The Scale of the WordPress Accounts Hack
A significant cybersecurity incident has unfolded, revealing a massive data breach affecting over 390,000 WordPress accounts. The attack, orchestrated by a threat actor tracked as MUT-1244, represents a sophisticated supply chain attack lasting a full year.
The sheer number of compromised WordPress accounts highlights the scale and impact of this campaign, which extended beyond typical targets to include security professionals and even other malicious actors. Researchers at Datadog Security Labs uncovered the details, shedding light on the methods and consequences of this extensive WordPress accounts hack.
The theft of WordPress credentials was not the only outcome; the attackers also successfully obtained SSH private keys and AWS access keys, significantly expanding the potential damage.
Technical Details of the Supply Chain Attack
The attackers employed a multi-pronged approach to compromise their victims. A key element of this supply chain attack involved the use of dozens of trojanized GitHub repositories. These repositories contained malicious proof-of-concept (PoC) exploits targeting known security vulnerabilities.
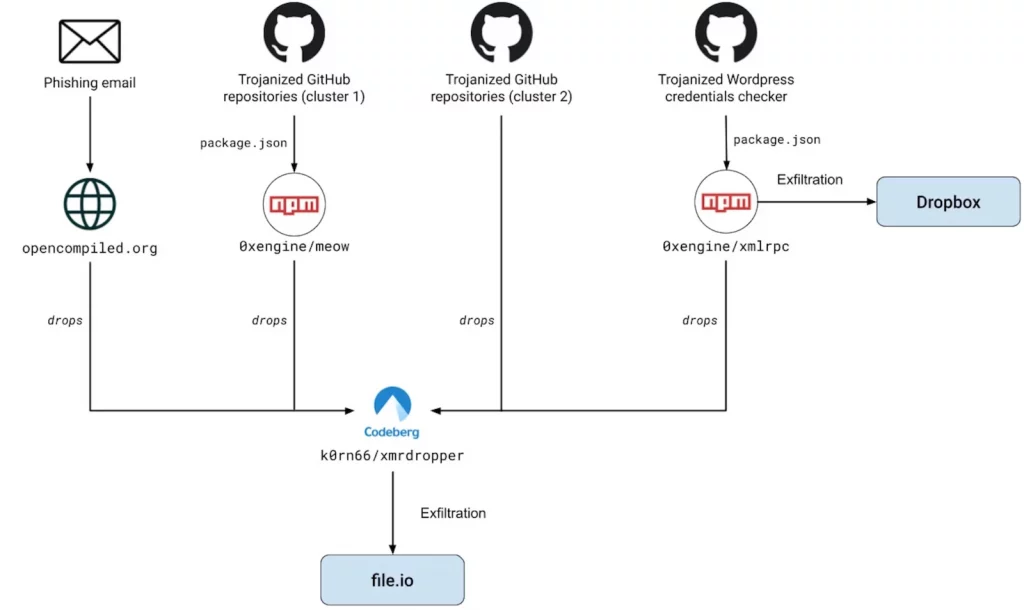
Attack flow (Datadog Security Labs)
The deceptive nature of these repositories was crucial to the success of the attack. By mimicking legitimate PoC exploits, MUT-1244 successfully tricked security professionals and other threat actors into downloading and executing the malicious code.
This highlights the risk of relying solely on publicly available code without careful vetting. The attackers also utilized a phishing campaign, distributing emails that appeared to offer a kernel upgrade disguised as a CPU microcode update. This cleverly disguised malware installation method further broadened the attack’s reach.
The payloads delivered through these compromised GitHub repositories and phishing emails were diverse, using various methods for code delivery. These included backdoored configure compilation files, malicious PDF files, Python droppers, and even malicious npm packages embedded within project dependencies.
This multifaceted approach demonstrated a high level of sophistication and resourcefulness on the part of MUT-1244. The attackers’ use of the “hpc20235/yawp” GitHub project, trojanized via a malicious “0xengine/xmlrpc” npm package, is a prime example of this strategy.
This specific attack, highlighted in a November Checkmarkx report, is directly linked to the broader MUT-1244 campaign, showcasing the longevity and adaptability of the threat actor’s methods.
The malware deployed by MUT-1244 included a cryptocurrency miner, allowing the attackers to profit from the compromised systems. More importantly, a backdoor was installed, enabling the exfiltration of sensitive data.
This backdoor facilitated the theft of private SSH keys, AWS credentials, environment variables, and key directory contents such as “~/.aws,” providing the attackers with extensive access to victims’ systems and cloud resources. The second-stage payload, hosted on a separate platform, further aided data exfiltration, utilizing file-sharing services like Dropbox and file.io. Hardcoded credentials for these services were embedded within the payload itself, giving MUT-1244 direct and easy access to the stolen information.
Impact and Analysis of the WordPress Accounts Hack
“MUT-1244 was able to gain access to over 390,000 credentials, believed to be WordPress ones. We assess with high confidence that before these credentials were exfiltrated to Dropbox, they were in the hands of offensive actors, who likely acquired them through illicit means,” stated Datadog Security Labs researchers.
This statement highlights the layered nature of the attack, suggesting that MUT-1244 leveraged pre-existing stolen credentials, likely purchased from underground markets, to further expand their reach and validate the stolen WordPress accounts. The use of the “yawpp” tool, advertised as a WordPress credential checker, allowed the attackers to efficiently verify the validity of the acquired credentials.
The success of this campaign underscores the vulnerability of the cybersecurity community itself. MUT-1244 successfully exploited trust within the community, compromising systems belonging to both white hat and black hat hackers. This highlights the importance of vigilance and critical thinking, even among experienced security professionals.
The attackers’ ability to target both ethical and malicious actors demonstrates the indiscriminate nature of this supply chain attack. Datadog Security Labs estimates that hundreds of systems remain compromised, with the ongoing nature of the campaign suggesting that further infections are likely.
The implications of this widespread breach extend far beyond the immediate victims, potentially impacting numerous organizations and individuals. The theft of AWS credentials, in particular, poses a significant risk, potentially allowing access to sensitive cloud-based data and resources.
The use of trojanized GitHub repositories, phishing campaigns, and sophisticated malware highlights the need for constant vigilance and proactive security measures to mitigate the risk of similar supply chain attacks targeting WordPress accounts and other critical systems.









