A new variant of the StopCrypt ransomware, also known as STOP, has been detected in the wild. This variant utilizes a multi-stage execution process that employs shellcodes to evade security tools.
StopCrypt ransomware, also referred to as STOP Djvu, is a highly prevalent form of ransomware that often goes unnoticed. It is typically distributed through malicious advertising and suspicious websites that offer adware bundles disguised as free software, game cheats, and software cracks.
However, upon installing these programs, users unknowingly expose themselves to a range of malware, including trojans that steal passwords and the STOP ransomware.
As a result, infected users often seek assistance from security researchers, ransomware experts, and our extensive 807-page STOP ransomware forum topic in their desperate attempts to find a solution.
Since its initial release in 2018, the encryption capabilities of the ransomware have remained largely unchanged, with subsequent versions primarily aimed at resolving critical issues.
StopCrypt Ransomware Employs New Multi-Staged Execution
The threat research team at SonicWall has recently discovered a new variant of the STOP ransomware, which they have named StopCrypt. This variant employs a multi-stage execution mechanism to carry out its malicious activities.
In the initial stage, the malware loads a DLL file called msim32.dll, which may serve as a diversionary tactic. Additionally, the malware incorporates time-delaying loops to potentially evade security measures that are time-based.
Furthermore, the malware utilizes dynamically constructed API calls on the stack to allocate memory space with read/write and execution permissions. This technique increases the difficulty of detecting the ransomware.
StopCrypt ransomware leverages API calls for various operations, notably for capturing snapshots of active processes to gain a comprehensive understanding of the operating environment.
In the subsequent stage, it employs process hollowing, a technique that hijacks legitimate processes and discreetly executes its payload in memory.
This intricate process involves a meticulously orchestrated sequence of API calls that manipulate process memory and control flow.
Once the final payload is executed, a series of actions unfold to ensure the ransomware’s persistence. These actions encompass modifying access control lists (ACLs) to prevent users from deleting critical malware files and directories, as well as establishing a scheduled task to execute the payload at five-minute intervals.
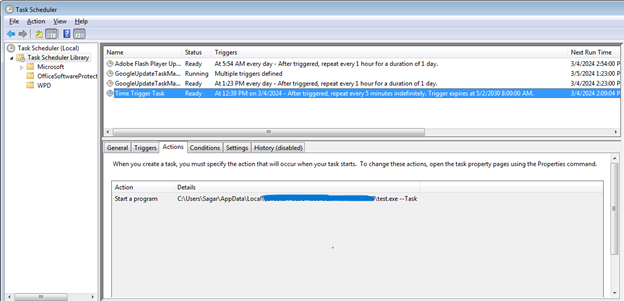
StopCrypt’s scheduled task
Source: (SonicWall)
The ransomware encrypts files and appends a “.msjd” extension to their names. It’s worth noting that the STOP ransomware frequently changes extensions, resulting in hundreds of variations.
Moreover, a ransom note named “_readme.txt” is generated in each affected folder, providing victims with instructions on how to pay the ransom for data recovery.
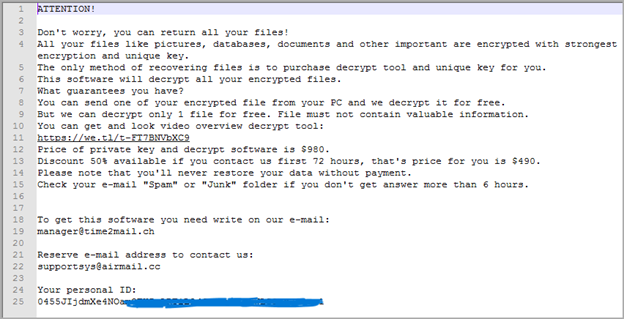
Sample of a ransom note
Source: (Sonic Wall)
The evolution of StopCrypt ransomware into a more sophisticated and potent threat highlights a concerning trend in cybercrime. Although StopCrypt’s ransom demands are not exorbitant, and its operators do not engage in data theft, the potential impact on numerous individuals can be substantial.









