LockBit ransomware returns with New and Improved encryptors and resumes their attacks with updated encryption ransom notes that direct victims to new servers.
This comes shortly after a joint effort by the NCA, FBI, and Europol, known as ‘Operation Cronos‘, to disrupt the LockBit ransomware operation. During this operation, law enforcement successfully seized infrastructure, recovered decryptors, and even transformed the ransomware gang’s data leak site into a police press portal, causing embarrassment for LockBit.
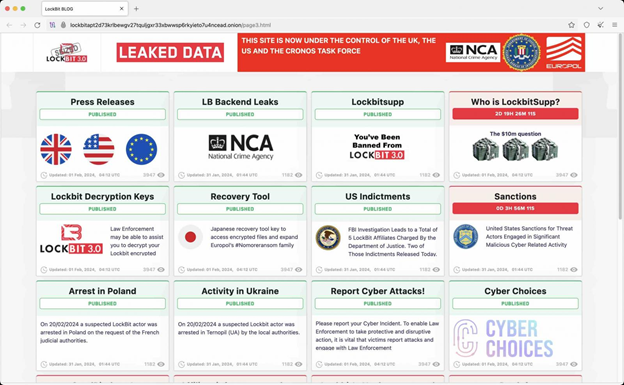
LockBit data leak site converted into a press site
Source: BleepingComputer
Following the incident, LockBit promptly established a fresh data leak site and issued a lengthy message directed at the FBI. In their communication, they alleged that law enforcement had exploited a PHP vulnerability to breach their servers.
However, rather than undergoing a complete rebranding, LockBit vowed to make a comeback with enhanced infrastructure and fortified security measures. Their objective is to thwart future operation-wide attacks by law enforcement and prevent them from obtaining decryptors.
LockBit Ransomware Returns with New LockBit Encryptors
The LockBit ransomware gang has returned and made a comeback with new encryptors and established fresh infrastructure for their data leak and negotiation sites.
This information was initially reported by Zscaler, who discovered that the ransom notes accompanying the updated encryptors now include Tor URLs pointing to LockBit’s new infrastructure.
These findings have been corroborated by samples of the encryptors uploaded to VirusTotal on both yesterday
Sample and today Sample(shared by MalwareHunterTeam).
It is also confirmed that the negotiation servers for the operation have become operational once again, but they are only accessible to victims of new attacks.
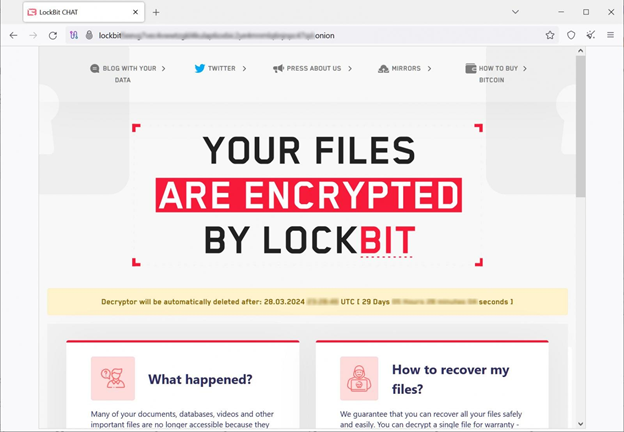
New LockBit negotiation sites
Source: BleepingComputer
During the time of LockBit’s disruption, the ransomware operation had an estimated 180 affiliates engaged in carrying out attacks.
The current status of these affiliates and their continued association with the Ransomware-as-a-Service remains uncertain, as one individual publicly expressed their dissatisfaction with the operation on X platform.
However, LockBit has publicly stated that they are actively seeking experienced pentesters to join their ranks once again, indicating a potential increase in future attacks. It remains unclear whether LockBit intends to gradually fade away and rebrand, similar to what was observed with Conti.
Nonetheless, it is advisable to consider LockBit as an ongoing threat for the time being.









