Hackers are increasingly using sophisticated techniques to spoof Microsoft ADFS login pages, stealing credentials and bypassing multi-factor authentication (MFA).
This campaign, discovered by Abnormal Security, targets education, healthcare, and government organizations—at least 150 in total.
The goal? Access corporate email for further attacks, including Business Email Compromise (BEC). This constitutes a serious case of Spoofing Microsoft ADFS.
The attack begins with spoofed emails, mimicking legitimate IT communications. These emails urge recipients to update security settings or accept new policies via a link.

Sample of a phishing email used in the attacks
Source: Abnormal Security
Clicking this link takes victims to a meticulously crafted phishing site, a near-perfect replica of their organization’s Microsoft ADFS login pages. This is a prime example of how Hackers spoof Microsoft ADFS login pages easily.
The fake login page demands usernames, passwords, and MFA codes, or tricks users into approving push notifications.
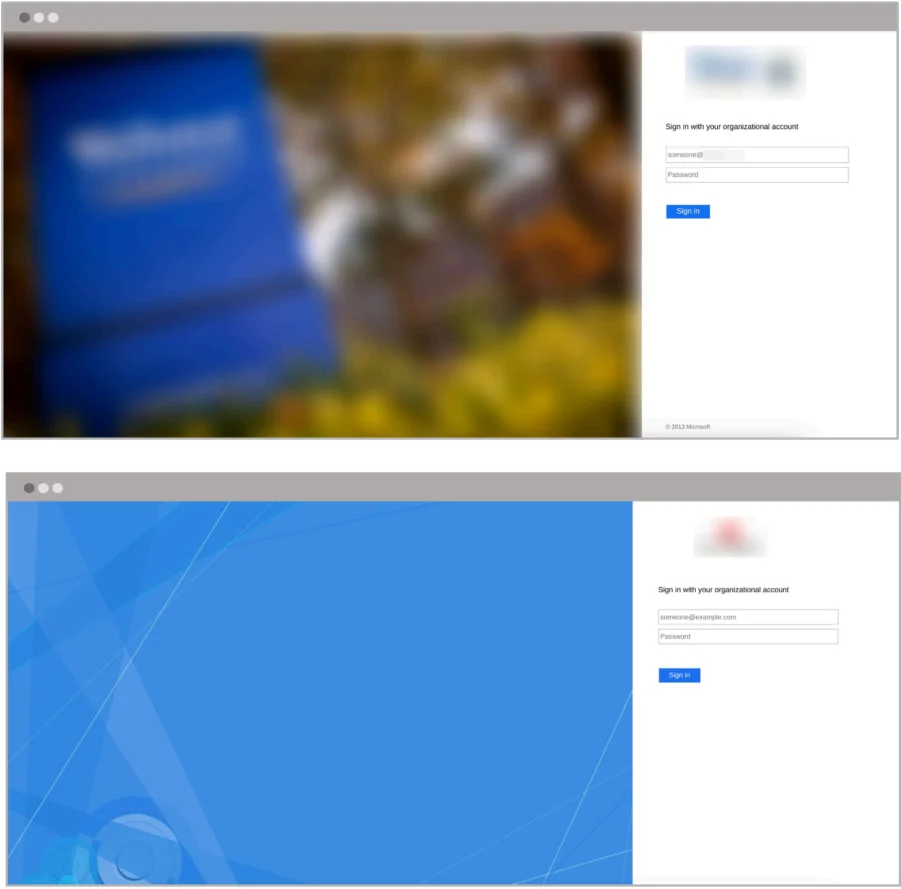
Spoofed ADFS portals
Source: Abnormal Security
“The phishing templates also include forms designed to capture the specific second factor required to authenticate the targets account, based on the organizations configured MFA settings.” Abnormal Security’s report details the attackers’ adaptability.
They observed templates targeting Microsoft Authenticator, Duo Security, and SMS verification. This shows the effectiveness of Hackers spoofing the Microsoft ADFS.
After obtaining credentials, victims are redirected to the legitimate login page to mask the attack. Meanwhile, the hackers exploit the stolen information, accessing accounts, creating email filters, and launching further phishing attacks.
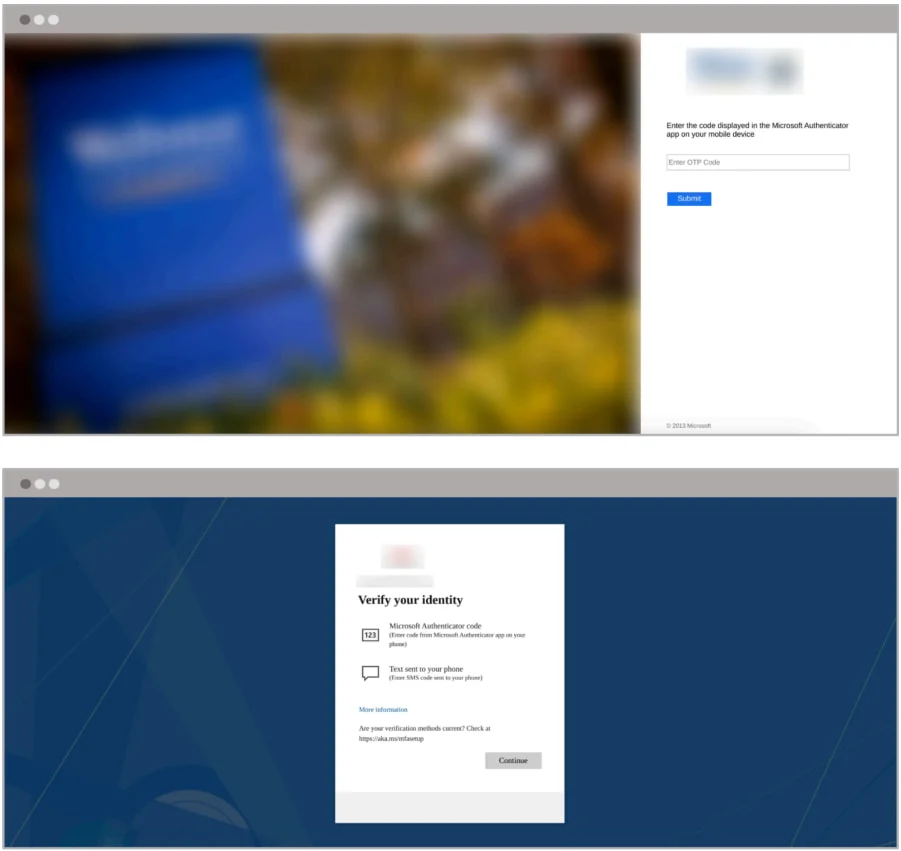
A few MFA bypass screens
Source: Abnormal Security
The attackers even used Private Internet Access VPN to mask their location, demonstrating a high level of sophistication in their ADFS spoofing techniques.
While not directly breaching ADFS, the social engineering aspect makes this tactic highly effective. The familiar login workflow fosters trust, making victims more susceptible.
Abnormal Security recommends migrating to solutions like Microsoft Entra, implementing enhanced email filters, and employing anomalous activity detection to counter such phishing attacks.
The impact of spoofed ADFS portals is significant. “Abnormal observed templates targeting multiple commonly used MFA mechanisms, including Microsoft Authenticator, Duo Security, and SMS verification.” This shows how attackers’ can adapt to various MFA systems.
The success of this campaign highlights the need for robust security measures to protect against Spoofed emails and sophisticated email spoofing techniques. Organizations must remain vigilant against these advanced phishing attack methods targeting Microsoft ADFS login pages.









