The financially motivated threat group known as Scattered Spider is intensifying its focus on VMware ESXi environments, launching a series of sophisticated cyberattacks against large U.S. enterprises in sectors such as retail, airlines, insurance, and transportation.
According to new research by Google’s Threat Intelligence Group (GTIG), the group is running a coordinated hacking spree that bypasses traditional defenses not through exploiting software flaws, but by using social engineering to gain privileged access to core systems.
Attackers Rely on Social Engineering, Not Software Exploits
GTIG reports that Scattered Spider continues to rely heavily on social engineering tactics, impersonating company employees to manipulate help desk teams. These deceptive calls are the first step in a multi-phase attack chain that ultimately results in full control over VMware ESXi hypervisors—the foundation of many organizations’ virtual infrastructure.
Once the attacker convinces IT support to reset a password for a legitimate employee, the group gains an initial foothold in the network. From there, they scan internal documentation and network assets, hunting for administrative credentials and configurations related to VMware vSphere environments.
“Armed with the name of a specific, high-value administrator, they make additional calls to the help desk. This time, they impersonate the privileged user and request a password reset, allowing them to seize control of a privileged account,” said the Google Threat Intelligence Group.
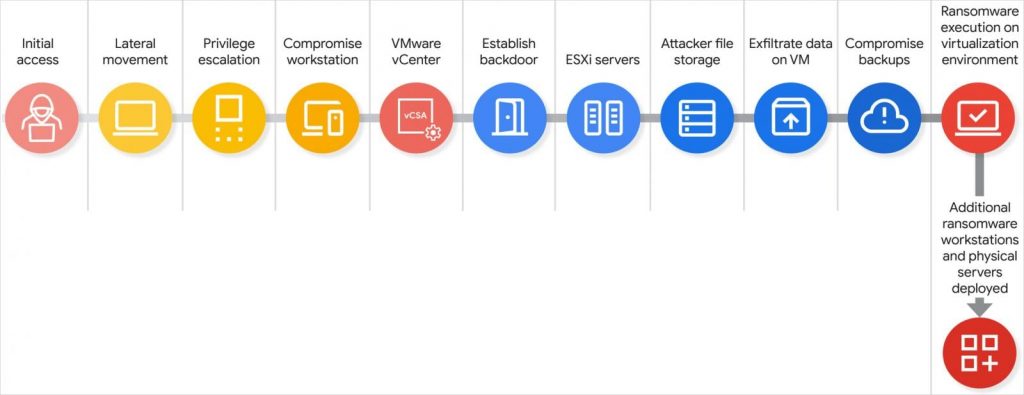
Scattered Spider attack chain
Source: Google
How Scattered Spider Gains Control Over VMware Environments
After obtaining high-level credentials, the attackers shift their attention to the VMware vCenter Server Appliance (vCSA)—the central hub for managing VMware virtual infrastructure. With access to vCSA, Scattered Spider:
- Enables SSH on ESXi hosts
- Resets root passwords
- Executes a “disk-swap” attack to extract critical domain data
In the disk-swap phase, attackers power off a domain controller VM, detach its virtual disk, and attach it to a separate VM under their control. This allows them to copy sensitive files like NTDS.dit, which stores Active Directory credentials, before reverting the configuration to avoid detection.
This level of access also allows attackers to manipulate backup systems. GTIG notes that backup jobs, snapshots, and repositories are being deleted—effectively cutting off recovery options before ransomware is deployed.
Ransomware Deployment Closes the Loop
With SSH access and administrative control over the hypervisor, Scattered Spider uses these systems to deliver and activate ransomware binaries, encrypting virtual machine files across connected datastores.
The entire process—from initial call to ransomware deployment—can be completed within hours, according to Google researchers.
“Even without exploiting any software vulnerabilities, the threat actor manages to obtain an unprecedented level of control over an entire virtualized environment, allowing them to bypass many traditional in-guest security controls,” a Google spokesperson told BleepingComputer.
Scattered Spider’s Methods Becoming a Blueprint for Other Groups
Although this is not the first time VMware ESXi systems have been targeted, GTIG warns that other ransomware groups are beginning to adopt these techniques, posing a growing threat to enterprises reliant on virtualized infrastructure.
One key issue is that many enterprises lack deep familiarity with VMware architecture, leaving these systems poorly defended.
Scattered Spider, also tracked as UNC3944, 0ktapus, or Octo Tempest, is known for its highly refined social engineering capabilities, including impersonating employees with correct terminology and local accents.
Google Shares Mitigation Framework for Enterprises
To help organizations defend against these threats, Google published a technical breakdown of a typical Scattered Spider attack chain, along with actionable guidance. Their recommendations include:
1. Harden VMware vSphere and ESXi
- Use
execInstalledOnlyto restrict command execution - Enable VM encryption
- Disable SSH on ESXi hosts
- Avoid direct AD joins on ESXi
- Delete orphaned virtual machines
- Enforce strict access policies and multi-factor authentication (MFA)
2. Secure Authentication and Critical Assets
- Deploy phishing-resistant MFA across VPNs, Active Directory, and vCenter
- Isolate Tier 0 assets (domain controllers, backups, PAM solutions)
- Consider separate identity providers (IdPs) to reduce dependency on Active Directory
3. Improve Monitoring and Recovery
- Centralize logs in a SIEM solution
- Alert on unusual behaviors like admin group changes and vCenter logins
- Use immutable, air-gapped backups and routinely test recovery from hypervisor-layer attacks
A New Cyber Threat Era for Virtualized Infrastructure
Scattered Spider’s ability to control entire virtual environments through non-technical, social means represents a growing risk for enterprises using VMware platforms. With ransomware deployment as the final stage, organizations face severe business disruption if these threats go undetected.
GTIG urges enterprises to reassess how they secure their VMware ESXi and vSphere environments, especially as attackers continue to innovate in ways that bypass traditional endpoint security tools.