DragonForce Introduces Affiliate Ransomware Service
The DragonForce ransomware group is reshaping the ransomware landscape by adopting a white-label model for its operations. The group is now offering other ransomware-as-a-service (RaaS) actors the chance to run their own operations under DragonForce’s proven infrastructure, without the need for maintaining costly systems or developing malware.
DragonForce is positioning itself as a “ransomware cartel,” aiming to manage a variety of brands within the cybercrime ecosystem. This new approach allows affiliates to use DragonForce’s resources—such as encryption tools, data storage, and decryption key management—while branding their operations as their own.
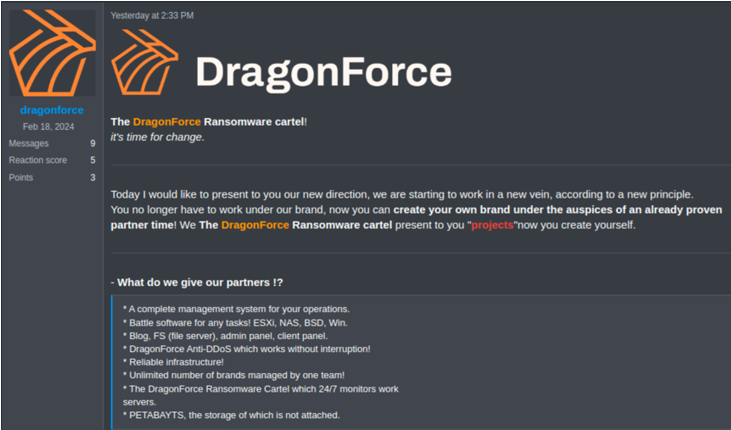
DragonForce announcing SaaS-like RaaS model
source: Secureworks
Key Features of the New Model
DragonForce’s model enables affiliates to:
- Use DragonForce’s malware and infrastructure
- Operate under their own branding
- Avoid the complexities of running data leak sites or negotiating with victims
In exchange, DragonForce takes a 20% cut from the ransoms affiliates collect. This offers a streamlined path for cybercriminals to profit without investing in the heavy lifting of creating and maintaining ransomware operations.
Target Systems and Flexibility
DragonForce’s system is designed to target various platforms, including ESXi, NAS, BSD, and Windows systems. Affiliates can choose to deploy ransomware under the DragonForce brand or their own, creating a flexible environment for cybercriminals to scale their attacks.
The group insists that its operations are governed by a set of internal rules, and affiliates must adhere to these to remain in the cartel. DragonForce maintains strict control over its operations by managing everything on its own servers.
Ethical Guidelines and Healthcare Considerations
Interestingly, DragonForce claims a level of moral consideration in its operations, stating that certain healthcare organizations are off-limits. The group has made it clear that it does not target hospitals treating cancer patients or heart-related conditions, suggesting that it prefers to avoid causing harm to individuals in critical care.
“We don’t attack cancer patients or anything heart-related,” a representative from DragonForce explained. “We’re here for business and money. I didn’t come here to kill people.”
DragonForce New Ransomware Model Appeals to a Broader Range of Affiliates
DragonForce’s new structure is expected to attract a wider range of affiliates, including those with less technical expertise. The flexibility of the model could help DragonForce recruit more actors who can deploy ransomware without the need to build or maintain their own infrastructure.
According to cybersecurity experts from Secureworks, the model’s simplicity could make it more appealing to less experienced threat actors. It also provides an avenue for larger profits due to its expanded affiliate network.
RansomBay Joins the DragonForce Cartel
DragonForce’s appeal has already led to the inclusion of new ransomware groups. RansomBay, a new ransomware gang, has signed on to the DragonForce model, further solidifying the cartel’s expanding reach.