The RansomHouse ransomware group recently developed a tool called ‘MrAgent’ for VMware ESXi attacks and streamline the deployment of their data encrypter on multiple VMware ESXi hypervisors.
RansomHouse operates as a ransomware-as-a-service (RaaS) and has been active since December 2021, employing double extortion techniques.
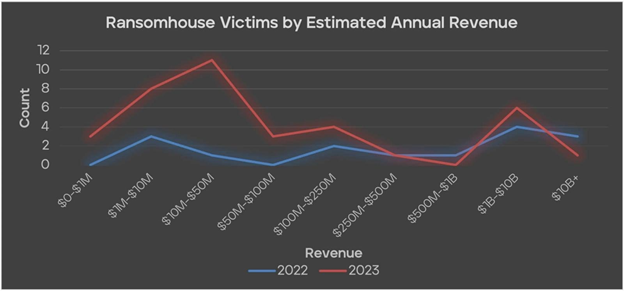
In May 2022, they established a dedicated victim extortion page on the dark web. While not as notorious as other cybercriminal organizations like LockBit, ALPHV/Blackcat, Play, or Clop, RansomHouse primarily targeted large organizations throughout the previous year, according to Trellix’s reports.
RansomHouse Target VMware ESXi Servers to Target VMs Using MrAgent Tool
Ransomware groups specifically target ESXi servers for VMs, which often store valuable data that can be exploited during the extortion process. Additionally, ESXi servers play a crucial role in running essential business applications and services such as databases and email servers, amplifying the impact of a ransomware attack on operations.
Source: (Trellix)
Analysts from Trellix have identified a new binary utilized by the RansomHouse group, which seems to be specifically tailored to streamline their attacks on ESXi systems.
The MrAgent Tool Is Highly Capable and Versatile Ransomware Tool
MrAgent serves as the central component of the tool, responsible for identifying the host system and disabling its firewall. It then automates the deployment of the ransomware across multiple hypervisors simultaneously, compromising all the managed virtual machines (VMs).
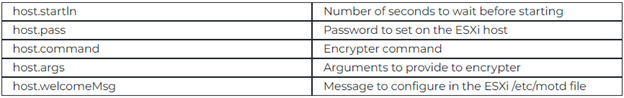
The tool is designed to accommodate customized configurations for ransomware deployment, which are received directly from the command and control (C2) server.
These configurations encompass various settings, such as password management on the hypervisor, customization of the encrypter command and its associated parameters, scheduling encryption events, and modifying the welcome message displayed on the hypervisor’s monitor to show a ransom notice.
Furthermore, MrAgent enables the execution of local commands on the hypervisor, as directed by the command and control (C2) server. These commands can involve tasks like file deletion, termination of active SSH sessions to prevent interference during the encryption process, and gathering information about the running virtual machines (VMs).
MrAgent configuration (Trellix)
By disabling the firewall and potentially terminating non-root SSH sessions, MrAgent reduces the likelihood of detection and intervention by administrators. Simultaneously, it intensifies the impact of the attack by targeting all accessible VMs simultaneously.
According to Trellix, a Windows version of MrAgent maintains the core functionality of the tool but includes adaptations specific to the Windows operating system, such as utilizing PowerShell for certain tasks.
The utilization of MrAgent across different platforms demonstrates RansomHouse’s objective to expand the tool’s versatility and enhance the effectiveness of their campaigns, particularly when targeting organizations that utilize both Windows and Linux systems.
“The efforts to (further) automate the steps that are otherwise often executed manually shows both the interest and willingness of the attacking affiliate to target large networks,”
Trellix says in the report.
The security implications of tools like MrAgent are severe, so defenders must implement comprehensive and robust security measures, including regular software updates, strong access controls, network monitoring, and logging to defend against such threats.