A newly discovered Android malware named SuperCard X is being distributed as part of a malware-as-a-service (MaaS) offering that allows attackers to steal payment card data and perform NFC relay attacks. The malware targets Android devices and enables point-of-sale and ATM transactions using emulated payment cards.
SuperCard X Malware Distributed via Telegram Channels, Linked to Chinese-Speaking Threat Actors
The SuperCard X platform has been linked to Chinese-speaking threat actors and shows similarities to the NFCGate open-source project and its malicious variant, NGate. These tools have previously supported NFC-based fraud, primarily in Europe.
The malware is actively promoted through Telegram channels, which also offer customer support to affiliates using the tool. According to security firm Cleafy, active attacks using SuperCard X have been identified in Italy, involving multiple customized malware variants, suggesting region-specific deployments.
Overview of the SuperCard X attacks
Source: Cleafy
How SuperCard X Carries Out NFC-Based Theft Through Social Engineering and Malware
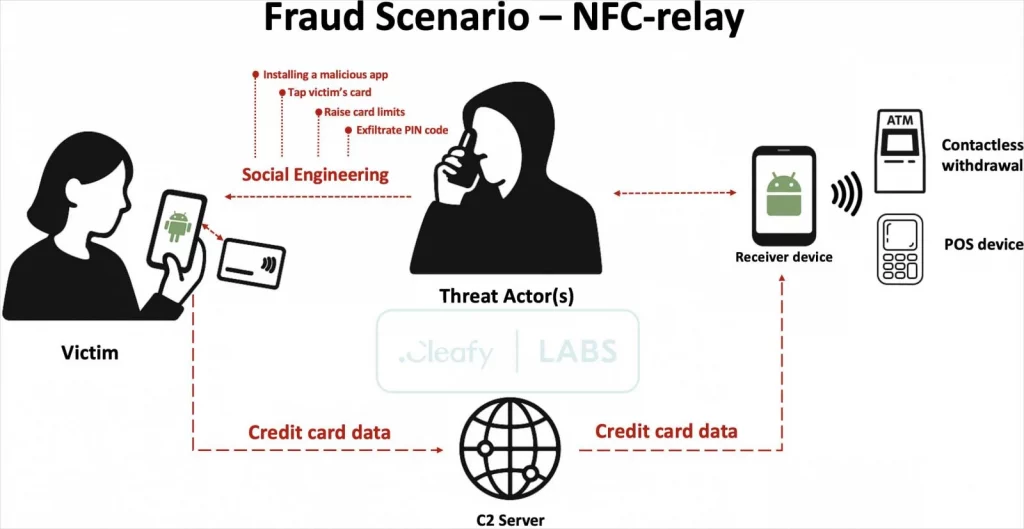
The attack begins with a fake SMS or WhatsApp message, typically impersonating a bank. The message claims there is an issue with a suspicious transaction and prompts the victim to call a provided number.
- The call is handled by a scammer pretending to be from bank support.
- The victim is tricked into providing their card number and PIN.
- They are asked to remove card spending limits using their banking app.
- Finally, they are told to install a malicious app called ‘Reader’, presented as a security or verification tool.
Once installed, the Reader app requests minimal permissions, mainly access to the NFC module, avoiding detection by security software. Victims are then instructed to tap their payment card to their phone. The malware reads the card chip data and forwards it to the attackers.
Card Emulation and Transaction Execution Using Tapper App
The attackers receive the stolen card data on their own Android device, which runs a second app named Tapper. This app emulates the card and enables contactless payments or ATM withdrawals.
- Emulated cards are ATR-based (Answer to Reset), mimicking legitimate smartcard behavior.
- Transactions are limited in value but hard to detect, as they appear normal to banks.
- These small charges are usually approved instantly and are difficult to reverse.
SuperCard X Uses Stealth Techniques and Secure Communications to Avoid Detection
Cleafy reports that SuperCard X is not currently detected by any antivirus engines on VirusTotal. The malware avoids using risky permissions or behaviors such as screen overlaying, allowing it to bypass heuristic scans.
Additional technical features include:
- mTLS (mutual TLS) to secure communication with command-and-control servers.
- Certificate-based authentication that resists interception and analysis.
These measures demonstrate a high level of sophistication and an understanding of smartcard protocols and mobile security evasion tactics.
Google Responds: No Presence of SuperCard X on Google Play
“Based on our current detection, no apps containing this malware are found on Google Play. Android users are automatically protected by Google Play Protect, which is on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps known to exhibit malicious behavior, even when those apps come from sources outside of Play,”
— Google spokesperson
Google confirmed that it has not found any apps containing this malware on Google Play.









