South Korean researchers have recently made a discovery regarding the Rhysida ransomware encryptor. They have identified an encryption flaw in the system, which allowed the creation of the Rhysida Ransomware Decryptor. This Rhysida ransomware decryptor can be utilized to recover files affected by the ransomware without any cost.
The Rhysida Ransomware Group
Rhysida is a notorious ransomware operation that emerged in mid-2023. Its primary targets are healthcare organizations, causing disruptions to their vital operations and compromising sensitive patient records.
This criminal group has also been known to target a wide range of industries, including healthcare, military, cultural, and energy organizations. In November 2023, the FBI and CISA issued a warning about the gang’s opportunistic attacks on these various sectors.
A group of South Korean researchers, including experts from the Korean Internet & Security Agency (KISA), conducted a thorough examination of the Rhysida ransomware.
Rhysida Ransomware Encryptor Analysis
Their analysis identified a vulnerability in the ransomware’s encryption system, specifically in the random number generator (CSPRNG) that generates unique private (encryption) keys for each attack.
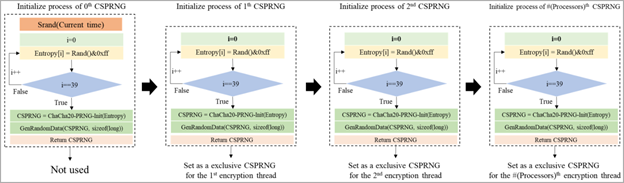
Seeds to generate numbers for each encryption thread (arxiv.org)
By exploiting this flaw, the researchers were able to recover the internal state of the CSPRNG during an attack. This allowed them to generate a valid key to decrypt the encrypted data.
The decryption method was further influenced by Rhysida’s use of intermittent encryption, which means only certain parts of the files were encrypted while others remained in plaintext.
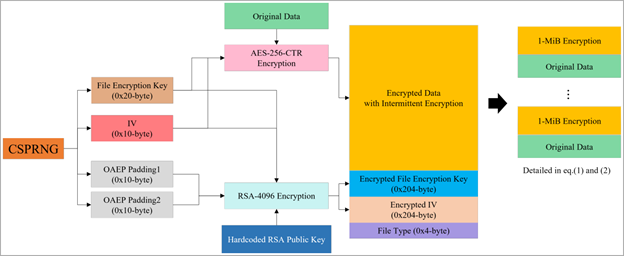
Rhysida’s intermittent encryption process (arxiv.org)
Understanding the encryption pattern and selectively applying the correct key to the affected parts of the files was crucial in developing the decryption process.
Rhysida Ransomware Flawed and Predictable Seed Value and Creation of Rhysida Ransomware Decryptor
The Rhysida ransomware has a flawed value generation system that relies on deriving a 32-bit seed value from the system’s current time. According to the researchers, this limited search space makes it computationally feasible to guess the seed value.
Rhysida utilizes this seed value to generate the private encryption key and initialization vector. However, it lacks other sources of high-entropy data to ensure that the seed value remains unpredictable. This makes it possible to guess the seed value by examining logs or other data that indicate the time of infection.
Based on this understanding, the researchers developed a systematic method to regenerate the state of the CSPRNG. They achieved this by attempting different seed values within the expected range, allowing them to regain control over the encryption process.
Once the researchers discover the correct value (by confirming its ability to decrypt data), they are able to predict all subsequent random numbers used by the ransomware for file encryption. As a result, all locked data can be retrieved without needing the actual private key.
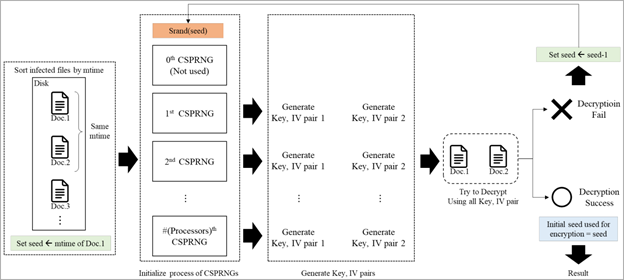
Process of obtaining the correct seed (arxiv.org)
The decryption process involves accurately recreating the same encryption key and initialization vector that were used during the original encryption. By applying a counter-mode (CTR) encryption process to the encrypted segments of the files, the researchers are able to effectively reverse the encryption.
