Australia is facing a surge in data breaches, with the number of reported incidents reaching a three-year high in the 2022-23 financial year. The Office of the Australian Information Commissioner (OAIC) has released its annual report, revealing a concerning trend that highlights the growing vulnerability of individuals and organizations to cyberattacks.
A Significant Increase in Reported Breaches:
The report highlights a stark increase in data breaches, with a total of 1,278 incidents reported, a 13% jump from the previous year. This marks the highest number of breaches reported since the 2019-20 financial year. While the OAIC acknowledges that this increase could be attributed to heightened awareness and improved reporting mechanisms, the underlying reality remains alarming.
The report reveals that malicious and criminal attacks are the most common type of data breach (67%), with the majority (57%) consisting of cybersecurity incidents. This highlights the sophisticated and organized nature of the threat.
The Impact of Data Breaches:
The consequences of data breaches extend far beyond mere inconvenience. The loss of sensitive personal information, including names, addresses, financial details, and even health records, can have devastating effects on individuals. Victims often face identity theft, financial fraud, and reputational damage.
The report reveals a diverse range of data breach incidents, with malicious cyberattacks topping the list. These attacks often involve sophisticated techniques like ransomware, phishing, and malware, targeting organizations and individuals alike.
The MediSecure Breach: A Wake-Up Call:
The report highlights a particularly alarming incident: the April 2024 breach of electronic prescription provider MediSecure, which affected an estimated 12.9 million Australians. This is the largest number of Australians impacted by a single cybersecurity breach since the Notifiable Data Breaches scheme began in 2018.
Sectors Most Affected:
The health sector has been particularly vulnerable, recording the highest number of data breaches during the reporting period (102). Other sectors significantly affected include the Australian Government (63), finance (58), education (44), and retail (29).
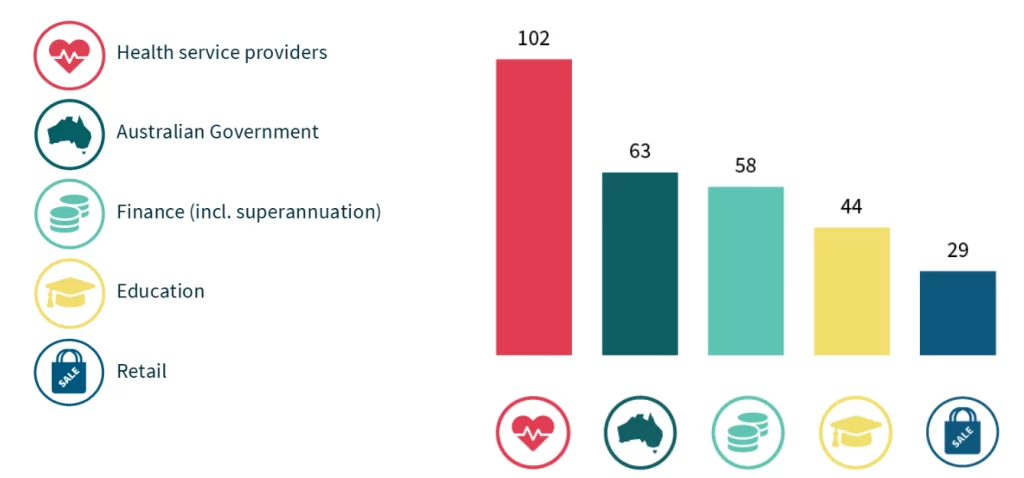
Source: Office of the Australian Information Commissioner
The Role of Human Error:
While malicious actors pose a significant threat, the report also highlights the role of human error in contributing to data breaches. Accidental disclosure of sensitive information, unauthorized access, and inadequate security measures can all lead to data leaks.
The Expert Perspective:
Professor Nigel Phair, from the Department of Software Systems and Cybersecurity at Monash University, emphasizes the growing concern about data breaches among Australian businesses.
“Cyber criminals constantly adapt their methods to steal customer data from a wide range of Australian organisations and subsequently monetise that theft.” He states,
He also highlights the challenge of accurately assessing the extent of the problem due to reliance on voluntary reporting and predicts that the number of breaches will continue to grow.
The Need for Enhanced Security Measures:
The OAIC emphasizes the need for organizations to implement robust security measures to protect sensitive data. This includes:
- Stronger password policies and multi-factor authentication: Encouraging the use of complex passwords and requiring multiple authentication factors can significantly reduce the risk of unauthorized access.
- Regular security audits and vulnerability assessments: Proactive identification and remediation of security vulnerabilities are crucial to prevent breaches.
- Employee training and awareness programs: Educating employees about cybersecurity threats and best practices can minimize the risk of human error.
- Data encryption and secure data storage: Encrypting sensitive data at rest and in transit can protect it from unauthorized access even if a breach occurs.
- Incident response plans: Having a well-defined plan for responding to data breaches is essential to minimize damage and ensure swift recovery.
The OAIC’s Call to Action:
The OAIC urges organizations to take proactive steps to enhance their cybersecurity posture and protect the privacy of individuals.
“The increasing number of data breaches reported to the OAIC is a cause for concern. It highlights the need for organizations to take proactive steps to enhance their cybersecurity posture and protect the privacy of individuals.” The report states,
They emphasize the importance of:
- Adopting a risk-based approach to data security: Organizations should prioritize the protection of sensitive data and implement appropriate security measures based on the level of risk.
- Promoting a culture of data security: Fostering a culture of data security within organizations is crucial to ensure that all employees understand their responsibilities and actively contribute to protecting sensitive information.
- Collaborating with industry partners and government agencies: Sharing best practices and collaborating with other organizations and government agencies can help strengthen cybersecurity defenses across the board.
The Future of Data Security:
The surge in data breaches highlights the growing importance of data security in today’s digital world. As technology advances and cyberattacks become more sophisticated, organizations and individuals must remain vigilant and adapt their security measures accordingly. The OAIC’s report serves as a stark reminder of the need for proactive measures to protect sensitive data and safeguard the privacy of individuals.