Nexperia, a Dutch chipmaker, recently confirmed that its network was compromised by hackers in March 2024. The breach came to light after a ransomware gang leaked some of the allegedly stolen data.
Nexperia, a subsidiary of Wingtech Technology, a Chinese company, operates semiconductor fabrication plants in Germany and the UK. They are known for producing a wide range of electronic components such as transistors, diodes, MOSFETs, and logic devices, with an impressive output of 100 billion units.
The company is headquartered in Nijmegen and has a workforce of 15,000 specialists, generating an annual revenue exceeding $2.1 billion.
In response to the Nexperia data breach, Nexperia has taken immediate action by shutting down its IT systems and initiating an investigation to assess the extent of the impact.
“Nexperia has become aware that an unauthorized third party accessed certain Nexperia IT servers in March 2024,”
“We promptly took action and disconnected the affected systems from the internet to contain the incident and implemented extensive mitigation.”
“We also launched an investigation with the support of third-party experts to determine the nature and scope of the incident and took strong measures to terminate the unauthorized access.”
Reads the statement.
Nexperia promptly reported the incident to both the police and data protection authorities in the Netherlands. Additionally, they have engaged the services of FoxIT to assist in the ongoing investigations.
Dunghill Leaks Claims the Nexperia Data Breach
On April 10, an extortion site named ‘Dunghill Leak’ made the announcement that it had successfully breached Nexperia.
According to their claim, the hackers managed to obtain 1 TB of confidential data and released a sample of the alleged stolen files.
The leaked data included microscope scans of electronic components, employee passports, non-disclosure agreements, and other miscellaneous samples. However, the authenticity of these materials has not yet been confirmed by Nexperia.
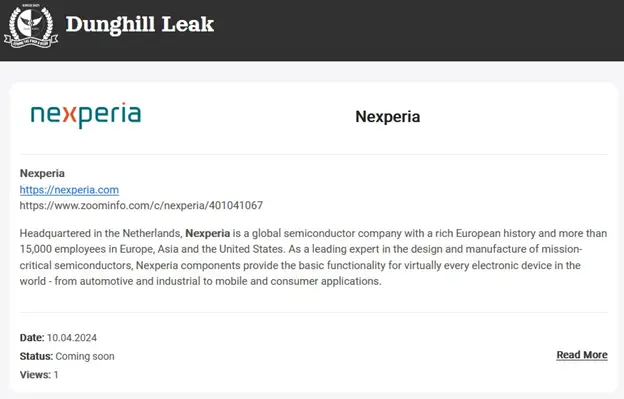
Nexperia added to the Dunghill Leak extortion site
Source: BleepingComputer
If the ransom demand is not met, Dunghill plans to release the following data:
• 121.1 GB of various files and miscellaneous data, including email storage files.
• 109 GB of client and user data, including brands such as SpaceX, IBM, Apple, and Huawei.
• 96 GB of commercial and marketing data, including pricing and marketing analysis.
• 41.5 GB of corporate data, including HR, employee personal details, passports, NDAs, etc.
• 246 GB of engineering data, including internal studies and manufacturing technologies.
• 371 GB of design and product data, including QC, NDAs, trade secrets, technical specifications, confidential schematics, and production instructions.
The Dunghill Leak site has been attributed to the Dark Angels ransomware gang, known for using the platform to coerce targeted organizations into paying ransoms.
In a ransom note, the threat actors issued a warning that failure to meet their extortion demands would result in the publication of the stolen data on the Dunghill Leak website. However, it appears that this threat has not been carried out.
Currently, the Dunghill Leak extortion site displays a list of twelve victims. Among them, data for eight has been either fully or partially released, while two are marked as ‘sold on the dark web.’