Schneider Electric ransomware attack has been claimed by Cactus ransomware. The attackers stole valuable corporate data from Sustainability Business division.
Schneider Electric Ransomware Attack
Schneider Electric, a leading company in energy management and automation, recently experienced a ransomware attack known as Cactus. As a result, valuable corporate data was stolen. The attack specifically targeted the Sustainability Business division on January 17th.
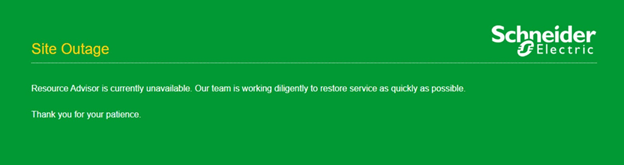
Consequently, the Resource Advisor cloud platform, operated by Schneider Electric, has been experiencing ongoing disruptions and outages.
During the Cactus ransomware attack on Schneider Electric, the cybercriminals managed to steal a significant amount of corporate data, estimated to be in terabytes. They are now using this stolen data as leverage to extort the company, threatening to release it unless a ransom is paid.
Details of Cactus Ransomware Attack on Schneider Electric
The specific nature of the stolen data remains undisclosed. However, it is worth noting that the Sustainability Business division of Schneider Electric primarily offers consulting services to enterprise organizations. These services involve providing guidance on renewable energy solutions and assisting clients in navigating complex climate regulatory requirements on a global scale.
Notable customers of Schneider Electric’s Sustainability Business division include Allegiant Travel Company, Clorox, DHL, DuPont, Hilton, Lexmark, PepsiCo, and Walmart.
The stolen data from Schneider Electric’s cyberattack could potentially include sensitive information regarding customers’ power utilization, industrial control and automation systems, as well as their compliance with environmental and energy regulations.
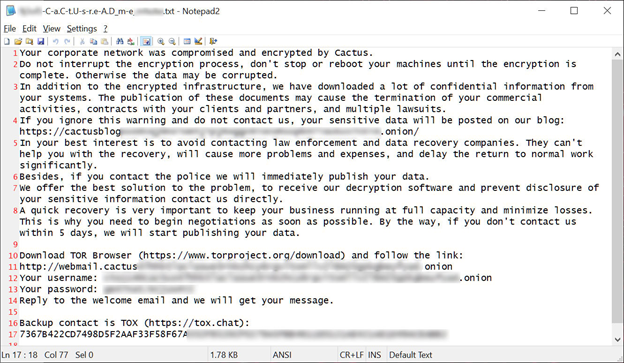
At this point, it is uncertain whether Schneider Electric will comply with the ransom demand. However, if the company chooses not to pay, it is highly likely that the ransomware gang will follow their previous pattern and proceed to leak the stolen data.
In a statement to BleepingComputer, Schneider Electric confirmed that its Sustainability Business division suffered a cyberattack and that data was accessed by the threat actors. However, the company says the attack was restricted to this one divisiion and did not impact other parts of the company.
About Schneider Electric
Schneider Electric, a global company with over 150,000 employees, achieved $28.5 billion in revenue during the first nine months of 2023. The company is anticipated to announce its full-year financial results for 2023 in the coming month.
Schneider Electric is recognized for its popular consumer brands such as Homeline, Square D, and APC, known for their widely used uninterruptible power supply (UPS) devices.
It is worth noting that Schneider Electric has faced previous cyberattacks. The company was targeted by the Clop ransomware gang in the past, as part of the widespread MOVEit data theft attacks. These attacks impacted more than 2,700 companies.
Origins of Cactus Ransomware
The Cactus ransomware operation emerged in March 2023 and has since targeted multiple companies, alleging successful breaches in cyberattacks.
Similar to other ransomware operations, the threat actors behind Cactus employ various techniques to infiltrate corporate networks. These methods include acquiring credentials through illicit means, collaborating with malware distributors, executing phishing attacks, and exploiting vulnerabilities.
Once inside a network, the threat actors operate covertly, navigating through different systems while simultaneously exfiltrating valuable corporate data stored on servers.
Upon successfully stealing the data and attaining administrative privileges within the network, the threat actors proceed to encrypt files and leave ransom notes as evidence of their intrusion.
These Cactus ransomware threat actors employ a strategy known as double-extortion attacks, where they demand a ransom in exchange for both a file decryptor and a promise to destroy the stolen data, ensuring it will not be leaked.
If a company refuses to pay the ransom, the threat actors resort to leaking the stolen data on a designated data leak site. Presently, over 80 companies are listed on Cactus’ data leak site, indicating that their data has either been leaked or is at risk of being exposed by the threat actors.