Cybersecurity researchers have discovered a new ransomware-as-a-service (RaaS) operation called Eldorado that first emerged in March 2024.
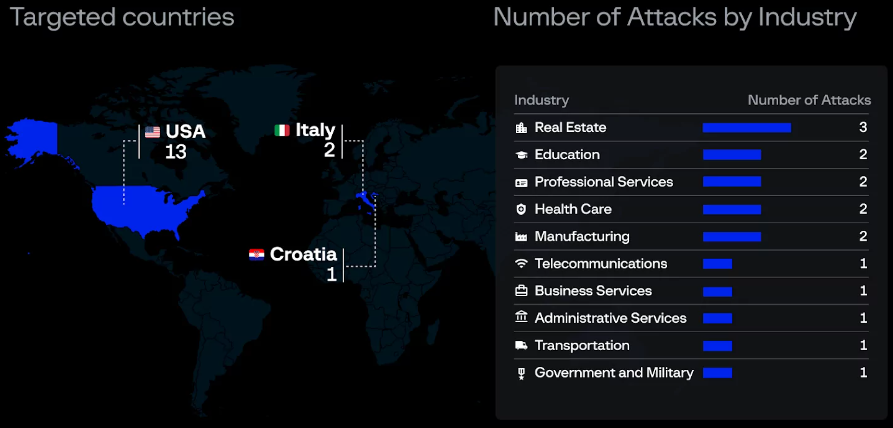
The Eldorado ransomware gang has already infected 16 victims across various sectors like real estate, education, healthcare and manufacturing. Most of the victims were located in the United States.
Group-IB, a cybersecurity firm, has been closely monitoring the activities of the Eldorado ransomware operators. They noticed the operators promoting their malicious service on known RaaS forums and looking to recruit skilled affiliates. The gang also runs a leakage site to list victims, however it was unavailable at the time of research.
Eldorado Ransomware Targets Windows and Linux Systems
Eldorado ransomware is developed using the Go programming language and comes with variants that can encrypt files on both Windows and Linux platforms. Group-IB researchers obtained the encryptor from the developers which included a user manual detailing 32-bit and 64-bit versions for VMware ESXi hypervisors and Windows.
According to the researchers, “Eldorado is a unique development and does not rely on previously published builder sources”. The ransomware employs the ChaCha20 algorithm to encrypt files using a unique 32-byte key and 12-byte nonce generated for each locked file. These keys and nonces are further encrypted using RSA with OAEP.
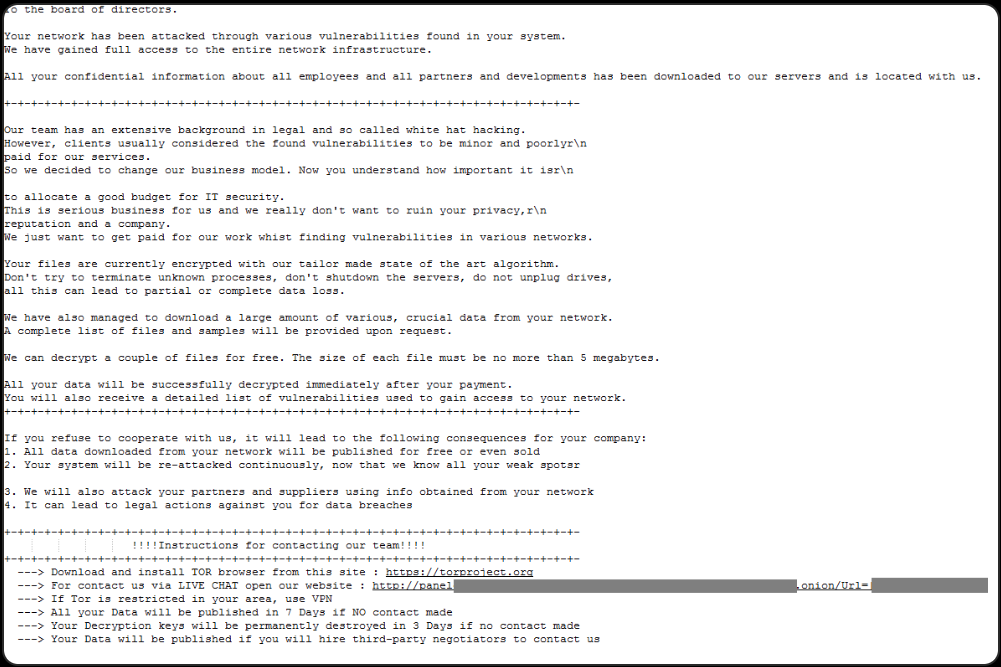
After encryption, files are appended with the “.00000001” extension and ransom notes named “HOW_RETURN_YOUR_DATA.TXT” are deposited in the Documents and Desktop folders. On Windows, Eldorado also encrypts network shares using SMB and deletes shadow volume copies to prevent recovery. It skips encrypting certain filetypes like DLLs, LNKs and EXEs to avoid rendering the system unusable. The ransomware is designed to self-delete by default.
As per Group-IB’s findings from infiltrating the operation, affiliates working with Eldorado are able to customize certain attack parameters. On Windows, affiliates can specify which directories to encrypt, skip local files, target network shares on specific subnets and prevent self-deletion. On Linux, customization is limited to setting encryption directories.
Recommendations to enhance defenses against Eldorado ransomware
In light of the capabilities demonstrated by the Eldorado ransomware gang, Group-IB recommends taking various security measures to strengthen defenses against such attacks:
- Implement multi-factor authentication and access control solutions
- Use endpoint detection and response tools to quickly identify threats
- Maintain regular data backups to minimize damage from encryption
- Leverage AI-based analytics and malware detonation for threat detection
- Prioritize and apply security patches to fix system vulnerabilities
- Educate employees on cybersecurity awareness and threat reporting
- Conduct audits and maintain best practices for digital hygiene
- Do not pay ransom demands which may enable further attacks
While Eldorado ransomware is a new ransomware-as-a-service that is not a rebrand of an existing operation, Group-IB warns it has rapidly caused significant harm to victims through data-encryption within a short span. Organizations must enhance their security posture to protect against such evolving cyber threats.