The U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the FBI and international partners, has issued an updated advisory warning organizations about the evolving threat posed by the Scattered Spider ransomware group. Known for targeting large enterprises across sectors, the group is now employing even more advanced tactics as of June 2025, especially within critical infrastructure and commercial facilities.
This marks the third advisory concerning Scattered Spider since November 2023.
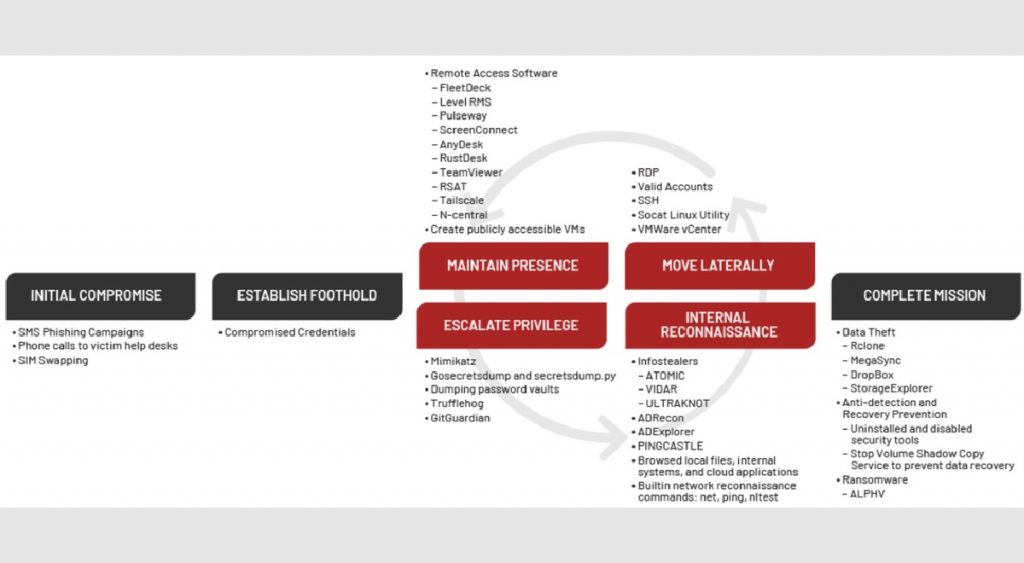
“While some TTPs remain consistent, Scattered Spider threat actors often change TTPs to remain undetected,” the advisory notes.
Who is Scattered Spider and What Makes Them a Critical Threat?
Also known by names such as UNC3944, Octo Tempest, Storm-0875, and Muddled Libra, Scattered Spider primarily targets large organizations using social engineering strategies inspired by phishing. Their victims often include third-party IT help desk providers, which they exploit to gain initial system access.
Their reach spans a wide range of industries including:
- Technology
- Financial services
- Telecommunications
- Retail
- Gaming
- Business process outsourcing (BPO)
- Media & entertainment
- Hospitality
Scattered Spider typically operates in English-speaking countries but has recently expanded attacks to Singapore and India.
Attack Methods: Social Engineering, MFA Bypass, and SIM Swapping
Scattered Spider has introduced new tactics, techniques, and procedures (TTPs) that include:
- Push bombing (MFA fatigue attacks): Victims receive repeated multi-factor authentication requests until they approve one by mistake.
- SIM swapping attacks: The group convinces telecom providers to transfer a victim’s phone number to a SIM card they control. This gives them access to one-time passwords used in 2FA.
- Helpdesk impersonation: Attackers pose as employees to trick IT staff into resetting passwords and reassigning MFA credentials.
The group also gathers employee data using open-source intelligence, including business directories and dark web marketplaces such as Russia Market. Once they gain access, attackers often deploy DragonForce ransomware to exfiltrate and encrypt data, demanding financial extortion from victims.
Targeting Cloud Infrastructure and Communication Platforms
The advisory confirms that Scattered Spider has used Snowflake Cloud accounts to execute mass data exfiltration. Attackers run thousands of queries in short bursts, pulling large volumes of data quickly. In response, Snowflake announced in May that it will enforce mandatory MFA for all password-enabled accounts by August and has already blocked SSO access across all customer accounts.
The group has also searched company communication platforms like Slack, Microsoft Teams, and Exchange Online to monitor internal discussions about incident response and security measures. In some cases, the attackers created fake identities and social media profiles, even joining internal teleconferences to stay ahead of response teams.
“The threat actor joined remediation calls to likely identify how security teams are hunting them and proactively develop new avenues of intrusion,” the FBI noted.
Arrests Made but Threat Remains Active
Authorities have arrested several suspected members of the group in recent months. Four individuals aged between 17 and 22 were arrested in the UK on June 17, while another suspect was detained in Spain earlier this month. Despite these actions, the group continues to operate and adapt.
Defense Recommendations for Enterprises
CISA’s advisory urges businesses to take the following steps to reduce risk:
- Enforce phishing-resistant MFA across all access points
- Regularly test offline backups, stored separately from the main environment
- Deploy application controls to restrict unauthorized software execution
- Educate employees on social engineering risks and report unusual activity immediately
Financial and Operational Impact of Scattered Spider Attacks
According to Mandiant, Scattered Spider’s operations have cost victim organizations hundreds of millions of dollars, both in direct ransom payments and operational downtime.
Notable incidents this year include coordinated attacks on UK retailers like Marks & Spencer, Co-op, and Harrods—breaches reportedly enabled by credentials stolen from IT vendor Tata Consultancy Services.
As the group continues to refine its methods and expand its global footprint, enterprises are being warned to stay vigilant and strengthen their cybersecurity posture.










