New research reveals alarming connections between the Black Basta and Cactus ransomware groups. Both groups employ similar social engineering techniques and utilize the BackConnect proxy malware for network infiltration.
Understanding the BackConnect Malware
BackConnect Malware acts as a proxy, enabling cybercriminals to mask their activities and escalate attacks within a compromised network undetected. Initially discovered within a Zloader sample, further investigation by Walmart linked it to Qbot (QakBot) malware.
This connection strengthens the existing belief that Zloader, Qbot, and BackConnect are all linked to the Black Basta operation. A BlackBasta data leak further solidified this link by revealing internal conversations between the ransomware gang’s manager and a suspected Qbot developer.
This isn’t the first time Black Basta Ransomware has shown adaptability. Following a 2023 law enforcement operation that disrupted Qbot’s operations, the group shifted to BackConnect, suggesting continued collaboration with developers associated with the Qbot operation.
A recent report from Trend Micro uncovered Cactus ransomware’s use of BackConnect, indicating a possible overlap in group membership.
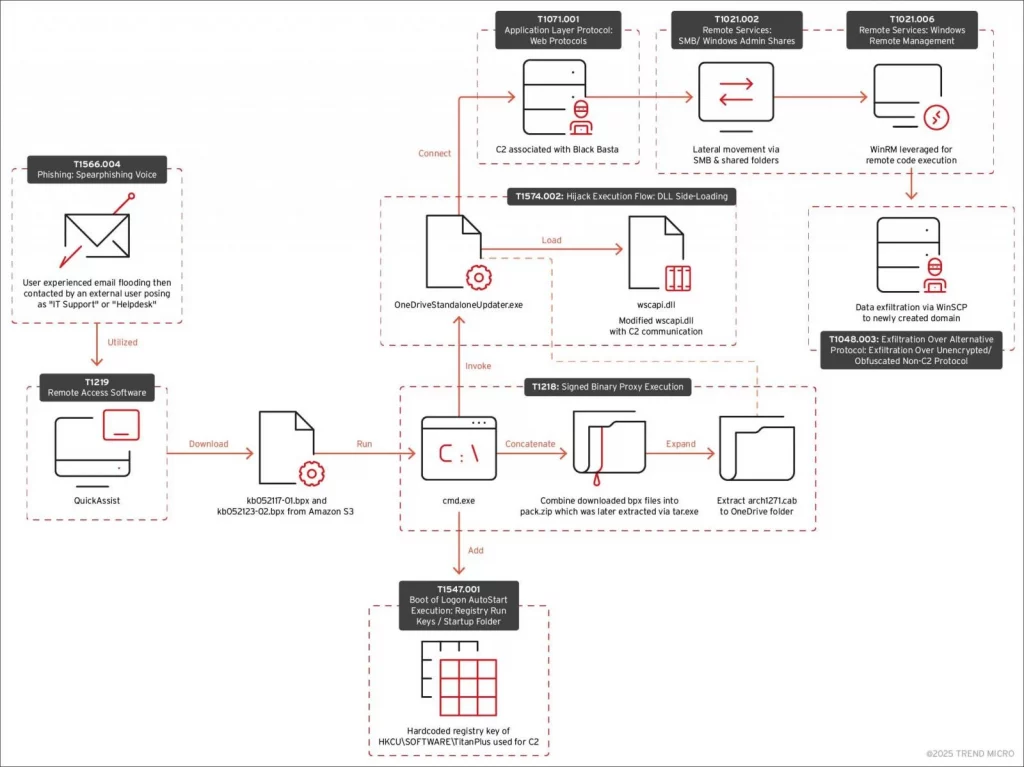
Cactus attack flow
Source: Trend Micro
Shared Social Engineering Tactics and Attack Similarities
The attacks employed by both Black Basta and Cactus Ransomware share striking similarities. Both groups overwhelm targets with emails, a tactic commonly associated with Black Basta.
Subsequently, they impersonate IT help desk employees via Microsoft Teams, tricking victims into granting remote access using Windows Quick Assist. While the attack flows aren’t identical, the similarities, including the use of command and control servers typically linked to Black Basta, are significant.
This underscores the need for robust security awareness training within organizations to mitigate the risk of social engineering attacks. See our article on Phishing Prevention Strategies for more information.
Black Basta’s History and Connections
Black Basta Ransomware, launched in April 2022, is believed to include members of the Conti ransomware gang, which shut down in May 2022 following a major data leak. Historically, Black Basta relied on Qakbot for initial network access.
The shift to BackConnect Malware demonstrates their ability to adapt and find alternative methods to compromise networks. This underscores the importance of proactive security measures and incident response planning.
Implications for Enterprise Businesses
The convergence of tactics and malware between Black Basta and Cactus Ransomware highlights the interconnected nature of ransomware operations. Enterprise businesses must prioritize robust security measures, including multi-layered security solutions, regular security awareness training, and incident response planning.
Understanding these evolving tactics is crucial for effective defense. For organizations with remote workforces, securing remote work environments is paramount for cybersecurity. Read our article on How to Secure Remote Work Environments for best practices.









