, and UPnP
- Avoid exposing devices directly to the internet
- Restrict access using secure VPNs
Although the primary actor is now in custody, the long-term damage caused by the campaign underscores the importance of securing backend infrastructure—especially for small and mid-sized businesses that rely heavily on NAS devices for operations and backups.









