Scammers are now targeting U.S. companies using fake BianLian ransom notes sent through postal mail. This alarming development was first reported by Guidepoint Security, with BleepingComputer later receiving a copy of the note from a CEO who encountered the scam.
Overview of the Scam
The BianLian ransom notes claim to originate from the “BIANLIAN Group.” The envelopes bear a return address located in an office building in Boston, Massachusetts:
BIANLIAN GROUP
24 FEDERAL ST, SUITE 100
BOSTON, MA 02110
These letters are mailed directly to the CEOs of various companies at their corporate addresses. Notably, the envelope from one CEO shows it was mailed on February 25, 2025, the same date reported by Arctic Wolf, who also highlighted this scam.

Envelope for fake BianLian ransom note
Source: BleepingComputer
Details of the Ransom Notes
The ransom notes are tailored to the specific industry of the targeted company. For instance:
- Healthcare companies are warned about stolen patient and employee information.
- Product-based businesses are accused of having customer orders and employee data exposed.
One excerpt from the fake note reads,
“I regret to inform you that we have gained access to [REDACTED] systems and over the past several weeks have exported thousands of data files, including customer order and contact information, employee information with IDs, SSNs, payroll reports, and other sensitive HR documents.”

Fake BianLian ransom note sent via snail mail
Source: GuidePoint Security
Unlike typical ransom demands, these letters assert that BianLian is no longer negotiating with victims. Instead, they demand a Bitcoin payment within 10 days to prevent alleged data leaks. The ransom amounts range from 250,000 to 250,000 to 250,000 to 500,000, with each note including:
- A newly generated Bitcoin address for payment.
- A QR code linked to the Bitcoin address.
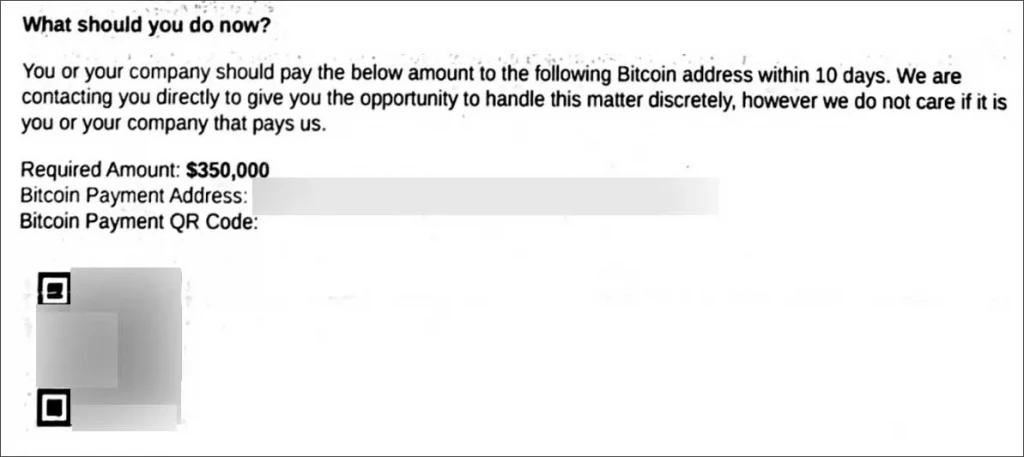
Payment information in fake BianLian ransom note
Source: BleepingComputer
Attempts at Legitimacy
To make their claims appear credible, the scammers have included real Tor data leak sites associated with the BianLian operation. Additionally, Arctic Wolf noted that some letters contained actual compromised passwords to enhance their legitimacy.
Grayson North from GuidePoint Security stated,
“While GRIT cannot confirm the identity of the letter’s authors at this time, we assess with a high level of confidence that the extortion demands contained within are illegitimate and do not originate from the BianLian ransomware group.”
Despite the apparent seriousness of these notes, no actual breaches have been confirmed. Experts advise IT and security administrators to inform executives about these scams to prevent unnecessary panic and resource allocation.
The postal mail scam involving BianLian ransom notes serves as a reminder of the evolving tactics used by cybercriminals. Companies must remain vigilant against such threats.
Helpful Reads:









