A ransomware group calling itself Lynx has posted a note on its dark-web leak site claiming it stole sensitive data from True World Group LLC, the United States’ largest sushi and seafood supplier. The post — a familiar pressure tactic used by extortion gangs — includes screenshots of what the group says are stolen documents. If authentic, the disclosures raise the possibility that True World is confronting a fresh breach or at least renewed exposure of material tied to an earlier incident.
Details of the Leaked Data
The Lynx leak page does not publish a neat inventory or scope, but the shared images and samples suggest possession of highly sensitive corporate materials. Among the artifacts shown are financial records and invoices that include transaction line items and sums, along with personnel files and other employee information. Cybernews researchers who inspected the samples note that while some of the documents mirror material from the company’s 2024 disclosure, a subset is dated in 2025 — a detail that raises questions about whether the files reflect a new compromise, ongoing access, or simply recycled data.
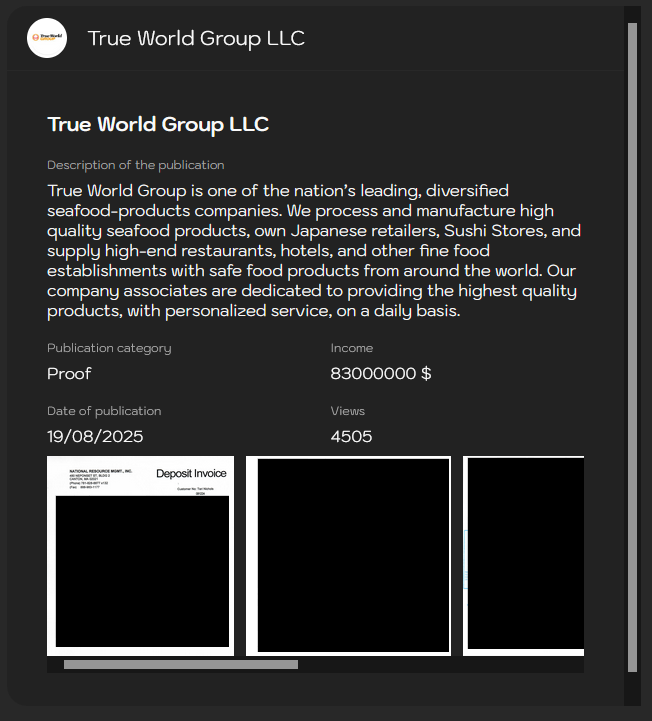
The gang’s public posting is short on technical detail but long on implication: screenshots are often enough to demonstrate possession and to increase pressure on a target to negotiate — or to silence speculation by prompting a corporate response.
History of the 2024 Incident
This would not be True World’s first public-facing security scare. In 2024, True World Holdings LLC notified more than 8,500 people that their personal data had been exposed after threat actors breached company systems and copied files containing current and former employee information. That earlier disclosure left a footprint: identity and personnel data had circulated in crime forums and prompted remediation outreach. The recurrence of similar documents — or of the same documents resurfacing with more recent timestamps — complicates the narrative for investigators and for affected individuals.
Potential Consequences for Business and Staff
Cybersecurity analysts warn that leaked commercial and employee records have several practical consequences. “The leaked data could be used by competitors to gather business intelligence data. Employee data could be used for identity theft, targeted phishing attacks,” the research team explained. Financial documents and invoices can be mined for vendor relationships, pricing, and payment flows; combined with employee records, they become fodder for highly convincing social-engineering campaigns. For a supplier embedded deeply in the food-service chain, such transparency can damage negotiations, expose pricing strategies, and create downstream risk for partners.
Who Is Lynx Ransomware?
Lynx surfaced in mid-2024 and operates as a ransomware-as-a-service (RaaS) operation, providing its malware and leak infrastructure to affiliates who carry out intrusions. The gang is known to target organizations across finance, architecture, and manufacturing verticals; security vendor Darktrace’s researchers have also linked Lynx-attributed activity to energy and retail incidents across the Middle East and Asia-Pacific regions. Cybernews’ monitoring tool Ransomlooker has cataloged dozens — and, by some counts, nearly two hundred — victims since 2024, placing Lynx among the more visible active ransomware groups.
Unit42 researchers observed that Lynx’s malware reuses significant portions of INC ransomware source code, suggesting the group adapted existing code to create its own strain rather than building everything from scratch. The gang’s roster of alleged victims includes high-profile organizations such as Dollar Tree, poultry producer Rose Acre Farms, and the CBS affiliate WDEF-TV. (Separately, INC ransomware has been tied to other incidents, including attacks on a Canadian cemetery and the city of Gardendale, Alabama.)
Lynx appears to recruit on Russian-language underground forums and publicly states it will not target organizations inside Russia or other CIS countries — a common posture among Russian-linked cybercrime groups that both limits local law-enforcement friction and signals a geopolitical boundary to operations. On its leak site, Lynx asserts a code of conduct, claiming it avoids hitting government bodies, hospitals, or nonprofits “because these sectors play vital roles in society,” and adding that “our operational model encourages dialogue and resolution rather than chaos and destruction.”
True World Group at a Glance
True World and its subsidiaries operate across food service and retail: they manage Japanese restaurants and grocery chains, run brands such as Noble Fish and White Wolf Japanese Patisserie, and operate a fleet of fishing vessels that supply fresh product to restaurants and grocers. The conglomerate employs around 1,000 people worldwide and plays a notable role in the U.S. seafood supply chain.
True World is affiliated with the Unification Church, the controversial religious movement founded in South Korea by Sun Myung Moon. That institutional connection has previously attracted public attention and plays a role in the conglomerate’s governance and public profile — a detail that sometimes colors how incidents are covered and discussed in media reports.
What Comes Next
Cybernews has reached out to True World Group for confirmation and comment, but at the time of reporting the company had not issued a public response. For suppliers deeply embedded in restaurant and grocery supply chains, even a perception of compromised records — whether newly stolen or re-published from past incidents — can trigger commercial fallout, regulatory scrutiny, and increased fraud risk for employees and partners. Whether Lynx’s latest post represents a true fresh breach or a re-surfacing of older material, the disclosures underscore the persistent risks that ransomware and leak-site theatrics pose to complex supply-chain businesses.









