Cybersecurity Cylance firm investigates claims of stolen user data. Data Linked to Snowflake Attacks.
Cybersecurity company Cylance has confirmed that user data allegedly being sold on a hacking forum did originally come from a data breach, though the stolen information is old and was accessed from an unrelated third-party platform.
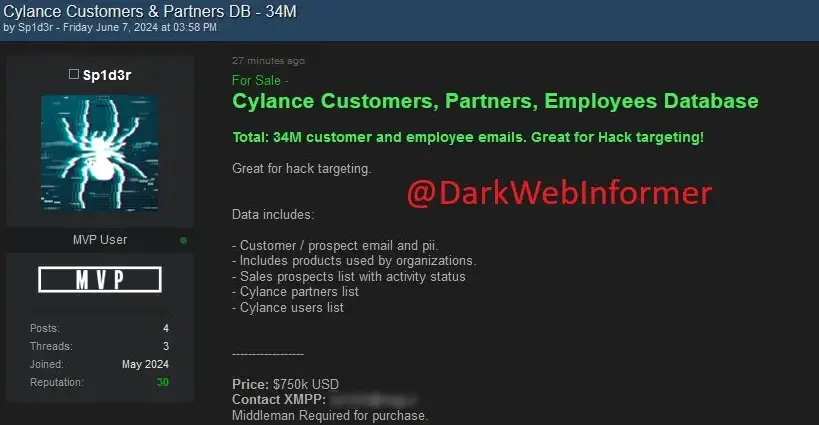
A threat actor known as Sp1d3r claims to be selling over 34 million customer and employee emails and personally identifiable information (PII) belonging to Cylance on a hacker forum for $750,000. However, after investigating the leaked samples, Cylance determined the data to be old marketing information from 2015-2018, prior to their acquisition of the Cylance product portfolio.
In a statement, Cylance acknowledged they are looking into the threats but assured that “no current Cylance customers are impacted, and no sensitive information is involved.” The company confirmed the “data in question was accessed from a third-party platform unrelated to BlackBerry and appears to be from 2015-2018, predating BlackBerry’s acquisition of the Cylance product portfolio.”
Link to Recent Snowflake Account Attacks
While Cylance did not name the third-party involved, the same threat actor (Sp1d3r) is also selling stolen data from automotive parts retailer Advance Auto Parts, obtained after breaching the company’s Snowflake account. As Cylance is also a Snowflake customer, this raises the possibility that their third-party may have been compromised through a similar Snowflake attack.
Recent breaches at Santander, Ticketmaster, and QuoteWizard/Lendingtree have also been connected to unauthorized access of Snowflake accounts. In a joint advisory, CrowdStrike and Mandiant stated these attacks involved criminals using stolen credentials to access Snowflake instances without multi-factor authentication enabled.
Further investigation by Mandiant linked the Snowflake attacks to a financially motivated threat actor known as UNC5537. This group had been stealing customer logins through malware infections dating back to 2020. With hundreds of valid usernames and passwords collected, UNC5537 was able to repeatedly login to impacted Snowflake accounts for data extraction and sale on cybercrime forums.
Protecting Accounts with MFA and Monitor for Compromised Credentials
Mandiant advised in a report that over 165 companies have now been warned about potential exposure from these ongoing attacks. The security firm urged organizations to enable multi-factor authentication on all cloud services, regularly change passwords for compromised accounts, and use network monitoring to only allow access from trusted IP addresses.
While Cylance did not experience a direct breach of their own systems, this incident highlights the ongoing risks of unprotected cloud databases and the importance of protecting accounts with strong authentication as well as quickly responding to any third-party compromises.






