CISA, in collaboration with the FBI, NSA, and international cybersecurity agencies, is urging organizations and DNS providers to implement countermeasures against the “Fast Flux” DNS evasion technique. This technique is being actively exploited by state-sponsored actors and ransomware gangs to mask malicious activity.
Fast Flux is a DNS method used to evade detection and maintain resilient infrastructure for command and control (C2), phishing, and malware delivery. The core of the technique involves rapidly changing DNS records (IP addresses and/or name servers). This rapid alteration makes it extremely difficult for security professionals to trace the source of malicious activity and effectively block it. These rapid switches are often facilitated by botnets—large networks of compromised systems acting as proxies or relays.
The CISA bulletin highlights two main Fast Flux variations: Single Flux and Double Flux. In Single Flux, attackers frequently rotate the IP addresses associated with a domain name in DNS responses. Double Flux adds another layer of complexity by also rapidly changing the DNS name servers themselves, making takedown efforts significantly harder. CISA emphasizes that Fast Flux is employed across the board, from low-level cybercriminals to sophisticated nation-state actors. Examples include Gamaredon, Hive ransomware, Nefilim ransomware, and bulletproof hosting providers.
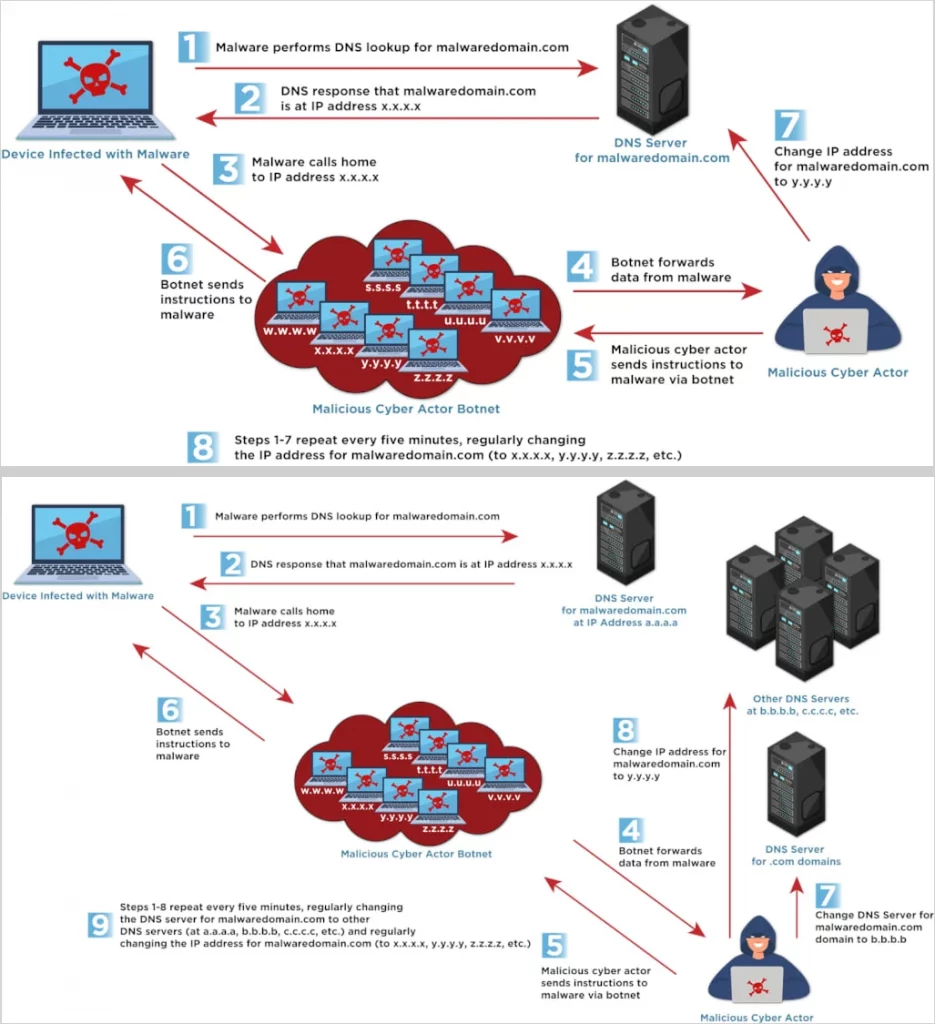
Single Flux (top) and Double Flux (bottom)
Source: CISA
CISA’s Recommendations for Detection and Mitigation
CISA provides several recommendations to detect and mitigate Fast Flux activity. For detection, they suggest:
- Analyzing DNS logs for frequent IP address rotations, low TTL values, high IP entropy, and geographically inconsistent resolutions.
- Integrating external threat feeds and DNS/IP reputation services into firewalls, SIEMs, and DNS resolvers.
- Monitoring network flow data and DNS traffic for large volumes of outbound queries or connections to numerous IPs in short timeframes.
- Cross-referencing suspicious domains or emails with DNS anomalies.
- Developing organization-specific detection algorithms based on historical DNS behavior and network baselines.
Mitigation strategies recommended by CISA include:
- Using DNS/IP blocklists and firewall rules to block access to Fast Flux infrastructure.
- Employing traffic sinkholing to internal servers for analysis.
- Utilizing reputational scoring for traffic blocking.
- Implementing centralized logging and real-time alerting for DNS anomalies.
- Participating in information-sharing networks.
The widespread use of Fast Flux underscores the need for proactive security measures. Organizations must remain vigilant and adopt the recommended strategies to protect themselves from this sophisticated evasion technique.









