More than 40 malicious browser extensions impersonating popular cryptocurrency wallets have been discovered in the official Firefox add-ons store, actively stealing user credentials and wallet seed phrases. The campaign, which has been ongoing since at least April, is believed to be the work of a Russian-speaking cybercriminal group.
Fake Extensions Pose as Trusted Wallet Brands
Researchers at Koi Security uncovered dozens of malicious Firefox add-ons masquerading as legitimate crypto wallet plugins. These include impersonations of well-known wallets such as:
- MetaMask
- Coinbase Wallet
- Trust Wallet
- Phantom
- OKX
- Exodus
- Keplr
- MyMonero
The fake extensions replicate the look and functionality of their legitimate counterparts by cloning open-source versions and adding malicious scripts. Once installed, the add-ons silently capture sensitive user data, especially seed phrases, and exfiltrate it to attacker-controlled servers.
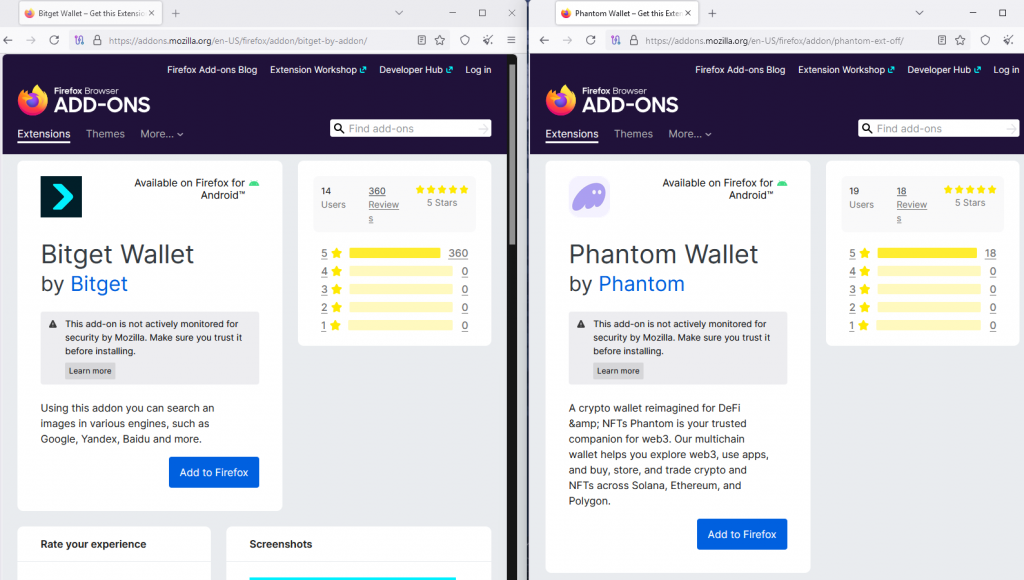
Fake wallet extensions on the Firefox add-ons store
Source: BleepingComputer
How the Attack Works
The attackers use JavaScript event listeners to monitor input fields. Any input string longer than 30 characters is flagged as a potential wallet key or seed phrase — a critical recovery component in crypto wallets. The stolen data is then transmitted to the attacker’s infrastructure, all while keeping the user unaware.
“The extensions suppress any visual error indicators by setting the dialog box opacity to zero, making the theft completely invisible to the victim,” explained Koi Security.
To increase trust, the fake extensions use official brand logos and fake five-star reviews. In some cases, the number of reviews far exceeds the number of installs, a red flag that less-attentive users might miss. Many of these extensions also include real-looking UIs, further masking their malicious intent.
Mozilla’s Response and Risk Mitigation
Mozilla has acknowledged the issue and said it is working to strengthen its defenses against crypto-targeted threats.
“We are aware of attempts to exploit Firefox’s add-ons ecosystem using malicious crypto-stealing extensions,” Mozilla stated. “Many of the extensions mentioned in the report had already been removed by Mozilla’s add-ons review team before publication, as well as dozens of others.”
Mozilla has implemented automated detection systems that trigger human review based on risk indicators. However, despite these efforts, some of the extensions highlighted by Koi Security remain available for download.
At the time of discovery, Koi Security used Firefox’s official reporting tool to flag the malicious add-ons. Yet, the persistence of these fake wallets in the store shows that the threat is not fully contained.
Crypto Theft as a Growing Supply Chain Threat
This campaign underscores how browser ecosystems — particularly through extensions and plugins — have become an overlooked but potent attack surface. For crypto users and platforms handling digital assets, these browser-level compromises function like supply chain attacks. The theft of seed phrases is often irreversible, with transactions appearing legitimate on the blockchain.
To reduce the risk:
- Avoid installing wallet extensions from browser stores.
- Use official sites or repositories to obtain plugins.
- Be wary of mismatched review counts and unclear developer profiles.
Recovery After a Breach
For enterprises supporting cryptocurrency operations or handling sensitive financial data through browser-based tools, this incident highlights the importance of rapid recovery. If credentials are compromised and systems are manipulated, businesses must act fast to isolate damage and restore safe configurations.
Looking for a trusted recovery solution?
Defend your organization with StoneFly DR365—an air-gapped, immutable backup and recovery appliance trusted by enterprises to ensure zero data loss even in the event of complex cyberattacks.