WhatsApp has successfully patched a critical zero-click vulnerability that was exploited to install Paragon spyware on targeted devices. This flaw, identified by researchers at the University of Toronto’s Citizen Lab, allowed attackers to compromise user devices without any interaction from victims.
Details of the Vulnerability and Attack
The zero-click exploit, which WhatsApp addressed late last year, did not require any client-side fixes. The company opted not to assign a CVE-ID after reviewing guidelines from MITRE and its internal policies.
A WhatsApp spokesperson stated, “WhatsApp has disrupted a spyware campaign by Paragon that targeted a number of users including journalists and members of civil society. We’ve reached out directly to people who we believe were affected.”
On January 31, WhatsApp notified approximately 90 Android users across more than two dozen countries. Notably, this group included Italian journalists and activists targeted with Paragon spyware to extract sensitive data and intercept private communications.

Graphite Android spyware’s zero-click exploit (Citizen Lab)
Attack Methodology of Paragon Spyware
Citizen Lab’s investigation revealed that attackers would add targets to a WhatsApp group and send a PDF file. The victim’s device would then automatically process this PDF, leveraging the now-patched zero-day vulnerability to install a Graphite spyware implant within WhatsApp. Once installed, the spyware could escape the Android sandbox, compromising other applications on the device and granting operators access to the victims’ messaging platforms.
“The 90-some targets notified by WhatsApp likely represent a fraction of the total number of Paragon cases. Yet, in the cases already investigated, there is a troubling and familiar pattern of targeting human rights groups, government critics, and journalists,” Citizen Lab noted.
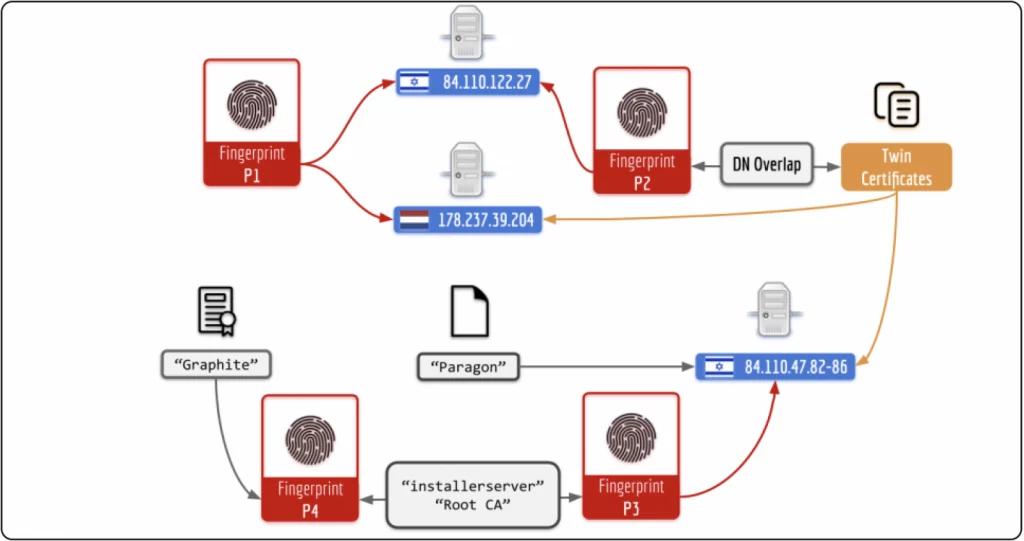
Fingerprinting Paragon infrastructure (Citizen Lab)
Detection of Paragon Spyware Using BIGPRETZEL
Graphite spyware infections can be detected on compromised Android devices through a forensic artifact known as BIGPRETZEL. However, the sporadic nature of Android logs means that evidence of infection might be overwritten or not captured.
Citizen Lab also mapped the server infrastructure used by Paragon to deploy Graphite spyware, finding connections to multiple government customers, including Australia, Canada, Cyprus, Denmark, Israel, and Singapore. They identified 150 digital certificates linked to this infrastructure.
“This infrastructure included cloud-based servers likely rented by Paragon and/or its customers, as well as servers likely hosted on the premises of Paragon and its government customers,” stated Citizen Lab.
Company Background and Questionable Ethical Practices
Founded in 2019 by former Israeli Prime Minister Ehud Barak and ex-commander of Unit 8200, Ehud Schneorson, Paragon Solutions Ltd. claims to sell its surveillance tools exclusively to law enforcement and intelligence agencies in democratic nations. In December 2022, the New York Times reported that the U.S. Drug Enforcement Administration (DEA) utilized the company’s Graphite spyware.
In a significant development, Wired reported in October 2024 that Paragon signed a $2 million contract with the U.S. Immigration and Customs Enforcement (ICE).
WhatsApp’s prompt action to patch this zero-day vulnerability highlights the ongoing battle against spyware threats that target vulnerable individuals, including journalists and activists. As the landscape of cyber threats evolves, the need for robust security measures becomes increasingly critical.