This restores the original plaintext without requiring the attacker’s private key. This method takes advantage of the symmetric property of CTR mode, where the encryption and decryption operations are identical.
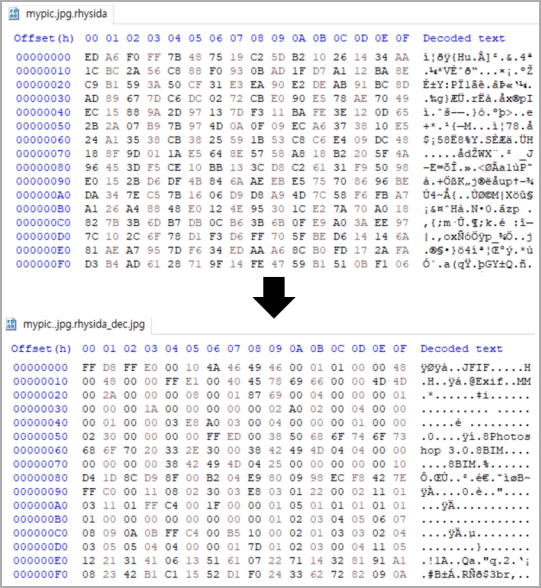
Decrypting an image file for free (arxiv.org)
KISA Website Now Hosts an Automated Rhysida Ransomware Decryptor
KISA’s website now provides an automated decryption tool for Windows, accompanied by a technical paper that was published last Friday. The tool’s usage instructions are available in both Korean and English.
Victims affected by the Rhysida ransomware can utilize this tool in an attempt to decrypt their files without any cost. However, we cannot guarantee the tool’s safety or effectiveness.
According to ransomware expert Fabian Wosar, it is essential to understand that this decryptor exclusively works for files encrypted by the Rhysida Windows encryptor. It is not compatible with decrypting files encrypted on VMware ESXi or through its PowerShell-based encryptor.
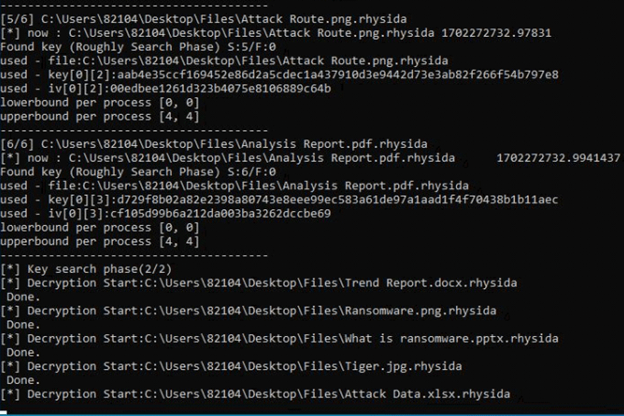
Decryptor running an automated process (KISA)
Rhysida Encryption Vulnerability Exploited for Months
The Rhysida encryption flaw has been privately used for months by cybersecurity firms and governments worldwide since at least May 2023.
“There goes another one. They are obviously not the first one who found this vulnerability,”
“This was independently found by at least three other parties, who chose to circulate it in private instead of seeking publication and alerting Rhysida about their problem.”
“As to who those parties are: Avast found it in October last year, the French CERT authored and published a private paper about it in June, and I found the vulnerability in May last year.”
Explains Wosar in a thread on X
According to Wosar, hundreds of machines with petabytes of data have been successfully decrypted using this flaw since its discovery in May. However, he cautions that now that the flaw has been publicly disclosed, the ransomware operators are likely to fix the bug within days. This means that recovering files without paying a ransom demand may become impossible.
South Korean researchers said that the reason behind publicly disclosing the flaw is that various cybersecurity companies share decryption techniques on platforms like blogs and GitHub, which aids in mitigating the damage caused by ransomware. They said that in collaboration with KISA, they developed the decryption tool and decided to release the research paper to effectively demonstrate its capabilities. Their aim is to contribute to the resilience of ransomware victims by sharing their detailed research.







