Stanford University has reported a Ransomware attack involving its Department of Public Safety (SUDPS) network. As a result of the Stanford ransomware attack, personal information belonging to approximately 27,000 individuals was compromised.
Stanford Ransomware Attack Compromised PII of 27k Individuals
In a recent update, Stanford University confirmed that the attackers were not able to access any other systems beyond the network of the Department of Public Safety.
This indicates that the impact of the attack was contained within the SUDPS network, preventing further unauthorized access to sensitive information stored in other university systems.
The university became aware of the attack on September 27 and subsequently launched an investigation into the incident.
The investigation is ongoing as the university works to address the incident and strengthen its cybersecurity measures.
According to the data breach notifications submitted to Maine’s Attorney General, the attackers behind the cyber incident targeting Stanford University’s Department of Public Safety (SUDPS) network successfully obtained documents containing personally identifiable information (PII) of approximately 27,000 individuals.
“The investigation determined that an unauthorized individual(s) gained access to the Department of Public Safety’s network between May 12, 2023, and Sept. 27, 2023,”
“The personal information that may have been affected varies from person to person but could include date of birth, Social Security number, government ID, passport number, driver’s license number, and other information the Department of Public Safety may have collected in its operations,”
The university said.
“For a small number of individuals, this information may also have included biometric data, health/medical information, email address with password, username with password, security questions and answers, digital signature, and credit card information with security codes.”
Stanford said in a statement.
Akira Ransomware Has Claimed Responsibility for the Stanford Ransomware Attack
Stanford University has not officially attributed the September cyber incident to a particular ransomware operation.
However, it is worth noting that the Akira ransomware gang claimed responsibility for the attack in October. According to their claims, they managed to exfiltrate approximately 430GB of files from the university’s systems. Subsequently, the cybercrime group made the stolen data available for download via BitTorrent on their dark web leak site.
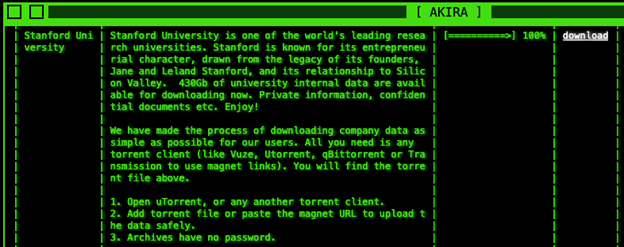
Source: BleepingComputer
The emergence of the Akira ransomware operation in March 2023 marked a concerning development in the cybersecurity landscape. The group gained notoriety by targeting victims from diverse industry sectors.
By June 2023, the Akira ransomware operators expanded their capabilities by developing and deploying a Linux encryptor.
This encryptor specifically targeted VMware ESXi virtual machines, which are widely utilized in enterprise environments.
This move demonstrated the group’s adaptability and willingness to target critical infrastructure and systems commonly employed by organizations.
As per negotiation chats discovered, the ransomware group behind the Akira operation has been demanding significant ransom payments from their victims.
The amount requested varies depending on the size of the breached organization, ranging from $200,000 to millions of dollars. This demonstrates the group’s intention to capitalize on the value of the compromised data.
In addition, Stanford University experienced another data breach in February 2023. This particular breach involved the exposure of Department of Economics Ph.D. program admission information, which occurred between December 2022 and January 2023.
It is unfortunate that the university has faced multiple incidents, including a data breach in April 2021, where documents stolen from Stanford School of Medicine’s Accellion File Transfer Appliance (FTA) platform were leaked by the Clop ransomware group.









