Insomniac Games, a subsidiary of Sony, is taking action after the Rhysida Ransomware Data Breach incident. Following a Rhysida ransomware attack in November, the personal information of some employees was stolen and later leaked online.
Insomniac Games, based in California, is known for its video game development and has been a part of Sony Interactive Entertainment’s Worldwide Studios division (now called PlayStation Studios) since its acquisition by Sony in August 2019.
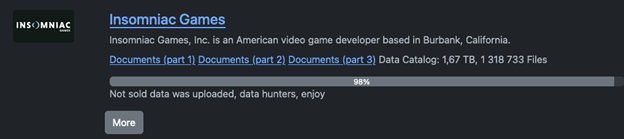
Sony initiated an investigation in December following claims made by the Rhysida ransomware gang. The gang alleged that they successfully breached Insomniac Games and obtained more than 1.3 million files from the company’s network.
Negotiations between the two parties broke down when Insomniac Games refused to pay the demanded $2 million ransom. As a result, Rhysida proceeded to release 1.67 terabytes of documents on their dark web leak site.
“We are saddened and angered about the recent criminal cyberattack on our studio and the emotional toll it’s taken on our dev team,”
The studio said in a statement published on Twitter.
“We are aware that the stolen data includes personal information belonging to our employees, former employees, and independent contractors.”
Insomniac Games Notifies Employees of the Rhysida Ransomware Data Breach
Insomniac Games is currently in the process of notifying employees whose personal data was compromised during the specific period of November 25 to November 26.
The leaked data, which includes ID scans, internal documents such as contract information and licensing agreements with Marvel and Nvidia, and even screenshots of the upcoming Wolverine game, was initially obtained by the Rhysida ransomware group.
According to the group’s claims, they have already released 98% of the stolen files, while the remaining files were sold to the highest bidder. Insomniac Games is taking appropriate measures to inform and support their affected employees.
Insomniac Games, a subsidiary of Sony, is taking action after the Rhysida Ransomware Data Breach incident. Following a Rhysida ransomware attack in November, the personal information of some employees was stolen and later leaked online.
Insomniac Games, based in California, is known for its video game development and has been a part of Sony Interactive Entertainment’s Worldwide Studios division (now called PlayStation Studios) since its acquisition by Sony in August 2019.
Sony initiated an investigation in December following claims made by the Rhysida ransomware gang. The gang alleged that they successfully breached Insomniac Games and obtained more than 1.3 million files from the company’s network.
Negotiations between the two parties broke down when Insomniac Games refused to pay the demanded $2 million ransom. As a result, Rhysida proceeded to release 1.67 terabytes of documents on their dark web leak site.
“We are saddened and angered about the recent criminal cyberattack on our studio and the emotional toll it’s taken on our dev team,”
The studio said in a statement published on Twitter.
“We are aware that the stolen data includes personal information belonging to our employees, former employees, and independent contractors.”
Insomniac Games Notifies Employees of the Rhysida Ransomware Data Breach
Insomniac Games is currently in the process of notifying employees whose personal data was compromised during the specific period of November 25 to November 26.
The leaked data, which includes ID scans, internal documents such as contract information and licensing agreements with Marvel and Nvidia, and even screenshots of the upcoming Wolverine game, was initially obtained by the Rhysida ransomware group.
According to the group’s claims, they have already released 98% of the stolen files, while the remaining files were sold to the highest bidder. Insomniac Games is taking appropriate measures to inform and support their affected employees.
“As you know, we store and maintain files containing employment information, including personal information about you. Unfortunately, these files were downloaded by an unauthorized actor and released online,” the breach notification letter says.
“Once Insomniac identified the downloaded files, we began analyzing the files to determine what types of personal information were affected and to whom it relates. While we worked quickly, this was a time-consuming process, and we wanted to provide you with accurate information.”
Insomniac Games and Sony have decided to provide an extension to the ID Watchdog services that are included in their employee benefits package. This extension entails an additional two years of complimentary credit monitoring and identity restoration, which goes beyond the current enrollment period. This initiative aims to further support and protect the affected employees in light of the data breach incident.
Insomniac Games has established a dedicated call center to address any inquiries or concerns that affected employees may have regarding the ransomware attack that occurred in November. Unfortunately, a Sony spokesperson was not available for immediate comment on the specific details of the data breach, including the number of individuals affected and the specific personal information that was leaked online.
Who Are Behind the Rhysida Ransomware?
The Rhysida ransomware-as-a-service (RaaS) operation first emerged in May 2023 and quickly gained attention after successfully breaching the Chilean Army (Ejército de Chile) and the British Library.
In August, the U.S. Department of Health and Human Services (HHS) identified the Rhysida gang as responsible for numerous attacks on healthcare organizations within the United States. However, a joint advisory from the Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) highlighted that the group is not limited to targeting healthcare alone.
The advisory cautioned that the Rhysida gang conducts opportunistic attacks, targeting organizations across various industry sectors. This serves as a reminder that businesses in multiple sectors should remain vigilant against potential threats from this group.