ClickFix, a growing social engineering technique, is now being used by multiple state-sponsored hacking groups in cyber-espionage operations. Recent reports link the tactic to APT groups from North Korea, Iran, and Russia, signaling a broader adoption of the method across nation-state actors.
ClickFix: How the Social Engineering Technique Works
ClickFix attacks begin when a target is tricked into visiting a malicious site that mimics legitimate services such as software portals or cloud storage platforms.
- Victims are often led to these sites via phishing emails or malvertising.
- The site displays a fake error message, claiming a download or document failed.
- A “Fix” button appears, prompting the user to manually run a PowerShell or command-line command.
- Once executed, the command downloads and launches malware on the victim’s device.
Microsoft previously observed this tactic used by Kimsuky, a North Korean group, as part of a fake device registration page in early 2025.
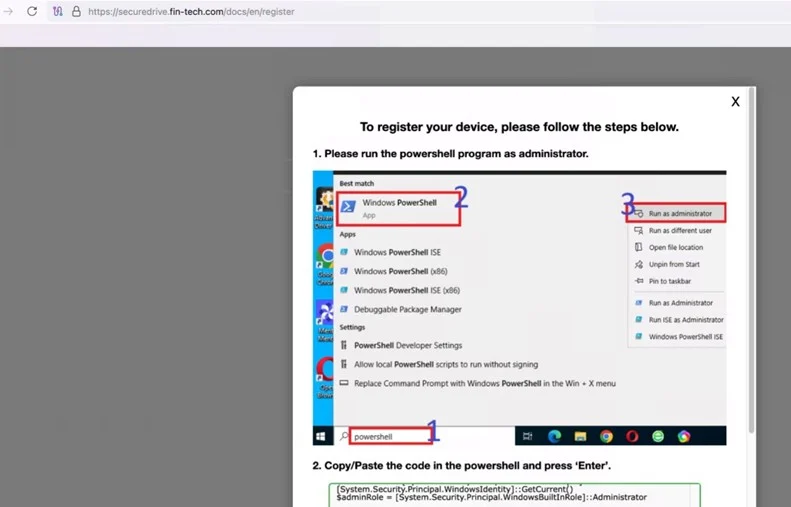
ClickFix page for fake device registration
Source: Microsoft
Proofpoint: Nation-State Groups Use ClickFix for Targeted Espionage
A report by Proofpoint highlights four major groups using ClickFix from late 2024 through early 2025:
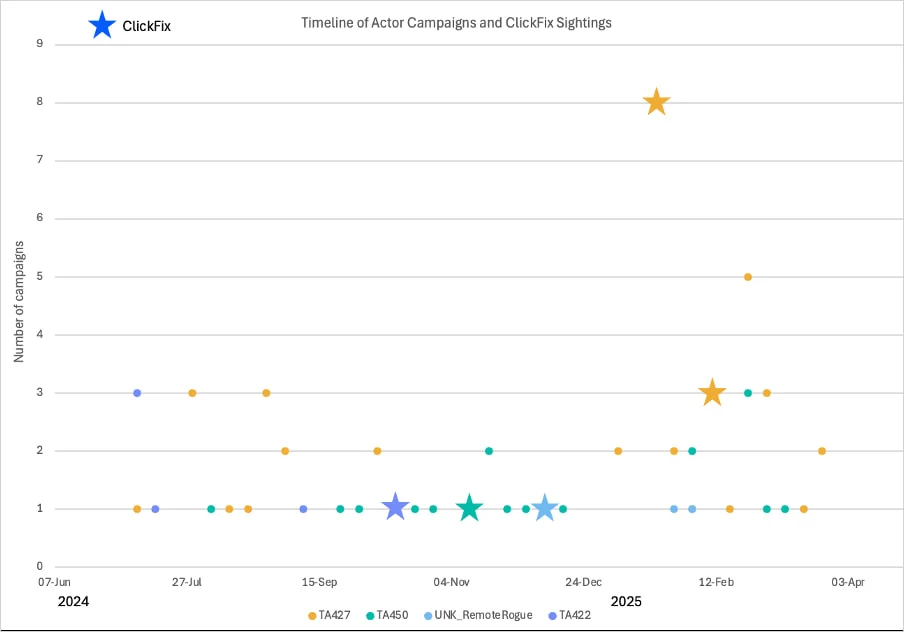
Timeline of ClickFix attacks
Source: Proofpoint
1. Kimsuky (North Korea)
- Targets: Policy think tanks focused on North Korea.
- Timeframe: January–February 2025.
- Tactic: Impersonated Japanese diplomats in Korean, Japanese, or English-language emails.
- Victims received PDF files linking to spoofed secure drives.
- Clicking the link prompted users to run a PowerShell script to “register.”
- This triggered the download of QuasarRAT, with scheduled tasks for persistence.
- A decoy PDF was shown to distract the victim during execution.
2. MuddyWater (Iran)
- Targets: 39 Middle Eastern organizations.
- Timeframe: Mid-November 2024.
- Tactic: Emails disguised as Microsoft security alerts.
- Users were urged to run PowerShell as admin to apply an update.
- This installed a remote monitoring tool called Level, supporting long-term espionage.
3. UNK_RemoteRogue (Russia)
- Targets: Two firms linked to a major arms manufacturer.
- Timeframe: December 2024.
- Tactic: Emails from compromised Zimbra servers mimicked Microsoft Office.
- Links led to a fake Microsoft Word site in Russian, featuring a video tutorial.
- Running the command executed PowerShell and JavaScript, connecting to a C2 server using Empire.
4. APT28 (Russia / GRU)
- Timeframe: October 2024.
- Tactic: Phishing emails mimicked Google Sheets with a fake reCAPTCHA check.
- After verification, a pop-up guided users to run PowerShell.
- The script opened an SSH tunnel and deployed Metasploit, granting remote access.
ClickFix Is Spreading Due to Low Awareness and High Success Rate
The increasing adoption of ClickFix across state-backed actors underscores its effectiveness in bypassing traditional defenses. Attackers rely on victims’ willingness to run unfamiliar commands, often under pressure or misinformation.
Though effective, these attacks succeed largely because users often don’t recognize the risks of executing unknown scripts, especially when presented in a seemingly legitimate context.