A critical Windows zero-day exploit, tracked internally by Trend Micro as ZDI-CAN-25373, has been actively exploited by at least 11 state-backed hacking groups since 2017. These groups, originating from North Korea, Iran, Russia, and China, have leveraged this vulnerability for data theft and cyber espionage.
The vulnerability, a User Interface (UI) Misrepresentation of Critical Information (CWE-451), allows attackers to manipulate how Windows displays shortcut (.lnk) files. This allows malicious code execution without the user’s knowledge.
Attackers hide malicious command-line arguments within .LNK files using padded whitespaces, cleverly masking them from the user’s view in the Windows interface. These whitespaces can be various hex codes representing different whitespace characters.
Security researchers Peter Girnus and Aliakbar Zahravi from Trend Micro’s Zero Day Initiative (ZDI) reported that Microsoft declined to patch this vulnerability, citing it as “not meeting the bar servicing.”
They stated, “We discovered nearly a thousand Shell Link (.lnk) samples that exploit ZDI-CAN-25373; however, it is probable that the total number of exploitation attempts are much higher.”
The researchers submitted a proof-of-concept exploit through Trend ZDI’s bug bounty program, but Microsoft’s response was to decline to issue a security patch.
The widespread attacks involved various state-sponsored threat groups and cybercrime gangs, including Evil Corp, APT43 (Kimsuky), Bitter, APT37, Mustang Panda, SideWinder, RedHotel, Konni, and others.
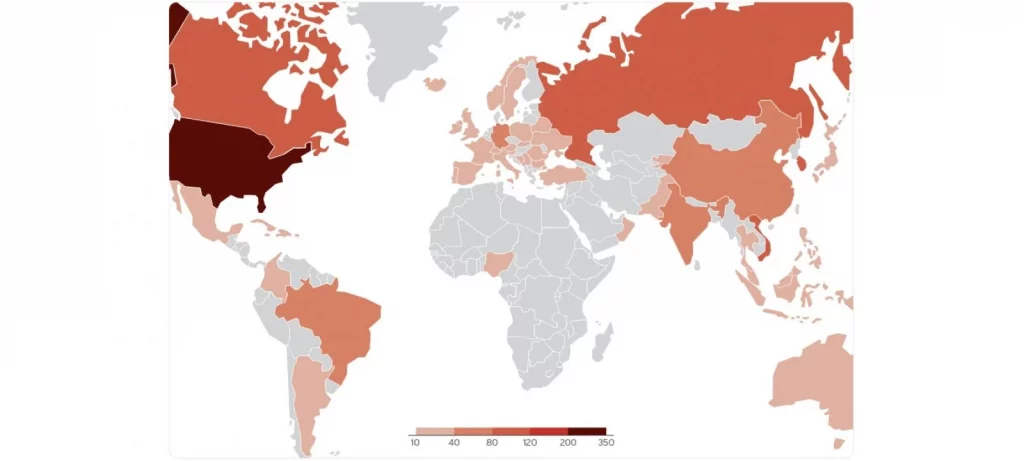
Map of countries targeted in ZDI-CAN-25373 attacks
Source: (Trend Micro)
While victims worldwide were targeted, the attacks primarily focused on North America, South America, Europe, East Asia, and Australia. A significant portion (nearly 70%) of these attacks were linked to espionage and information theft, with only 20% focused on financial gain.
Diverse malware payloads and loaders, such as Ursnif, Gh0st RAT, and Trickbot, were observed in these campaigns. The use of malware-as-a-service (MaaS) platforms further complicates the threat landscape.
5/7 Diverse malware payloads and loaders like Ursnif, Gh0st RAT, and Trickbot have been tracked in these campaigns, with malware-as-a-service (MaaS) platforms complicating the threat landscape. pic.twitter.com/tvR1s6kSCy
— Trend Micro Research (@TrendMicroRSRCH) March 18, 2025
“We appreciate the work of ZDI in submitting this report under a coordinated vulnerability disclosure. Microsoft Defender has detections in place to detect and block this threat activity, and the Smart App Control provides an extra layer of protection by blocking malicious files from the Internet. As a security best practice, we encourage customers to exercise caution when downloading files from unknown sources as indicated in security warnings, which have been designed to recognize and warn users about potentially harmful files. While the UI experience described in the report does not meet the bar for immediate servicing under our severity classification guidelines, we will consider addressing it in a future feature release.”
Microsoft spokesperson said in a statement
This Windows zero-day exploit is similar to CVE-2024-43461, which used encoded braille whitespace characters to camouflage malicious HTA files. That vulnerability was patched by Microsoft in September 2024.
The exploitation of ZDI-CAN-25373 highlights the ongoing challenge of zero-day vulnerabilities and the importance of robust security practices for enterprise businesses.
This vulnerability underscores the critical need for proactive security measures, including multi-factor authentication and careful scrutiny of downloaded files. Learn more about mitigating similar threats by reading our guide on Top Cyber Threats Facing Enterprise Businesses in 2025.