Iranian state-sponsored threat actor OilRig, also known as APT34, continued its cyber espionage endeavors throughout 2022, deploying three distinctive downloader malware—ODAgent, OilCheck, and OilBooster. Slovak cybersecurity company ESET unveiled these findings, shedding light on the group’s tactics, techniques, and procedures.
Using Legitimate Cloud Service for C2 Communications and Data Exfiltration
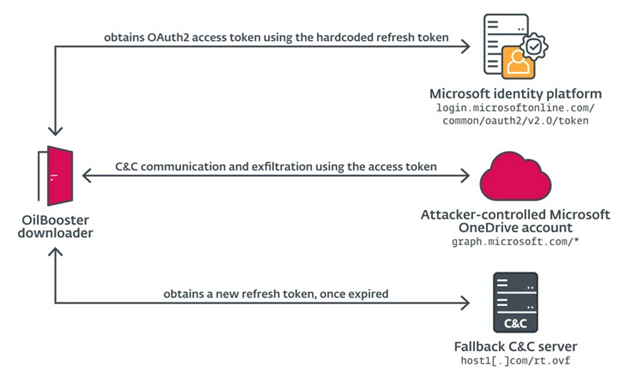
These newly identified downloaders exhibited a unique strategy by utilizing legitimate cloud service APIs for command-and-control communication and data exfiltration. Notably, Microsoft Graph OneDrive and Outlook APIs, alongside the Microsoft Office Exchange Web Services (EWS) API, were leveraged.
This approach allows OilRig to camouflage its activities within genuine network traffic, evading detection and maintaining the secrecy of its attack infrastructure.
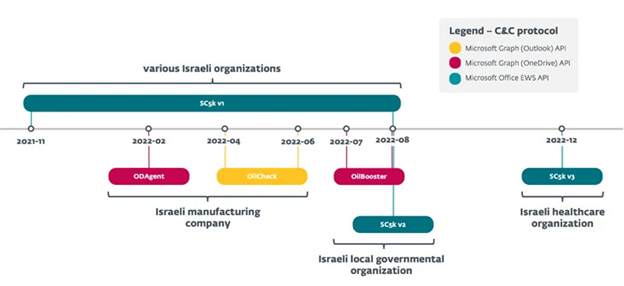
OilRig’s targets in this campaign encompassed various sectors, including healthcare, manufacturing, and local government organizations. Notably, all victims had previously encountered the threat actor. The exact initial access vector remains unclear.
The Downloader Profiles
ODAgent: A C#/.NET downloader discovered in February 2022. It employs the Microsoft OneDrive API for command-and-control communication, allowing the threat actor to download and execute payloads while exfiltrating staged files.
SampleCheck5000: An updated version of a known OilRig downloader. It interacts with a shared Microsoft Exchange mail account, using the Office Exchange Web Services (EWS) API to download and execute additional OilRig tools.
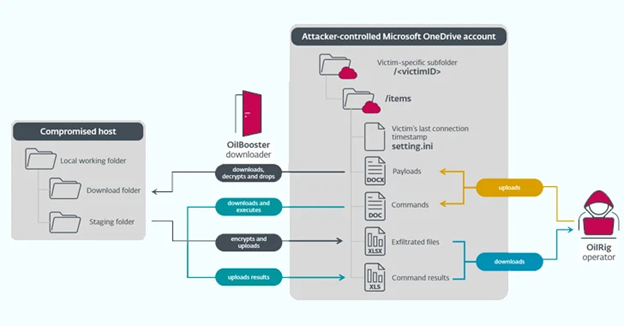
OilBooster: Similar to ODAgent, it uses the Microsoft OneDrive API for command-and-control. OilBooster, however, differs by connecting to a Microsoft Office 365 account via the Microsoft Graph API to fetch commands and payloads from victim-specific folders.