Recent reports have surfaced the internet that on Christmas Eve, the source code for GTA 5 source code leaked on GTA leak channel on the dark web. This incident follows a previous hack by the Rockstar games hacker Lapsus$, who stole corporate data from Rockstar games over a year ago.
The GTA 5 Source Code Leak also contains a file for Bully 2, which has been expected to launch as the sequel to Rockstar 2006’s Bully. GTA 5 leaked source code was shared on various platforms, including Discord, a dark web website, and a Telegram channel that the Lapsus$ hackers previously used to distribute stolen Rockstar data.
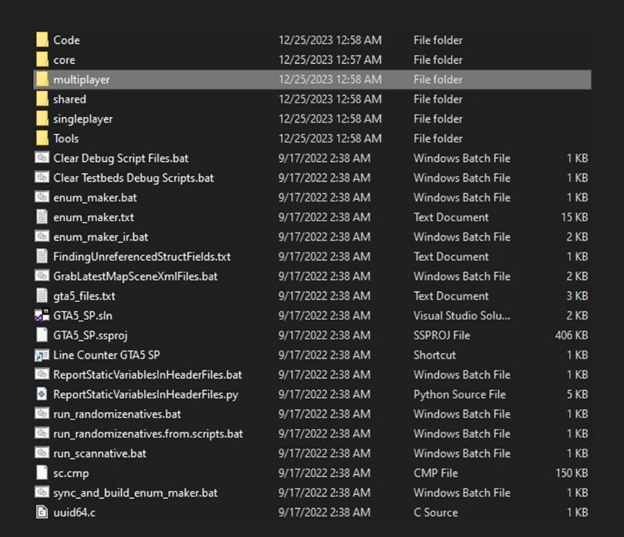
The owner of a Grand Theft Auto leak channel on Telegram, known as ‘Phil,’ posted the links to the stolen source code, along with a screenshot of one of the folders.
Arion Kurtaj – GTA 6 Hacker Life in Prison
It is worth noting that Arion Kurtaj, the Rockstar games hacker, also known as ‘teapotuberhacker,’ was instrumental in GTA 5 Source Code Leak and was recently sentenced to an indefinite hospital prison by a UK judge for his involvement in hacking Rockstar and Uber.
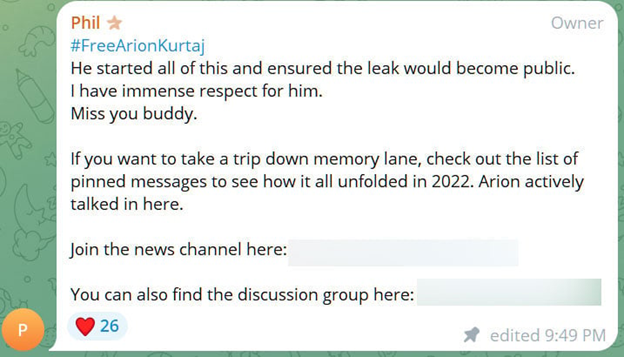
As the Rockstar hacker faces life in prison, the channel owner paid tribute to Arion Kurtaj in their post.
#FreeArionKurtaj
He started all of this and ensured the leak would become public.
I have immense respect for him.
Miss you buddy.
If you want to take a trip down memory lane, check out the list of pinned messages to see how it all unfolded in 2022. Arion actively talked in here.
GTA 5 Source Code Leak – What Happened?
In 2022, Rockstar Games fell victim to hacking orchestrated by members of the well-known Lapsus$ hacking group in the GTA 6 leaks incident.
During the breach, the hackers managed to infiltrate the company’s internal Slack server and Confluence wiki.
During the attack, the Lapsus$ threat actors claimed to have successfully stolen the source code and assets for both GTA 5 and the yet-to-be-released GTA 6.
They even went as far as leaking certain content on forums and Telegram, including samples of the GTA 5 source code as evidence of their theft.
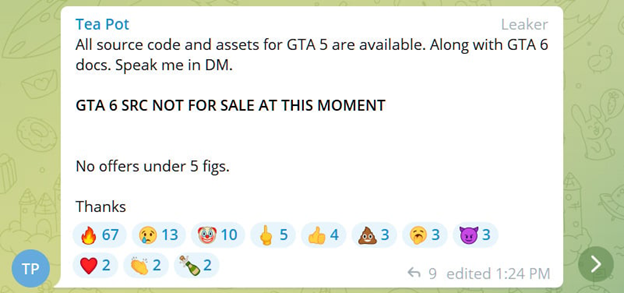
According to reports from the security research group vx-underground, they engaged in a conversation with the leaker on Discord.
“They claim to have received the source code August, 2023,” reads the vx-underground post.
“Their motivation was to combat scamming in the GTA V modding scene, many people were allegedly scammed by people claiming to have the GTA V source code.”
It is important to note that while the leaked source code appears to be genuine GTA 5 source code, its authenticity has not been independently verified.
The Lapsus$ Hackers
The Lapsus$ hacking group gained notoriety for their expertise in social engineering and SIM swapping techniques, which they utilized to breach corporate networks. Their cyberattacks targeted prominent companies such as Uber, Microsoft, Rockstar Games, Okta, Nvidia, Mercado Libre, T-Mobile, Ubisoft, Vodafone, and Samsung.
During these attacks, the threat actors would often attempt to extort the targeted organizations, threatening to leak stolen data, which typically included valuable source code and customer information.
The success of these attacks prompted the Department of Homeland Security (DHS) Cyber Safety Review Board to thoroughly analyze the tactics employed by Lapsus$ and provide recommendations to prevent similar attacks in the future.
Although the Lapsus$ group’s activities have diminished following the arrest of some of its members with Arion Kurtaj being the most recent, it is believed that they have now become part of the loosely connected hacking collective known as Scattered Spider.
This new group shares similar tactics to Lapsus$, employing strategies such as social engineering, phishing, MFA fatigue, and SIM swapping attacks to gain initial access to the networks of large organizations.









