The Internet Archive, a non-profit digital library, has been hit by a second security breach. This time, the attackers exploited stolen GitLab authentication tokens to gain access to the organization’s Zendesk support system, potentially compromising over 800,000 support tickets dating back to 2018. This follows a previous breach that exposed the data of 33 million users.
Zendesk Breached: A Cascade of Compromised Credentials
The breach was discovered after numerous individuals reported receiving unexpected replies to old Internet Archive removal requests.
These replies served as a chilling confirmation of the breach, with the threat actor boasting:
“It’s dispiriting to see that even after being made aware of the breach weeks ago, IA has still not done the due diligence of rotating many of the API keys that were exposed in their gitlab secrets,”
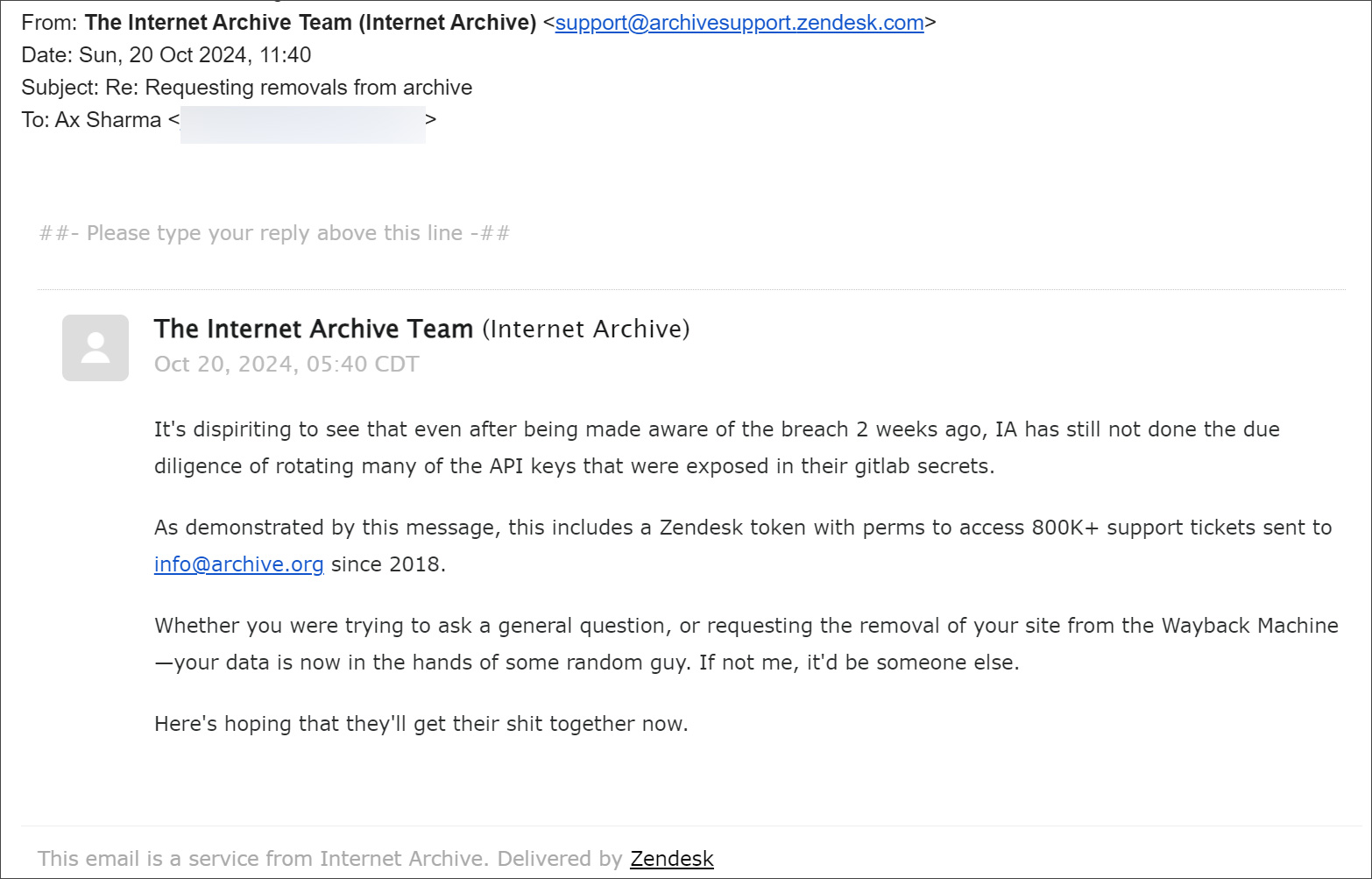
Internet Archive Zendesk emails sent by the threat actor
Source: BleepingComputer
The attacker further revealed access to a Zendesk token granting access to a massive trove of support tickets. The authenticity of these emails was confirmed by the fact that they passed DKIM, DMARC, and SPF authentication checks, originating from a legitimate Zendesk server (192.161.151.10).
Adding to the severity of the situation, we learned that some users had to upload personal identification documents when requesting the removal of pages from the Wayback Machine. The threat actor may now possess access to these sensitive attachments, depending on their Zendesk API access and whether they downloaded the support tickets.
The Root Cause: Exposed GitLab Tokens and a Two-Year Lapse in Security
This latest Internet Archive breach is directly linked to a previously reported vulnerability. On October 9th, BleepingComputer revealed that the Internet Archive had suffered two simultaneous attacks: a data breach affecting 33 million users and a DDoS attack launched by a group claiming to be pro-Palestinian (SN_BlackMeta). While separate actors perpetrated these attacks, the data breach’s root cause was the exposure of a GitLab configuration file on the server services-hls.dev.archive.org.
This configuration file contained an authentication token that remained exposed for nearly two years (since at least December 2022), despite being rotated multiple times. This token allowed the threat actor to download the Internet Archive’s source code, which, in turn, contained additional credentials and authentication tokens, including access to the organization’s database management system. T
his access granted the attacker the ability to download the user database, more source code, and even modify the site itself. The attacker claimed to have stolen 7TB of data, although no samples were provided as proof. The stolen data included the API access tokens for the Zendesk support system, leading to the current crisis.
BleepingComputer repeatedly attempted to warn the Internet Archive about the exposed GitLab token and the potential consequences, but received no response.
Internet Archive Breach Motivated by Cyber Street Cred, Not Monetary Gain
Contrary to initial speculation, the breach wasn’t motivated by political agendas, government involvement, or financial gain. The attacker’s primary motivation appears to be enhancing their reputation within the underground data breach community.
The attacker explained their actions to BleepingComputer through an intermediary, stating that the breach was performed while in a group chat with others, with multiple individuals receiving portions of the stolen data. This stolen data is now likely circulating within the community and is expected to be leaked publicly on hacking forums like Breached in the future. The Internet Archive, as a high-profile target, provided significant “cyber street cred” for the attacker.
The Internet Archive’s repeated breaches highlight the critical importance of proactive security measures and prompt response to security warnings. The failure to rotate authentication tokens and address known vulnerabilities led to a cascade of compromised data, affecting millions of users and potentially exposing sensitive personal information. This incident serves as a stark reminder for all organizations to prioritize security best practices and promptly address security vulnerabilities to prevent similar breaches.









