The Darcula phishing-as-a-service (PhaaS) platform is about to release its third major version. A key feature for this version is auto creating custom phishing kits targeting any brand. This lowers the barrier to entry for novice cybercriminals.
Darcula Suite: New Features and Capabilities
The upcoming release, called “Darcula Suite,” is currently in beta. It removes previous restrictions on targeting. Instead of a limited selection of kits, users can create their own.
This new version also simplifies the process. It requires fewer technical skills and includes a user-friendly admin dashboard. It also offers IP and bot filtering, campaign performance tracking, and automated credit card theft tools.
Netcraft researchers tested the beta and confirmed these features. They also noted increased interest from cybercriminals, even before the official release.
“Because the container images used to run the admin panel are publicly available at registry[.]magic-cat[.]world, Netcraft was able to get a rough estimate of the number of individuals already exploring this test suite,” their report states.
“The pull count of the API image has increased by more than 100% and the web image by more than 50% from February 5 to February 10.”
Darcula 3.0 test version
Source: Netcraft
DIY Phishing Kit Generator
The main feature of Darcula Suite is its DIY phishing kit generator. Users provide a brand’s URL. The platform then automatically generates all the necessary templates for the attack.
It uses Puppeteer to clone the legitimate site, copying HTML, CSS, images, and JavaScript to maintain the original design of the site.
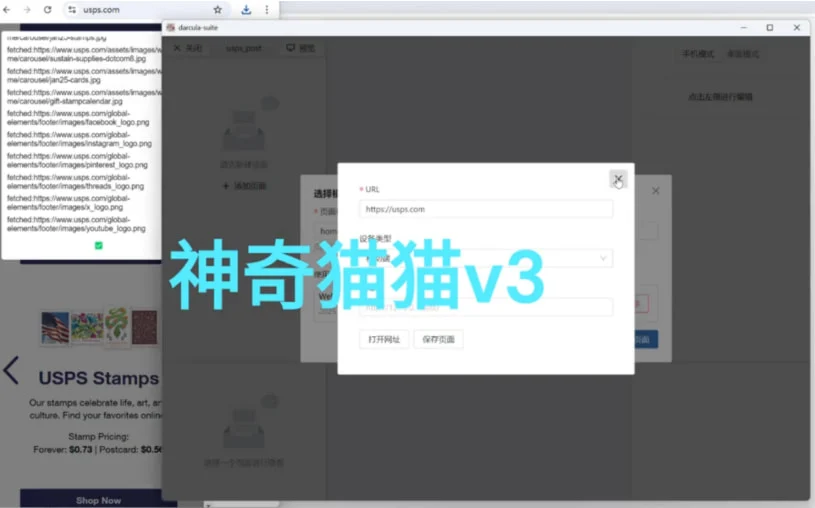
Darcula cloning a legitimate site
Source: Netcraft
Attackers can modify elements like login fields, payment forms, and two-factor authentication prompts. They can replace them with phishing pages, use custom error messages, or modify JavaScript to steal data.
Pre-made templates are also available, including fake password reset pages, credit card payment forms, and 2FA code entry prompts.
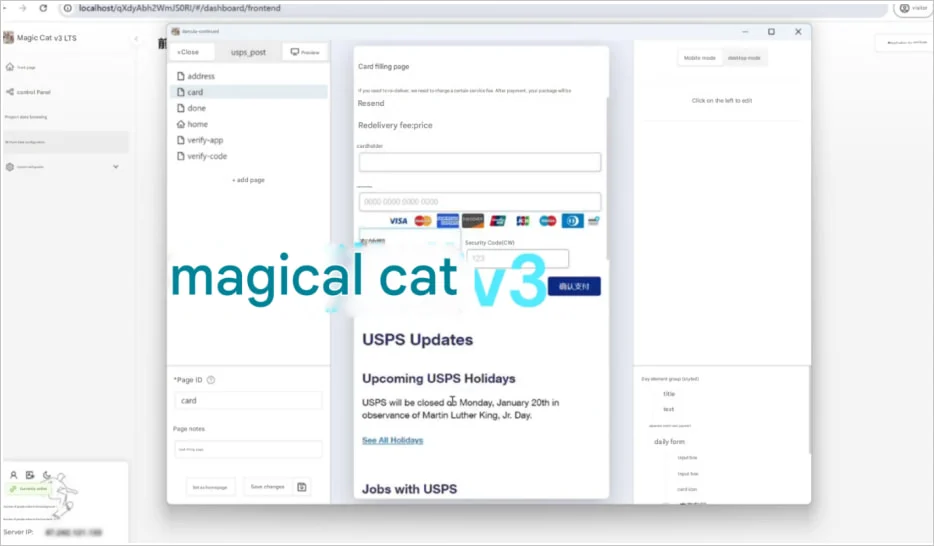
Injected payment form for credit card phishing
Source: Netcraft
The finished phishing site is packaged into a “.cat-page” bundle and uploaded to the Darcula admin panel for deployment, management, data theft, and monitoring.
Additional Features in Darcula 3.0
Beyond the DIY generator, Darcula 3.0 includes:
Anti-detection features: randomized deployment paths, IP filtering, crawler blocking, and device-type restrictions.
Improved admin panel: simplified phishing campaign management, a performance dashboard, real-time stolen credential logs, and Telegram notifications.
Credit card conversion tool: converts stolen credit card data into virtual card images for use in digital payment apps.
Netcraft reports that Telegram groups linked to Darcula are already selling burner phones pre-loaded with stolen cards.
Increased Phishing Threat
Darcula 3.0’s ease of use will likely lead to a significant increase in phishing attacks. Netcraft notes that in the last 10 months, they detected and blocked almost 100,000 Darcula 2.0 domains, 20,000 phishing sites, and 31,000 associated IP addresses.
The new features make detecting and stopping these attacks even more challenging. The rise of PhaaS services like Darcula highlights the growing sophistication and accessibility of cybercrime tool