This Connectwise Screenconnect bug allows them to infiltrate compromised networks and deploy LockBit ransomware payloads. The vulnerability, known as CVE-2024-1709, has been actively targeted since Tuesday, shortly after ConnectWise released security updates and proof-of-concept exploits were made public by various cybersecurity companies. ConnectWise has also addressed another high-severity path traversal vulnerability, CVE-2024-1708, but can only be abused by threat actors with elevated privileges. The identified security vulnerabilities affect all versions of Connectwise Screenconnect ScreenConnect, leading the company to take action on Wednesday. They have removed license restrictions, allowing customers with expired licenses to upgrade to the latest software version and protect their servers from potential LockBit attacks. The severity of CVE-2024-1709 is evident as it is being widely exploited in the wild. According to Shadowserver, a security threat monitoring platform, there are currently 643 IP addresses targeting vulnerable servers. Shodan, a search engine for internet-connected devices, has identified over 8,659 ScreenConnect servers, but only 980 of them are running the patched version, Connectwise ScreenConnect 23.9.8.
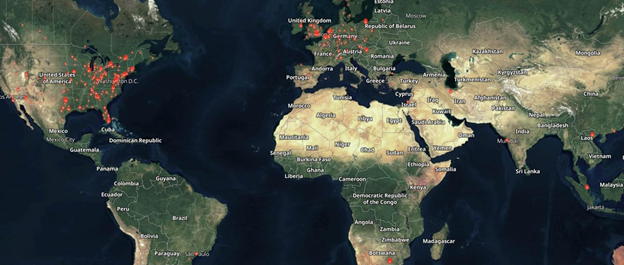
Internet-Exposed ScreenConnect Servers
Source: (Shodan)
Connectwise Screenconnect Bug is Exploited in LockBit Ransomware Attacks
Sophos X-Ops has recently disclosed that malicious actors have been utilizing the identified auth bypass flaws in the Connectwise ScreenConnect to gain unauthorized access to victims’ systems. Once inside, they proceed to deploy LockBit ransomware as their chosen payload.
“In the last 24 hours, we’ve observed several LockBit attacks, apparently after exploitation of the recent ConnectWise ScreenConnect vulnerabilities (CVE-2024-1708 / CVE-2024-1709),”
“Two things of interest here: first, as noted by others, the ScreenConnect vulnerabilities are being actively exploited in the wild. Second, despite the law enforcement operation against LockBit, it seems as though some affiliates are still up and running.”
The Sophos’ threat response task force said.
Huntress, a cybersecurity company, has corroborated the information and discovered that LockBit ransomware attackers have targeted additional organizations.
Among the victims are a local government entity, which includes systems likely associated with their 911 systems, and a healthcare clinic. These attackers exploited the CVE-2024-1709 vulnerabilities to infiltrate the networks of these organizations.
“We can confirm that the malware being deployed is associated with Lockbit,”
“We can’t attribute this directly to the larger LockBit group but it is clear that lockbit has a large reach that spans tooling, various affiliate groups, and offshoots that have not been completely erased even with the major takedown by law enforcement.”
Huntress said in an email.
CISA Adds CVE-2024-1709 to KEV (Known Exploited Vulnerabilities) Catalog
The Cybersecurity and Infrastructure Security Agency (CISA) has recently included CVE-2024-1709 in its Known Exploited Vulnerabilities Catalog. To protect U.S. federal agencies from potential attacks, CISA has mandated that these agencies secure their servers within one week, by February 29.
The vulnerabilities affect ScreenConnect versions 23.9.7 and earlier. CISA has provided the following remediation steps in their advisory to address these issues:
Cloud
No further action is required from the partners. ConnectWise has already taken the necessary steps to address the issue by updating the servers hosted in the “screenconnect.com” cloud and “hostedrmm.com”
On-premise
For partners who are self-hosted or on-premise, it is crucial that they update heir servers to version 23.9.8 immediately in order to apply a necessary patch. This update is essential to ensure the security and stability of servers.
The cybersecurity researchers at Huntress have recently conducted a thorough analysis of the ConnectWise vulnerability. They have observed that this vulnerability is currently being exploited in real-world attacks. In addition, the researchers have successfully replicated the exploit and attack sequence.
Based on their findings, the researchers have determined that this vulnerability can be easily exploited, which is a cause for concern. Consequently, they recommend that specific details about the vulnerability should not be made public until sufficient time has been given for the industry to address and patch the issue.
The researchers believe that making this information readily available to threat actors could pose significant risks.
CISA Orders Immediate Patching of Connectwise Screenconnect Bug as Per (BOD) 22-01
As per Binding Operational Directive (BOD) 22-01, titled “Reducing the Significant Risk of Known Exploited Vulnerabilities,” it is mandatory for FCEB agencies to promptly address the vulnerabilities identified in the catalog. The objective is to safeguard their networks against potential attacks that take advantage of these flaws.
In addition to federal agencies, cybersecurity experts strongly advise private organizations to review the Catalog and take necessary steps to address any vulnerabilities present in their own infrastructure.
To ensure compliance, the Cybersecurity and Infrastructure Security Agency (CISA) has issued an order for federal agencies to rectify these vulnerabilities no later than February 29, 2024.
LockBit Ransomware Dismantled in Operation Cronos
The infrastructure of LockBit ransomware was successfully seized in a recent law enforcement operation called Operation Cronos, led by the U.K.’s National Crime Agency (NCA). As part of this global operation, the dark web leak sites associated with LockBit were taken down on Monday.
In a collaborative effort, the National Police Agency of Japan has developed a decryptor for LockBit 3.0 Black Ransomware. This decryptor utilizes more than 1,000 encryption keys obtained from the seized servers of LockBit. It has been made freely available on the ‘No More Ransom’ portal.
To further combat the activities of the LockBit ransomware gang, the U.S. State Department has announced rewards of up to $15 million for individuals providing information about the members of the gang and their associates.
This initiative aims to encourage the reporting of valuable information that can assist in apprehending those involved in the criminal activities associated with LockBit ransomware.