Over the weekend, Monobank, a prominent Ukraine’s largest mobile-only bank, experienced a distributed denial-of-service (DDoS) attack. This Monobank DDoS Attack is part of a series of attacks targeting Ukrainian financial institutions.
The Monobank DDoS Attack is the Largest DDoS Attack on the Bank
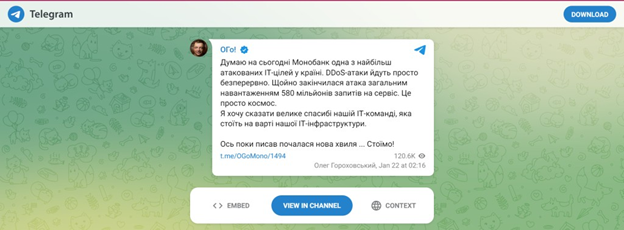
Monobank’s CEO, Oleh Horokhovskyi, reported that this was the largest attack the bank has faced, with a staggering 580 million service requests over a span of three days.
DDoS attacks involve hackers flooding an online service with excessive and meaningless internet traffic, aiming to disrupt its normal functioning.
The DDoS attacks on Monobank spanned from Friday to Sunday. As Monobank solely operates through a mobile app, it has not provided any information regarding the impact on its operations.
Users of Monobank stated that they did not experience any problems with the bank’s app or virtual banking cards.
CEO Oleh Horokhovskyi described Monobank as one of the most frequently targeted IT entities in Ukraine, emphasizing the continuous nature of DDoS attacks against the bank.
“I think today Monobank is one of the most attacked IT targets in the country.”
Horokhovskyi expressed concern about the attacks, on Telegram,
Who is Behind Ukraine’s Monobank DDoS Attack?
Monobank has not provided any information regarding the identity of the potential hacker group behind the recent attack. CEO Oleh Horokhovskyi has chosen not to comment further on the matter.
It is worth noting that larger organizations have experienced more severe DDoS incidents, such as the attacks against major U.S. tech companies in August.
The Recent Monobank DDoS Attack is a Continuation of DDoS Attacks that Started in December
Monobank had previously encountered an attack earlier in December, which coincided with the shutdown of Ukraine’s largest telecom operator, Kyivstar, by Russian state hackers.
This resulted in millions of subscribers being without cellular network and internet coverage for several days. During that incident, Monobank swiftly resolved the issue.
Given Monobank’s frequent use by Ukrainians to raise donations for the military, it is plausible that Russian threat actors would target the bank. It is important to note that Russian-linked hackers are also actively targeting other financial institutions in Ukraine.
Ukraine’s Computer Emergency Response Team, CERT-UA Has Already Issued a Warning on UAC-0006 Hackers
In December, Ukraine’s computer emergency response team, CERT-UA, issued a warning about cyberattacks by a hacker group identified as UAC-0006, which primarily focuses on the Ukrainian financial industry.
The hacker group UAC-0006 has been operating since 2013 and has gained notoriety for its use of malware to illicitly obtain funds from Ukrainian businesses. It remains uncertain whether this group is sponsored by a state or motivated by financial gain.
The Monobank Bug Bounty Program Identifies Two New High Severity Flaws
Monobank has not reported any recent cyberattacks apart from the DDoS incidents. In December, the bank took proactive measures by implementing its first bug bounty program. This program incentivizes security researchers, also known as ethical hackers, to identify and report vulnerabilities in exchange for rewards.
To ensure the security of its bug bounty program, participants in Monobank’s initiative were required to verify their identities using Ukraine’s e-government app. This measure aimed to effectively identify and exclude potential Russian hackers, according to Monobank’s Chief Information Officer.
During the bug bounty program, participants successfully identified two high-severity flaws and several less serious bugs within Monobank’s systems. However, no critical security vulnerabilities were discovered, indicating the bank’s robust security measures.









