The BlackBasta ransomware operation has developed an automated brute-forcing framework called “BRUTED” to compromise edge network devices such as firewalls and VPNs.
This tool allows BlackBasta to efficiently gain initial network access and scale its ransomware attacks against vulnerable internet-exposed endpoints.
EclecticIQ researcher Arda Büyükkaya discovered BRUTED while analyzing leaked internal chat logs from the ransomware gang. His findings confirm numerous reports from 2024 detailing large-scale brute-forcing and password spraying attacks against these types of devices, some of which may be linked to BRUTED or similar operations.
Büyükkaya reports that BlackBasta has used BRUTED since 2023 to conduct large-scale credential-stuffing and brute-force attacks. The framework targets specific VPN and remote access products:
- SonicWall NetExtender
- Palo Alto GlobalProtect
- Cisco AnyConnect
- Fortinet SSL VPN
- Citrix NetScaler (Citrix Gateway)
- Microsoft RDWeb (Remote Desktop Web Access)
- WatchGuard SSL VPN

Attack approach used for each product
Source: EclecticIQ
BRUTED searches for publicly accessible edge devices by enumerating subdomains, resolving IP addresses, and appending prefixes like “.vpn” or “remote.”
It reports findings to a command-and-control (C2) server. After identifying targets, BRUTED retrieves password candidates from a remote server and combines them with locally generated guesses. It then uses multiple CPU processes to execute numerous authentication requests.
Büyükkaya shared the source code revealing the tool’s use of specific request headers and user agents for each target to enhance its evasion capabilities.
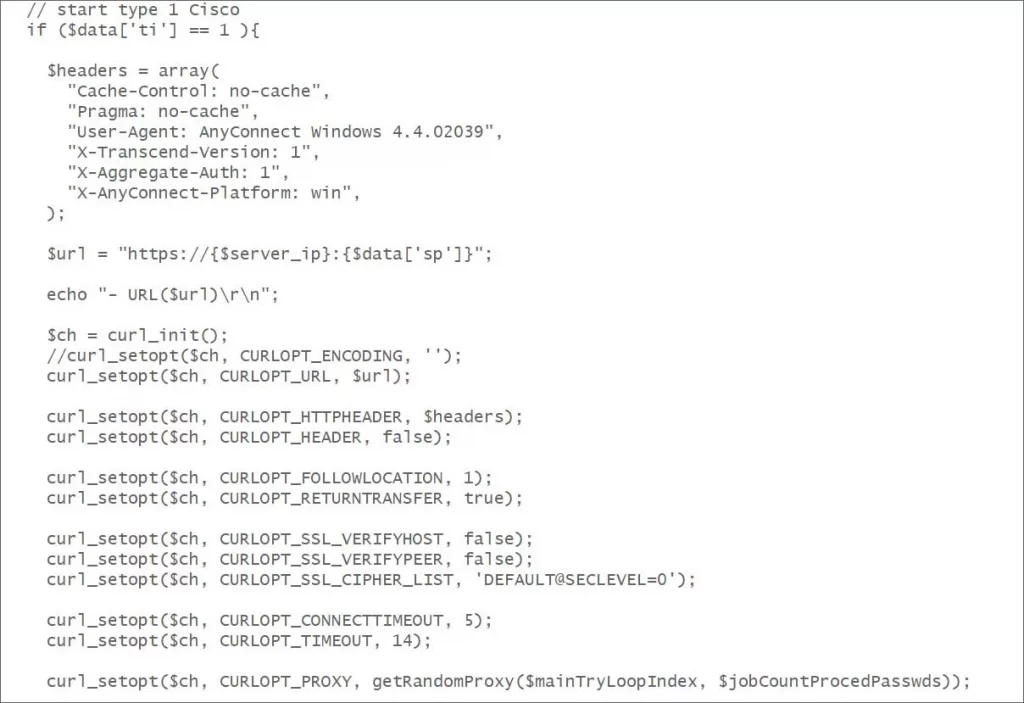
Source code for Cisco AnyConnect (ASA) brute force function
Source: BleepingComputer
The tool uses specific request headers and user agents for each target to avoid detection. It also extracts Common Name (CN) and Subject Alternative Names (SAN) from SSL certificates to generate additional password guesses.
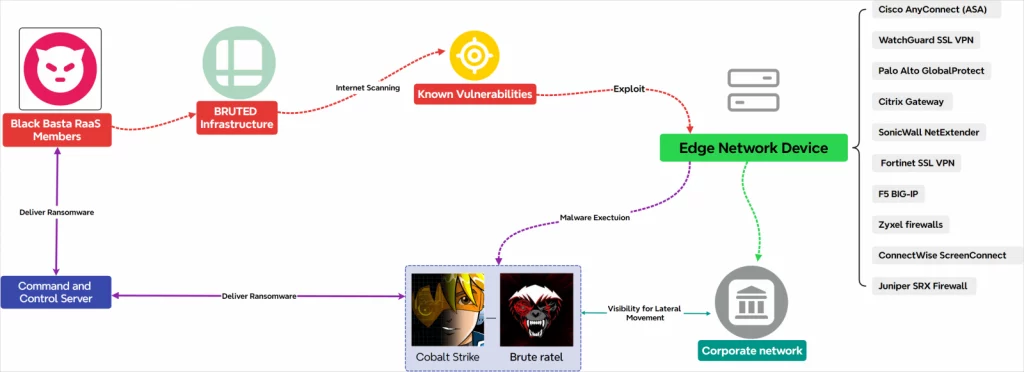
Black Basta attacks involving BRUTED
Source: EclecticIQ
BRUTED uses SOCKS5 proxies with an obfuscated domain name to hide its infrastructure. Its main infrastructure consists of multiple servers in Russia, registered under Proton66 (AS 198953).
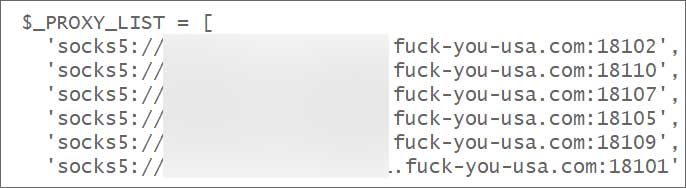
Proxy servers used by Black Basta’s BUSTED framework
Source: BleepingCoputer
Leaked chat logs even reveal discussions about server downtime due to unpaid fees, offering a glimpse into the ransomware gang’s operations.
To defend against such attacks, organizations should:
- Enforce strong, unique passwords for all edge devices and VPN accounts.
- Implement multi-factor authentication (MFA) to prevent access even if credentials are compromised.
- Monitor authentication attempts from unknown locations and high-volume login failures.
- Implement rate-limiting and account lockout policies.
- Keep edge devices updated with the latest security patches.
EclecticIQ has shared a list of IPs and domains used by BRUTED, which can be used to create firewall rules blocking requests from known malicious infrastructure. While BRUTED doesn’t exploit vulnerabilities, keeping devices updated remains critical.
The use of automated tools to target VPNs highlights the need for comprehensive security strategies, including strong password policies, MFA, and regular security audits. For more on protecting against such attacks, see our article on 9 Steps to Remove Malware from Your Windows PC.
Helpful Reads:









